Latest YouTube Video
Saturday, September 5, 2015
Brazil scores early, beat Costa Rica 1-0
from FOX Sports Digital http://ift.tt/1Uzk3Pm
via IFTTT
Over 80,000 fans turn up for Dede's Dortmund testimonial
from FOX Sports Digital http://ift.tt/1O4U56i
via IFTTT
Spain beats Slovakia 2-0 to tighten race in Euro qualifying
from FOX Sports Digital http://ift.tt/1QgH3Sz
via IFTTT
Orioles Video: Mike Wright surrenders long HR to Jose Bautista in 5-1 loss to AL East-leading Blue Jays; lost 14 of 17 (ESPN)
via IFTTT
South Sudan gets 1st competitive win, Ghana edges Rwanda
from FOX Sports Digital http://ift.tt/1JKl6Je
via IFTTT
England qualifies for Euro 2016, Rooney ties scoring record
from FOX Sports Digital http://ift.tt/1JX04Za
via IFTTT
Resurgent Russia beats Sweden in Euro 2016 qualifying
from FOX Sports Digital http://ift.tt/1JX04Ze
via IFTTT
10-Year-Old With Rare Disease Shamed by Anonymous Note Left on Car
from Google Alert - anonymous http://ift.tt/1PSzDEg
via IFTTT
Ryan Foerster
from Google Alert - anonymous http://ift.tt/1PSndfD
via IFTTT
Madrid donates 1 million euros to refugees
from FOX Sports Digital http://ift.tt/1JJkIdV
via IFTTT
Q&A with Nightline Adviser (anonymous)
from Google Alert - anonymous http://ift.tt/1Fp7IGz
via IFTTT
Apple to Built Fuel Cell Battery that Could Power iPhones and Macbooks for Weeks
from The Hacker News http://ift.tt/1N9bH0d
via IFTTT
Fekir faces long spell out after rupturing knee ligaments
from FOX Sports Digital http://ift.tt/1UtcaQO
via IFTTT
Anonymous donor pledges $500000 in a matching gift challenge for the Dream Center
from Google Alert - anonymous http://ift.tt/1hJUXAA
via IFTTT
Anonymous on Twitter: "MEDIA ALERT: Dec. 8, 2015, Nashville, Matt DeHart's trial begins. | https://t ...
from Google Alert - anonymous https://www.google.com/url?rct=j&sa=t&url=https://twitter.com/YourAnonNews/status/639492490605789185&ct=ga&cd=CAIyGjgxMzAxNTQ0ZWE3M2NhMmQ6Y29tOmVuOlVT&usg=AFQjCNGo3DBnLEVfYgP45c5-Nykp1oZUAA
via IFTTT
Milky Way with Airglow Australis

Mexico salvages 3-3 tie with Trinidad and Tobago
from FOX Sports Digital http://ift.tt/1M11y7b
via IFTTT
Friday, September 4, 2015
Messi scores twice, Argentina beats Bolivia 7-0
from FOX Sports Digital http://ift.tt/1UsJSWA
via IFTTT
Orioles Highlight: Chris Davis hits 39th and 40th HRs, Matt Wieters and Adam Jones also homer in 10-2 rout of Blue Jays (ESPN)
via IFTTT
Altidore scores twice as US comes back to beat Peru 2-1
from FOX Sports Digital http://ift.tt/1KQT9l8
via IFTTT
Altidore scores twice as US rallies to beat Peru 2-1
from FOX Sports Digital http://ift.tt/1NguxnJ
via IFTTT
FFA aware of security situation ahead of World Cup match
from FOX Sports Digital http://ift.tt/1hIMBJy
via IFTTT
Jermaine Jones makes 1st US start since February
from FOX Sports Digital http://ift.tt/1JUPamR
via IFTTT
Germany moves top of Euro 2016 qualifying group
from FOX Sports Digital http://ift.tt/1FomnSf
via IFTTT
Hungary, Romania draw 0-0 in Euro 2016 qualifier
from FOX Sports Digital http://ift.tt/1EGfrFg
via IFTTT
Denmark, Albania draw 0-0 in European qualifier
from FOX Sports Digital http://ift.tt/1imn09Z
via IFTTT
France beats Portugal 1-0 in friendly; Martial makes debut
from FOX Sports Digital http://ift.tt/1VDLWYZ
via IFTTT
Goetze leads Germany to 3-1 win over Poland and top spot
