Latest YouTube Video
Saturday, October 29, 2016
Kringle Vs Krampus: A Santa's Anonymous Benefit Show
from Google Alert - anonymous http://ift.tt/2f4gNOj
via IFTTT
Teenage Hacker Arrested For Disrupting 911 Service With DDoS Attack
from The Hacker News http://ift.tt/2dRmjrv
via IFTTT
Mirai Botnet Itself is Flawed; Hacking Back IoTs Could Mitigate DDoS Attacks
from The Hacker News http://ift.tt/2fgpxWw
via IFTTT
Yearly Arctic Sea Ice Age with Graph of Ice Age by Area: 1984 - 2016
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2eZ3eRA
via IFTTT
Weekly Animation of Arctic Sea Ice Age with Graph of Ice Age by Percent of Total: 1984 - 2016
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2fg78Jz
via IFTTT
Weekly Animation of Arctic Sea Ice Age with Graph of Ice Age By Area: 1984 - 2016
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2eZ1BDf
via IFTTT
Haunting the Cepheus Flare

Friday, October 28, 2016
Why Anonymous “Discernment” Ministries Have No Credibility
from Google Alert - anonymous http://ift.tt/2ePreJf
via IFTTT
Sean Anonymous signs off as Local Current DJ in Residence
from Google Alert - anonymous http://ift.tt/2e51mrr
via IFTTT
[FD] [FOXMOLE SA 2016-07-20] Lupusec XT1 Alarm System - Multiple Issues
Source: Gmail -> IFTTT-> Blogger
[FD] APPLE-SA-2016-10-27-3 iTunes 12.5.2 for Windows
Source: Gmail -> IFTTT-> Blogger
[FD] APPLE-SA-2016-10-27-2 iCloud for Windows v6.0.1
Source: Gmail -> IFTTT-> Blogger
[FD] APPLE-SA-2016-10-27-1 Xcode 8.1
Source: Gmail -> IFTTT-> Blogger
New Privacy Rules require ISPs to must Ask you before Sharing your Sensitive Data
from The Hacker News http://ift.tt/2eD0YRX
via IFTTT
[FD] Wickr Inc - When honesty disappears behind the VCP Mountain
Source: Gmail -> IFTTT-> Blogger
ISS Daily Summary Report – 10/27/2016
from ISS On-Orbit Status Report http://ift.tt/2dOy1Dn
via IFTTT
This Code Injection Technique can Potentially Attack All Versions of Windows
from The Hacker News http://ift.tt/2eYsjdX
via IFTTT
'Celebgate' Hacker Gets 18 Months in Prison for Hacking Celebrity Nude Photos
from The Hacker News http://ift.tt/2eWko2k
via IFTTT
ICON and GOLD: Exploring the Interface to Space
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2eBFVis
via IFTTT
Exploring the Ionosphere: The View from GOLD
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2eT7N0f
via IFTTT
Exploring the Ionosphere: The Dayside Ionosphere
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2eBIukz
via IFTTT
Thursday, October 27, 2016
Synthesis of Shared Control Protocols with Provable Safety and Performance Guarantees. (arXiv:1610.08500v1 [cs.RO])
We formalize synthesis of shared control protocols with correctness guarantees for temporal logic specifications. More specifically, we introduce a modeling formalism in which both a human and an autonomy protocol can issue commands to a robot towards performing a certain task. These commands are blended into a joint input to the robot. The autonomy protocol is synthesized using an abstraction of possible human commands accounting for randomness in decisions caused by factors such as fatigue or incomprehensibility of the problem at hand. The synthesis is designed to ensure that the resulting robot behavior satisfies given safety and performance specifications, e.g., in temporal logic. Our solution is based on nonlinear programming and we address the inherent scalability issue by presenting alternative methods. We assess the feasibility and the scalability of the approach by an experimental evaluation.