from FOX Sports Digital http://ift.tt/1JUruyY
via IFTTT
Robben out for 4 weeks with groin injury
from FOX Sports Digital http://ift.tt/1EFxqv6
via IFTTT
Italy's Serie B to introduce green cards for fair play
from FOX Sports Digital http://ift.tt/1ilUmpv
via IFTTT
Porto wants Champions League donations to migrants
from FOX Sports Digital http://ift.tt/1VD6eBI
via IFTTT
Rubin Kazan to fire coach after poor start to Russian league
from FOX Sports Digital http://ift.tt/1NRMlWd
via IFTTT
St. Pauli to play Dortmund with motto 'Refugees Welcome'
from FOX Sports Digital http://ift.tt/1KPfAXX
via IFTTT
Chinese energy firm acquires majority stake in Slavia Prague
from FOX Sports Digital http://ift.tt/1JH4DWm
via IFTTT
Bayern midfielder Javi Martinez supporting migrants
from FOX Sports Digital http://ift.tt/1fZ4O4h
via IFTTT
ISS Daily Summary Report – 09/3/15
from ISS On-Orbit Status Report http://ift.tt/1JGWZes
via IFTTT
Twitter Open Sources 'Diffy' that Automatically Catches Potential Bugs in Code
from The Hacker News http://ift.tt/1JGQE2L
via IFTTT
How to Fix Chrome Massive Memory Usage? Simply Try 'Chrome 45' for Faster Performance
from The Hacker News http://ift.tt/1JSZewH
via IFTTT
Caution! Hackers Can Easily Hijack Popular Baby Monitors to Watch Your Kids
from The Hacker News http://ift.tt/1EFaGvR
via IFTTT
Buy Safe and Secure VPN
from Google Alert - anonymous http://ift.tt/1L96IIn
via IFTTT
MAVEN Stellar Occultation Atmospheric Coverage
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/1IO2HqZ
via IFTTT
Meet World's Fastest Wi-Fi Router (Looks Like an Alien)
from The Hacker News http://ift.tt/1NejpYD
via IFTTT
New Rules Require FBI to Get Warrant for Spying With ‘Stingrays’ Cell Phone Trackers
from The Hacker News http://ift.tt/1FmY6Mp
via IFTTT
Arp 159 and NGC 4725

Anonymous on Twitter: "New #Anonymous video: http://ift.tt/1OfpDo5;
from Google Alert - anonymous https://www.google.com/url?rct=j&sa=t&url=https://twitter.com/YourAnonNews/status/639166072495718400/photo/1&ct=ga&cd=CAIyGjgxMzAxNTQ0ZWE3M2NhMmQ6Y29tOmVuOlVT&usg=AFQjCNGCk2CKuaw071sYMN8KMxqCrciOfg
via IFTTT
Thursday, September 3, 2015
Meeting Directory
from Google Alert - anonymous http://ift.tt/1NdPT5d
via IFTTT
Ravens: WR Marlon Brown (3 catches for 64 yards) resurfaced in preseason finale, writes Jamison Hensley (ESPN)
via IFTTT
Generating Weather Forecast Texts with Case Based Reasoning. (arXiv:1509.01023v1 [cs.AI])
Several techniques have been used to generate weather forecast texts. In this paper, case based reasoning (CBR) is proposed for weather forecast text generation because similar weather conditions occur over time and should have similar forecast texts. CBR-METEO, a system for generating weather forecast texts was developed using a generic framework (jCOLIBRI) which provides modules for the standard components of the CBR architecture. The advantage in a CBR approach is that systems can be built in minimal time with far less human effort after initial consultation with experts. The approach depends heavily on the goodness of the retrieval and revision components of the CBR process. We evaluated CBRMETEO with NIST, an automated metric which has been shown to correlate well with human judgements for this domain. The system shows comparable performance with other NLG systems that perform the same task.