from cs.AI updates on arXiv.org http://ift.tt/2fcqH5n
via IFTTT
A Review of 40 Years of Cognitive Architecture Research: Focus on Perception, Attention, Learning and Applications. (arXiv:1610.08602v1 [cs.AI])
In this paper we present a broad overview of the last 40 years of research on cognitive architectures. Although the number of existing architectures is nearing several hundred, most of the existing surveys do not reflect this growth and focus on a handful of well-established architectures. While their contributions are undeniable, they represent only a part of the research in the field. Thus, in this survey we wanted to shift the focus towards a more inclusive and high-level overview of the research in cognitive architectures. Our final set of 86 architectures includes 55 that are still actively developed, and borrow from a diverse set of disciplines, spanning areas from psychoanalysis to neuroscience. To keep the length of this paper within reasonable limits we discuss only the core cognitive abilities, such as perception, attention mechanisms, learning and memory structure. To assess the breadth of practical applications of cognitive architectures we gathered information on over 700 practical projects implemented using the cognitive architectures in our list. We use various visualization techniques to highlight overall trends in the development of the field. Our analysis of practical applications shows that most architectures are very narrowly focused on a particular application domain. Furthermore, there is an apparent gap between general research in robotics and computer vision and research in these areas within the cognitive architectures field. It is very clear that biologically inspired models do not have the same range and efficiency compared to the systems based on engineering principles and heuristics. Another observation is related to a general lack of collaboration. Several factors hinder communication, such as the closed nature of the individual projects (only one-third of the reviewed here architectures are open-source) and terminological differences.
from cs.AI updates on arXiv.org http://ift.tt/2eVFPAm
via IFTTT
Anomaly Detection with the Voronoi Diagram Evolutionary Algorithm. (arXiv:1610.08640v1 [cs.AI])
This paper presents the Voronoi diagram-based evolutionary algorithm (VorEAl). VorEAl partitions input space in abnormal/normal subsets using Voronoi diagrams. Diagrams are evolved using a multi-objective bio-inspired approach in order to conjointly optimize classification metrics while also being able to represent areas of the data space that are not present in the training dataset. As part of the paper VorEAl is experimentally validated and contrasted with similar approaches.
from cs.AI updates on arXiv.org http://ift.tt/2fcnF12
via IFTTT
Personalized Risk Scoring for Critical Care Prognosis using Mixtures of Gaussian Processes. (arXiv:1610.08853v1 [cs.AI])
Objective: In this paper, we develop a personalized real-time risk scoring algorithm that provides timely and granular assessments for the clinical acuity of ward patients based on their (temporal) lab tests and vital signs; the proposed risk scoring system ensures timely intensive care unit (ICU) admissions for clinically deteriorating patients. Methods: The risk scoring system learns a set of latent patient subtypes from the offline electronic health record data, and trains a mixture of Gaussian Process (GP) experts, where each expert models the physiological data streams associated with a specific patient subtype. Transfer learning techniques are used to learn the relationship between a patient's latent subtype and her static admission information (e.g. age, gender, transfer status, ICD-9 codes, etc). Results: Experiments conducted on data from a heterogeneous cohort of 6,321 patients admitted to Ronald Reagan UCLA medical center show that our risk score significantly and consistently outperforms the currently deployed risk scores, such as the Rothman index, MEWS, APACHE and SOFA scores, in terms of timeliness, true positive rate (TPR), and positive predictive value (PPV). Conclusion: Our results reflect the importance of adopting the concepts of personalized medicine in critical care settings; significant accuracy and timeliness gains can be achieved by accounting for the patients' heterogeneity. Significance: The proposed risk scoring methodology can confer huge clinical and social benefits on more than 200,000 critically ill inpatient who exhibit cardiac arrests in the US every year.
from cs.AI updates on arXiv.org http://ift.tt/2eVHINF
via IFTTT
Hit-and-Run for Sampling and Planning in Non-Convex Spaces. (arXiv:1610.08865v1 [stat.CO])
We propose the Hit-and-Run algorithm for planning and sampling problems in non-convex spaces. For sampling, we show the first analysis of the Hit-and-Run algorithm in non-convex spaces and show that it mixes fast as long as certain smoothness conditions are satisfied. In particular, our analysis reveals an intriguing connection between fast mixing and the existence of smooth measure-preserving mappings from a convex space to the non-convex space. For planning, we show advantages of Hit-and-Run compared to state-of-the-art planning methods such as Rapidly-Exploring Random Trees.