from cs.AI updates on arXiv.org http://ift.tt/1XmR0CO
via IFTTT
Building a Truly Distributed Constraint Solver with JADE. (arXiv:1509.01040v1 [cs.AI])
Real life problems such as scheduling meeting between people at different locations can be modelled as distributed Constraint Satisfaction Problems (CSPs). Suitable and satisfactory solutions can then be found using constraint satisfaction algorithms which can be exhaustive (backtracking) or otherwise (local search). However, most research in this area tested their algorithms by simulation on a single PC with a single program entry point. The main contribution of our work is the design and implementation of a truly distributed constraint solver based on a local search algorithm using Java Agent DEvelopment framework (JADE) to enable communication between agents on different machines. Particularly, we discuss design and implementation issues related to truly distributed constraint solver which might not be critical when simulated on a single machine. Evaluation results indicate that our truly distributed constraint solver works well within the observed limitations when tested with various distributed CSPs. Our application can also incorporate any constraint solving algorithm with little modifications.
from cs.AI updates on arXiv.org http://ift.tt/1XmR0mi
via IFTTT
Semi-described and semi-supervised learning with Gaussian processes. (arXiv:1509.01168v1 [stat.ML])
Propagating input uncertainty through non-linear Gaussian process (GP) mappings is intractable. This hinders the task of training GPs using uncertain and partially observed inputs. In this paper we refer to this task as "semi-described learning". We then introduce a GP framework that solves both, the semi-described and the semi-supervised learning problems (where missing values occur in the outputs). Auto-regressive state space simulation is also recognised as a special case of semi-described learning. To achieve our goal we develop variational methods for handling semi-described inputs in GPs, and couple them with algorithms that allow for imputing the missing values while treating the uncertainty in a principled, Bayesian manner. Extensive experiments on simulated and real-world data study the problems of iterative forecasting and regression/classification with missing values. The results suggest that the principled propagation of uncertainty stemming from our framework can significantly improve performance in these tasks.
from cs.AI updates on arXiv.org http://ift.tt/1POCo9y
via IFTTT
For US, roster spots up for grabs in Friday match vs Peru
from FOX Sports Digital http://ift.tt/1VAkz1O
via IFTTT
Pelle leads Italy to 1-0 win over Malta again in qualifying
from FOX Sports Digital http://ift.tt/1QbEKQI
via IFTTT
Iceland beats Netherlands 1-0 in Euro 2016 qualifier
from FOX Sports Digital http://ift.tt/1O0Mq9a
via IFTTT
Bale powers Wales closer to 1st tournament in 58 years
from FOX Sports Digital http://ift.tt/1Oe3hmW
via IFTTT
Italy-Malta match to observe minute's silence for migrants
from FOX Sports Digital http://ift.tt/1hDKOpe
via IFTTT
Villas-Boas banned 6 games in Russia for striking official
from FOX Sports Digital http://ift.tt/1JEb788
via IFTTT
German soccer clubs, fans rush to support migrants
from FOX Sports Digital http://ift.tt/1KMeMmy
via IFTTT
New Pics Added to the Blog Gallery (September 3, 2015)
New Pics Added to the Blog Gallery! (September 3, 2015)
Click link below to visit gallery now!
http://ift.tt/1HAGoHC
from The 'hotspot' for all things Bob Ross. http://ift.tt/1KLTC80
via IFTTT
Arsenal striker Danny Welbeck has surgery on left knee
from FOX Sports Digital http://ift.tt/1hCWecJ
via IFTTT
Bayern Munich sets up training camp for refugee children
from FOX Sports Digital http://ift.tt/1hWUdsL
via IFTTT
Violin Concerto in D major, S-Skma (Anonymous)
from Google Alert - anonymous http://ift.tt/1hWU8oI
via IFTTT
Salve Jesu sancte sponse (Anonymous)