from cs.AI updates on arXiv.org http://ift.tt/2fcpRWu
via IFTTT
Learning Scalable Deep Kernels with Recurrent Structure. (arXiv:1610.08936v1 [cs.LG])
Many applications in speech, robotics, finance, and biology deal with sequential data, where ordering matters and recurrent structures are common. However, this structure cannot be easily captured by standard kernel functions. To model such structure, we propose expressive closed-form kernel functions for Gaussian processes. The resulting model, GP-LSTM, fully encapsulates the inductive biases of long short-term memory (LSTM) recurrent networks, while retaining the non-parametric probabilistic advantages of Gaussian processes. We learn the properties of the proposed kernels by optimizing the Gaussian process marginal likelihood using a new provably convergent semi-stochastic procedure and exploit the structure of these kernels for fast and scalable training and prediction. We demonstrate state-of-the-art performance on several benchmarks, and thoroughly investigate a consequential autonomous driving application, where the predictive uncertainties provided by GP-LSTM are uniquely valuable.
from cs.AI updates on arXiv.org http://ift.tt/2eVI9Y0
via IFTTT
On Design Mining: Coevolution and Surrogate Models. (arXiv:1506.08781v5 [cs.NE] UPDATED)
Design mining is the use of computational intelligence techniques to iteratively search and model the attribute space of physical objects evaluated directly through rapid prototyping to meet given objectives. It enables the exploitation of novel materials and processes without formal models or complex simulation. In this paper, we focus upon the coevolutionary nature of the design process when it is decomposed into concurrent sub-design threads due to the overall complexity of the task. Using an abstract, tuneable model of coevolution we consider strategies to sample sub-thread designs for whole system testing, how best to construct and use surrogate models within the coevolutionary scenario, and the effects of access to multiple whole system (physical) testing equipment on performance. Drawing on our findings, the paper then describes the effective design of an array of six heterogeneous vertical-axis wind turbines.
from cs.AI updates on arXiv.org http://ift.tt/1Nx7TnZ
via IFTTT
A Deep Hierarchical Approach to Lifelong Learning in Minecraft. (arXiv:1604.07255v2 [cs.AI] UPDATED)
The ability to reuse or transfer knowledge from one task to another in lifelong learning problems, such as Minecraft, is one of the major challenges faced in AI. Reusing knowledge across tasks is crucial to solving tasks efficiently with lower sample complexity. We provide a Reinforcement Learning agent with the ability to transfer knowledge by learning reusable skills, a type of temporally extended action (also known as Options (Sutton et. al. 1999)). The agent learns reusable skills to solve tasks in Minecraft, a popular video game which is an unsolved and high-dimensional lifelong learning problem. These reusable skills, which we refer to as Deep Skill Networks (DSNs), are then incorporated into our novel Hierarchical Deep Reinforcement Learning Network (H-DRLN) architecture. The H-DRLN, a hierarchical extension of Deep Q-Networks, learns to efficiently solve tasks by reusing knowledge from previously learned DSNs. The DSNs are incorporated into the H-DRLN using two techniques: (1) a DSN array and (2) skill distillation, our novel variation of policy distillation (Rusu et. al. 2015) for learning skills. Skill distillation enables the H-DRLN to scale in lifelong learning, by accumulating knowledge and encapsulating multiple reusable skills into a single distilled network. The H-DRLN exhibits superior performance and lower learning sample complexity (by taking advantage of temporally extended actions) compared to the regular Deep Q Network (Mnih et. al. 2015) in sub-domains of Minecraft. We also show the potential to transfer knowledge between related Minecraft tasks without any additional learning.