from Google Alert - anonymous http://ift.tt/1Ocffxd
via IFTTT
ISS Daily Summary Report – 09/2/15
from ISS On-Orbit Status Report http://ift.tt/1JAWbWr
via IFTTT
Popular Belkin Wi-Fi Routers vulnerable to Hackers
from The Hacker News http://ift.tt/1Oc8age
via IFTTT
26 Android Phone Models Shipped with Pre-Installed Spyware
from The Hacker News http://ift.tt/1LWRmwn
via IFTTT
Derby's American owners sell to 'Candy Crush' entrepreneur
from FOX Sports Digital http://ift.tt/1VyGlTu
via IFTTT
Using Android 'AppLock' to Protect Your Privacy? — It's Useless
from The Hacker News http://ift.tt/1hWsA2S
via IFTTT
Toure missing as Ivory Coast launches African title defense
from FOX Sports Digital http://ift.tt/1NOYmMb
via IFTTT
American owners of English football club Derby sell up
from FOX Sports Digital http://ift.tt/1EDbdhP
via IFTTT
Germany midfielder Marco Reus breaks toe in left foot
from FOX Sports Digital http://ift.tt/1LMSgsv
via IFTTT
Critical OS X Flaw Grants Mac Keychain Access to Malware
from The Hacker News http://ift.tt/1NbWgpA
via IFTTT
Chile rises in top 10 of FIFA rankings led by Argentina
from FOX Sports Digital http://ift.tt/1KKNPjh
via IFTTT
FIFA World Rankings List
from FOX Sports Digital http://ift.tt/1ijHeRI
via IFTTT
Soccer players suspended for game after blackface incident
from FOX Sports Digital http://ift.tt/1JAmSue
via IFTTT
Violin Concerto in G minor, S-Skma (Anonymous)
from Google Alert - anonymous http://ift.tt/1UouA56
via IFTTT
September 27, 2015 Total Lunar Eclipse: View from the Moon
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/1JOfO0y
via IFTTT
[FD] Stored XSS in Watu PRO Play allows unauthenticated attackers to do almost anything an admin can (WordPress plugin)
Source: Gmail -> IFTTT-> Blogger
[FD] CSRF in Watu PRO allows unauthenticated attackers to delete quizzes (WordPress plugin)
Source: Gmail -> IFTTT-> Blogger
[FD] Stored XSS in Watu PRO allows unauthenticated attackers to do almost anything an admin can (WordPress plugin)
Source: Gmail -> IFTTT-> Blogger
[FD] PacSec (Tokyo Nov 11-12): PWN2OWN Mobile first casualty of Wassenaar, CFP extended to Friday September 4
Source: Gmail -> IFTTT-> Blogger
[FD] Serendipity 2.0.1 - Blind SQL Injection
Source: Gmail -> IFTTT-> Blogger
[FD] Serendipity 2.0.1 - Persistent XSS
Source: Gmail -> IFTTT-> Blogger
[FD] Serendipity 2.0.1 - Code Execution
[FD] NibbleBlog 4.0.3 - Code Execution - Not fixed
Source: Gmail -> IFTTT-> Blogger
[FD] NibbleBlog 4.0.3 - CSRF - Not fixed
Source: Gmail -> IFTTT-> Blogger
Chung says AFC broke election rules ahead of FIFA vote
from FOX Sports Digital http://ift.tt/1LWh8Rk
via IFTTT
The Flare and the Galaxy

Violin Concerto in B-flat major, S-Skma (2) (Anonymous)
from Google Alert - anonymous http://ift.tt/1NOyvDU
via IFTTT
Wednesday, September 2, 2015
Orioles Highlight: Steve Pearce spectacular catch, Chris Davis 2 HRs, including massive walk-off blast in win vs. Rays (ESPN)
via IFTTT
Heu mihi Domine (Anonymous)
from Google Alert - anonymous http://ift.tt/1KsMUW0
via IFTTT
College soccer players suspended after blackface incident
from FOX Sports Digital http://ift.tt/1KsGqGG
via IFTTT
Trio Sonata in D major, S-Skma (Anonymous)
from Google Alert - anonymous http://ift.tt/1KJLll2
via IFTTT
Turing's Imitation Game has been Improved. (arXiv:1509.00584v1 [cs.AI])
Using the recently introduced universal computing model, called orchestrated machine, that represents computations in a dissipative environment, we consider a new kind of interpretation of Turing's Imitation Game. In addition we raise the question whether the intelligence may show fractal properties. Then we sketch a vision of what robotic cars are going to do in the future. Finally we give the specification of an artificial life game based on the concept of orchestrated machines. The purpose of this paper is to start the search for possible relationships between these different topics.
from cs.AI updates on arXiv.org http://ift.tt/1KsxH7h
via IFTTT
A Neural Attention Model for Abstractive Sentence Summarization. (arXiv:1509.00685v1 [cs.CL])
Summarization based on text extraction is inherently limited, but generation-style abstractive methods have proven challenging to build. In this work, we propose a fully data-driven approach to abstractive sentence summarization. Our method utilizes a local attention-based model that generates each word of the summary conditioned on the input sentence. While the model is structurally simple, it can easily be trained end-to-end and scales to a large amount of training data. The model shows significant performance gains on the DUC-2004 shared task compared with several strong baselines.
from cs.AI updates on arXiv.org http://ift.tt/1LM9FRX
via IFTTT
A Fuzzy Approach for Feature Evaluation and Dimensionality Reduction to Improve the Quality of Web Usage Mining Results. (arXiv:1509.00690v1 [cs.DB])
Web Usage Mining is the application of data mining techniques to web usage log repositories in order to discover the usage patterns that can be used to analyze the users navigational behavior. During the preprocessing stage, raw web log data is transformed into a set of user profiles. Each user profile captures a set of URLs representing a user session. Clustering can be applied to this sessionized data in order to capture similar interests and trends among users navigational patterns. Since the sessionized data may contain thousands of user sessions and each user session may consist of hundreds of URL accesses, dimensionality reduction is achieved by eliminating the low support URLs. Very small sessions are also removed in order to filter out the noise from the data. But direct elimination of low support URLs and small sized sessions may results in loss of a significant amount of information especially when the count of low support URLs and small sessions is large. We propose a fuzzy solution to deal with this problem by assigning weights to URLs and user sessions based on a fuzzy membership function. After assigning the weights we apply a Fuzzy c-Mean Clustering algorithm to discover the clusters of user profiles. In this paper, we describe our fuzzy set theoretic approach to perform feature selection (or dimensionality reduction) and session weight assignment. Finally we compare our soft computing based approach of dimensionality reduction with the traditional approach of direct elimination of small sessions and low support count URLs. Our results show that fuzzy feature evaluation and dimensionality reduction results in better performance and validity indices for the discovered clusters.
from cs.AI updates on arXiv.org http://ift.tt/1KsxFwg
via IFTTT
What to talk about and how? Selective Generation using LSTMs with Coarse-to-Fine Alignment. (arXiv:1509.00838v1 [cs.CL])
We present an end-to-end, domain-independent neural encoder-aligner-decoder model for selective generation, i.e., the joint task of content selection and surface realization. Our model first encodes the full set of over-determined database event records (e.g., in weather forecasting and sportscasting) via a memory-based recurrent neural network (LSTM), then utilizes a novel coarse-to-fine (hierarchical), multi-input aligner to identify the small subset of salient records to talk about, and finally employs a decoder to generate free-form descriptions of the aligned, selected records. Our model achieves up to 54% relative improvement over the current state-of-the-art on the benchmark WeatherGov dataset, despite using no specialized features or resources. Using a simple k-nearest neighbor beam helps further. Finally, we also demonstrate the generalizability of our method on the RoboCup dataset, where it gets results that are competitive with state-of-the-art, despite being severely data-starved.
from cs.AI updates on arXiv.org http://ift.tt/1LM9FRU
via IFTTT
Class-Anonymous-0.02
from Google Alert - anonymous http://ift.tt/1ILtGU2
via IFTTT
Class-Anonymous-0.01
from Google Alert - anonymous http://ift.tt/1L6sAUV
via IFTTT
Anonymous donor delivers check for $30000
from Google Alert - anonymous http://ift.tt/1hV2Nbe
via IFTTT
England a magnet for players as clubs flex financial muscle
from FOX Sports Digital http://ift.tt/1KJd1Xg
via IFTTT
After hiatus, Tim Howard won't be US starter vs Mexico
from FOX Sports Digital http://ift.tt/1NYvn7O
via IFTTT
Dortmund's Grosskreutz heads to Galatasaray but can't play
from FOX Sports Digital http://ift.tt/1LLFp9Z
via IFTTT
French amateur club hits jackpot with Martial move to United
from FOX Sports Digital http://ift.tt/1hz8cnA
via IFTTT
Carrard panel starts reform work for crisis-hit FIFA
from FOX Sports Digital http://ift.tt/1NY95CW
via IFTTT
Take the Bob Ross Quiz (September 2015)
Test your knowledge of the Bob Ross TV show, painting techniques and general Bob Ross trivia!