from cs.AI updates on arXiv.org http://ift.tt/1WmQ9Sn
via IFTTT
Residual Networks Behave Like Ensembles of Relatively Shallow Networks. (arXiv:1605.06431v2 [cs.CV] UPDATED)
In this work we propose a novel interpretation of residual networks showing that they can be seen as a collection of many paths of differing length. Moreover, residual networks seem to enable very deep networks by leveraging only the short paths during training. To support this observation, we rewrite residual networks as an explicit collection of paths. Unlike traditional models, paths through residual networks vary in length. Further, a lesion study reveals that these paths show ensemble-like behavior in the sense that they do not strongly depend on each other. Finally, and most surprising, most paths are shorter than one might expect, and only the short paths are needed during training, as longer paths do not contribute any gradient. For example, most of the gradient in a residual network with 110 layers comes from paths that are only 10-34 layers deep. Our results reveal one of the key characteristics that seem to enable the training of very deep networks: Residual networks avoid the vanishing gradient problem by introducing short paths which can carry gradient throughout the extent of very deep networks.
from cs.AI updates on arXiv.org http://ift.tt/1sx5TqP
via IFTTT
Domain Adaptation with Soft-margin multiple feature-kernel learning beats Deep Learning for surveillance face recognition. (arXiv:1610.01374v2 [cs.CV] UPDATED)
Face recognition (FR) is the most preferred mode for biometric-based surveillance, due to its passive nature of detecting subjects, amongst all different types of biometric traits. FR under surveillance scenario does not give satisfactory performance due to low contrast, noise and poor illumination conditions on probes, as compared to the training samples. A state-of-the-art technology, Deep Learning, even fails to perform well in these scenarios. We propose a novel soft-margin based learning method for multiple feature-kernel combinations, followed by feature transformed using Domain Adaptation, which outperforms many recent state-of-the-art techniques, when tested using three real-world surveillance face datasets.
from cs.AI updates on arXiv.org http://ift.tt/2dT6v7Y
via IFTTT
Fast Bayesian Non-Negative Matrix Factorisation and Tri-Factorisation. (arXiv:1610.08127v1 [cs.LG])
We present a fast variational Bayesian algorithm for performing non-negative matrix factorisation and tri-factorisation. We show that our approach achieves faster convergence per iteration and timestep (wall-clock) than Gibbs sampling and non-probabilistic approaches, and do not require additional samples to estimate the posterior. We show that in particular for matrix tri-factorisation convergence is difficult, but our variational Bayesian approach offers a fast solution, allowing the tri-factorisation approach to be used more effectively.
from cs.AI updates on arXiv.org http://ift.tt/2eHpmSA
via IFTTT
Showing user as Anonymous user for all downloads
from Google Alert - anonymous http://ift.tt/2eAGXLs
via IFTTT
You Can Hijack Nearly Any Drone Mid-flight Using This Tiny Gadget
from The Hacker News http://ift.tt/2eKGRl0
via IFTTT
Wont work with AccessPress Anonymous Post
from Google Alert - anonymous http://ift.tt/2eQs1HI
via IFTTT
ISS Daily Summary Report – 10/26/2016
from ISS On-Orbit Status Report http://ift.tt/2eeDe3l
via IFTTT
Chinese Hackers won $215,000 for Hacking iPhone and Google Nexus at Mobile Pwn2Own
from The Hacker News http://ift.tt/2eTMESX
via IFTTT
Friday's Massive DDoS Attack Came from Just 100,000 Hacked IoT Devices
from The Hacker News http://ift.tt/2dNy2SZ
via IFTTT
Alcoholics Anonymous-Open Meeting
from Google Alert - anonymous http://ift.tt/2f9AitD
via IFTTT
Rating Feature for Anonymous Users
from Google Alert - anonymous http://ift.tt/2eTadeP
via IFTTT
Statistics logs under Anonymous user
from Google Alert - anonymous http://ift.tt/2f9zPHS
via IFTTT
Racists Anonymous Helping To Make People Aware Of Their Own Biases
from Google Alert - anonymous http://ift.tt/2dMSHXk
via IFTTT
Propeller Shadows on Saturn's Rings
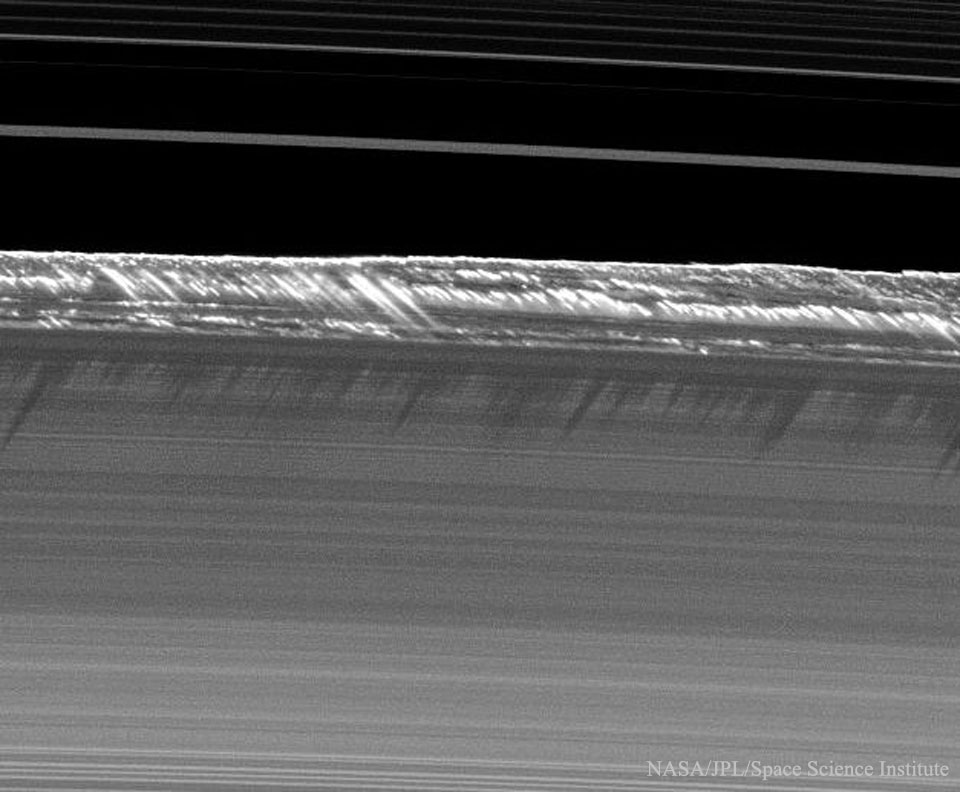
Wednesday, October 26, 2016
Anonymous Ottawa liver donors are coming out of the shadows, hoping to inspire others to do the ...
from Google Alert - anonymous http://ift.tt/2eI7PXS
via IFTTT
I have a new follower on Twitter
Q Digital Studio
We make technology do its job better. So you can do yours. #webdesign #webdevelopment #eecms
Denver, CO
http://t.co/7pPfxoJNWc
Following: 1537 - Followers: 1976
October 26, 2016 at 10:55PM via Twitter http://twitter.com/qdigitalstudio
Infinite-dimensional Log-Determinant divergences II: Alpha-Beta divergences. (arXiv:1610.08087v1 [math.FA])
This work presents a parametrized family of divergences, namely Alpha-Beta Log- Determinant (Log-Det) divergences, between positive definite unitized trace class operators on a Hilbert space. This is a generalization of the Alpha-Beta Log-Determinant divergences between symmetric, positive definite matrices to the infinite-dimensional setting. The family of Alpha-Beta Log-Det divergences is highly general and contains many divergences as special cases, including the recently formulated infinite dimensional affine-invariant Riemannian distance and the infinite-dimensional Alpha Log-Det divergences between positive definite unitized trace class operators. In particular, it includes a parametrized family of metrics between positive definite trace class operators, with the affine-invariant Riemannian distance and the square root of the symmetric Stein divergence being special cases. For the Alpha-Beta Log-Det divergences between covariance operators on a Reproducing Kernel Hilbert Space (RKHS), we obtain closed form formulas via the corresponding Gram matrices.