from The 'hotspot' for all things Bob Ross. http://ift.tt/1O92zaz
via IFTTT
Bob’s Tips & Tricks (September 2015)
Bob’s Tips & Tricks (September 2015)
Click inside the box below to enlarge.
from The 'hotspot' for all things Bob Ross. http://ift.tt/1KIe61G
via IFTTT
Berbatov signs with Greek club PAOK Thessaloniki
from FOX Sports Digital http://ift.tt/1O8nn1N
via IFTTT
ISS Daily Summary Report – 09/1/15
from ISS On-Orbit Status Report http://ift.tt/1KHFdtv
via IFTTT
Government minister takes over Russian football
from FOX Sports Digital http://ift.tt/1JxRnB5
via IFTTT
Ex-Nigeria player Odegbami wants to run for FIFA president
from FOX Sports Digital http://ift.tt/1fUQeLl
via IFTTT
[FD] PayPal Inc - Security Approval & 2FA Account Auth Bypass Session Vulnerability
Source: Gmail -> IFTTT-> Blogger
FBI’s Cyber Task Force Identifies Stealthy FF-RATs used in Cyber Attack
from The Hacker News http://ift.tt/1JxMszT
via IFTTT
France to face Russia at Stade de France in March
from FOX Sports Digital http://ift.tt/1NMZr79
via IFTTT
How to add Team Calendars with anonymous access in the Dashboard
from Google Alert - anonymous http://ift.tt/1ihxqrx
via IFTTT
Distant Neutrinos Detected Below Antarctic Ice
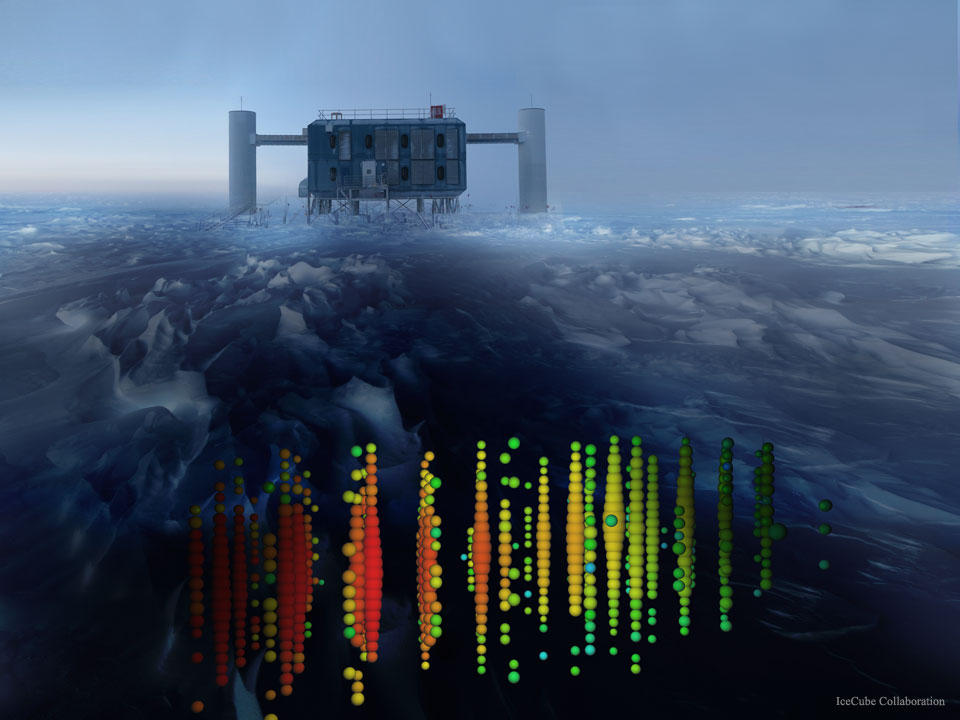
Tuesday, September 1, 2015
Orioles Video: Cal Ripken Jr. honored on 20th anniversary of breaking Lou Gehrig's record prior to 11-2 loss to Rays (ESPN)
via IFTTT
No pressure for Japan coach ahead of World Cup qualifiers
from FOX Sports Digital http://ift.tt/1N8Nhp3
via IFTTT
Australia coach retracts comments over football pay dispute
from FOX Sports Digital http://ift.tt/1JAeux4
via IFTTT
Value function approximation via low-rank models. (arXiv:1509.00061v1 [cs.LG])
We propose a novel value function approximation technique for Markov decision processes. We consider the problem of compactly representing the state-action value function using a low-rank and sparse matrix model. The problem is to decompose a matrix that encodes the true value function into low-rank and sparse components, and we achieve this using Robust Principal Component Analysis (PCA). Under minimal assumptions, this Robust PCA problem can be solved exactly via the Principal Component Pursuit convex optimization problem. We experiment the procedure on several examples and demonstrate that our method yields approximations essentially identical to the true function.
from cs.AI updates on arXiv.org http://ift.tt/1FiiVso
via IFTTT
GR2RSS: Publishing Linked Open Commerce Data as RSS and Atom Feeds. (arXiv:1509.00190v1 [cs.IR])
The integration of Linked Open Data (LOD) content in Web pages is a challenging and sometimes tedious task for Web developers. At the same moment, most software packages for blogs, content management systems (CMS), and shop applications support the consumption of feed formats, namely RSS and Atom. In this technical report, we demonstrate an on-line tool that fetches e-commerce data from a SPARQL endpoint and syndicates obtained results as RSS or Atom feeds. Our approach combines (1) the popularity and broad tooling support of existing feed formats, (2) the precision of queries against structured data built upon common Web vocabularies like schema.org, GoodRelations, FOAF, VCard, and WGS 84, and (3) the ease of integrating content from a large number of Web sites and other data sources in RDF in general.
from cs.AI updates on arXiv.org http://ift.tt/1PKcmUO
via IFTTT
Partial Sum Minimization of Singular Values in Robust PCA: Algorithm and Applications. (arXiv:1503.01444v2 [cs.CV] CROSS LISTED)
Robust Principal Component Analysis (RPCA) via rank minimization is a powerful tool for recovering underlying low-rank structure of clean data corrupted with sparse noise/outliers. In many low-level vision problems, not only it is known that the underlying structure of clean data is low-rank, but the exact rank of clean data is also known. Yet, when applying conventional rank minimization for those problems, the objective function is formulated in a way that does not fully utilize a priori target rank information about the problems. This observation motivates us to investigate whether there is a better alternative solution when using rank minimization. In this paper, instead of minimizing the nuclear norm, we propose to minimize the partial sum of singular values, which implicitly encourages the target rank constraint. Our experimental analyses show that, when the number of samples is deficient, our approach leads to a higher success rate than conventional rank minimization, while the solutions obtained by the two approaches are almost identical when the number of samples is more than sufficient. We apply our approach to various low-level vision problems, e.g. high dynamic range imaging, motion edge detection, photometric stereo, image alignment and recovery, and show that our results outperform those obtained by the conventional nuclear norm rank minimization method.
from cs.AI updates on arXiv.org http://ift.tt/1Nex0O7
via IFTTT
Orioles: Cal Ripken Jr. believes his record of 2,632 consecutive games can be broken, but doesn't have candidate in mind (ESPN)
via IFTTT
Boavista introduces Rivaldo's son as its newest player
from FOX Sports Digital http://ift.tt/1JLGpHp
via IFTTT
Transfer window: Club rifts, failed moves, record spend
from FOX Sports Digital http://ift.tt/1N8pDJk
via IFTTT
honeysuckle
from Google Alert - anonymous http://ift.tt/1PJVAW3
via IFTTT
[FD] KL-001-2015-004 : XGI Windows VGA Display Manager Arbitrary Write Privilege Escalation
Source: Gmail -> IFTTT-> Blogger
Uruguay set to rescind rights deal over bribery probe
from FOX Sports Digital http://ift.tt/1FhnQtt
via IFTTT
[FD] KL-001-2015-003 : SiS Windows VGA Display Manager Multiple Privilege Escalation
Source: Gmail -> IFTTT-> Blogger
United-Madrid blame game after De Gea deadline-day debacle
from FOX Sports Digital http://ift.tt/1Q6RqIE
via IFTTT
[FD] [CORE-2015-0013] - FortiClient Antivirus Multiple Vulnerabilities
Source: Gmail -> IFTTT-> Blogger