from cs.AI updates on arXiv.org http://ift.tt/2dM8whb
via IFTTT
A Physician Advisory System for Chronic Heart Failure Management Based on Knowledge Patterns. (arXiv:1610.08115v1 [cs.AI])
Management of chronic diseases such as heart failure, diabetes, and chronic obstructive pulmonary disease (COPD) is a major problem in health care. A standard approach that the medical community has devised to manage widely prevalent chronic diseases such as chronic heart failure (CHF) is to have a committee of experts develop guidelines that all physicians should follow. These guidelines typically consist of a series of complex rules that make recommendations based on a patient's information. Due to their complexity, often the guidelines are either ignored or not complied with at all, which can result in poor medical practices. It is not even clear whether it is humanly possible to follow these guidelines due to their length and complexity. In the case of CHF management, the guidelines run nearly 80 pages. In this paper we describe a physician-advisory system for CHF management that codes the entire set of clinical practice guidelines for CHF using answer set programming. Our approach is based on developing reasoning templates (that we call knowledge patterns) and using these patterns to systemically code the clinical guidelines for CHF as ASP rules. Use of the knowledge patterns greatly facilitates the development of our system. Given a patient's medical information, our system generates a recommendation for treatment just as a human physician would, using the guidelines. Our system will work even in the presence of incomplete information. Our work makes two contributions: (i) it shows that highly complex guidelines can be successfully coded as ASP rules, and (ii) it develops a series of knowledge patterns that facilitate the coding of knowledge expressed in a natural language and that can be used for other application domains. This paper is under consideration for acceptance in TPLP.
from cs.AI updates on arXiv.org http://ift.tt/2fhfSyf
via IFTTT
A self-tuning Firefly algorithm to tune the parameters of Ant Colony System (ACSFA). (arXiv:1610.08222v1 [cs.AI])
Ant colony system (ACS) is a promising approach which has been widely used in problems such as Travelling Salesman Problems (TSP), Job shop scheduling problems (JSP) and Quadratic Assignment problems (QAP). In its original implementation, parameters of the algorithm were selected by trial and error approach. Over the last few years, novel approaches have been proposed on adapting the parameters of ACS in improving its performance. The aim of this paper is to use a framework introduced for self-tuning optimization algorithms combined with the firefly algorithm (FA) to tune the parameters of the ACS solving symmetric TSP problems. The FA optimizes the problem specific parameters of ACS while the parameters of the FA are tuned by the selected framework itself. With this approach, the user neither has to work with the parameters of ACS nor the parameters of FA. Using common symmetric TSP problems we demonstrate that the framework fits well for the ACS. A detailed statistical analysis further verifies the goodness of the new ACS over the existing ACS and also of the other techniques used to tune the parameters of ACS.
from cs.AI updates on arXiv.org http://ift.tt/2dM7kdm
via IFTTT
Quantum-enhanced machine learning. (arXiv:1610.08251v1 [quant-ph])
The emerging field of quantum machine learning has the potential to substantially aid in the problems and scope of artificial intelligence. This is only enhanced by recent successes in the field of classical machine learning. In this work we propose an approach for the systematic treatment of machine learning, from the perspective of quantum information. Our approach is general and covers all three main branches of machine learning: supervised, unsupervised and reinforcement learning. While quantum improvements in supervised and unsupervised learning have been reported, reinforcement learning has received much less attention. Within our approach, we tackle the problem of quantum enhancements in reinforcement learning as well, and propose a systematic scheme for providing improvements. As an example, we show that quadratic improvements in learning efficiency, and exponential improvements in performance over limited time periods, can be obtained for a broad class of learning problems.
from cs.AI updates on arXiv.org http://ift.tt/2fhibBw
via IFTTT
Universal adversarial perturbations. (arXiv:1610.08401v1 [cs.CV])
Given a state-of-the-art deep neural network classifier, we show the existence of a universal (image-agnostic) and very small perturbation vector that causes natural images to be misclassified with high probability. We propose a systematic algorithm for computing universal perturbations, and show that state-of-the-art deep neural networks are highly vulnerable to such perturbations, albeit being quasi-imperceptible to the human eye. We further empirically analyze these universal perturbations and show, in particular, that they generalize very well across neural networks. The surprising existence of universal perturbations reveals important geometric correlations among the high-dimensional decision boundary of classifiers. It further outlines potential security breaches with the existence of single directions in the input space that adversaries can possibly exploit to break a classifier on most natural images.
from cs.AI updates on arXiv.org http://ift.tt/2eHr3Q8
via IFTTT
New Liftable Classes for First-Order Probabilistic Inference. (arXiv:1610.08445v1 [cs.AI])
Statistical relational models provide compact encodings of probabilistic dependencies in relational domains, but result in highly intractable graphical models. The goal of lifted inference is to carry out probabilistic inference without needing to reason about each individual separately, by instead treating exchangeable, undistinguished objects as a whole. In this paper, we study the domain recursion inference rule, which, despite its central role in early theoretical results on domain-lifted inference, has later been believed redundant. We show that this rule is more powerful than expected, and in fact significantly extends the range of models for which lifted inference runs in time polynomial in the number of individuals in the domain. This includes an open problem called S4, the symmetric transitivity model, and a first-order logic encoding of the birthday paradox. We further identify new classes S2FO2 and S2RU of domain-liftable theories, which respectively subsume FO2 and recursively unary theories, the largest classes of domain-liftable theories known so far, and show that using domain recursion can achieve exponential speedup even in theories that cannot fully be lifted with the existing set of inference rules.
from cs.AI updates on arXiv.org http://ift.tt/2eHsKgf
via IFTTT
Kissing Cuisines: Exploring Worldwide Culinary Habits on the Web. (arXiv:1610.08469v1 [cs.CY])
As food becomes an important part of modern life, recipes shared on the web are a great indicator of civilizations and culinary attitudes in different countries. Similarly, ingredients, flavors, and nutrition information are strong signals of the taste preferences of individuals from various parts of the world. Yet, we do not have a thorough understanding of these palate varieties.
In this paper, we present a large-scale study of recipes published on the Web and their content, aiming to understand cuisines and culinary habits around the world. Using a database of more than 157K recipes from over 200 different cuisines, we analyze ingredients, flavors, and nutritional values which distinguish dishes from different regions, and use this knowledge to assess the predictability of recipes from different cuisines. We then use country health statistics to understand the relation between these factors and health indicators of different nations, such as obesity, diabetes, migration, and health expenditure. Our results confirm the strong effects of geographical and cultural similarities on recipes, health indicators, and culinary preferences between countries around the world.
from cs.AI updates on arXiv.org http://ift.tt/2dMbvpJ
via IFTTT
Visual Question Answering: Datasets, Algorithms, and Future Challenges. (arXiv:1610.01465v2 [cs.CV] UPDATED)
Visual Question Answering (VQA) is a recent problem in computer vision and natural language processing that has garnered a large amount of interest from the deep learning, computer vision, and natural language processing communities. In VQA, an algorithm needs to answer text-based questions about images. Since the release of the first VQA dataset in 2014, several additional datasets have been released and many algorithms have been proposed. In this review, we critically examine the current state of VQA in terms of problem formulation, existing datasets, evaluation metrics, and algorithms. In particular, we discuss the limitations of current datasets with regard to their ability to properly train and assess VQA algorithms. We then exhaustively review existing algorithms for VQA. Finally, we discuss possible future directions for VQA and image understanding research.
from cs.AI updates on arXiv.org http://ift.tt/2cUI3xg
via IFTTT
"Helpline" Gives Charleroi Students Anonymous Way To Report Incidents
from Google Alert - anonymous http://ift.tt/2eHIi0G
via IFTTT
[FD] [CSS] POINTYFEATHER / tar extract pathname bypass (CVE-2016-6321)
Source: Gmail -> IFTTT-> Blogger
[FD] CVE-2016-1240 - Tomcat packaging on Debian-based distros - Local Root Privilege Escalation
Source: Gmail -> IFTTT-> Blogger
Anonymous Audit Report from China
from Google Alert - anonymous http://ift.tt/2f8vViA
via IFTTT
I have a new follower on Twitter
Nick Warren
Founder & CEO @MetaSensor
Silicon Valley
https://t.co/lKdg1HAsLk
Following: 5585 - Followers: 5425
October 26, 2016 at 05:15PM via Twitter http://twitter.com/n_warren
How to pass in an anonymous function?
from Google Alert - anonymous http://ift.tt/2dLBugW
via IFTTT
LinkedIn to get Banned in Russia for not Complying with Data Localization Law
from The Hacker News http://ift.tt/2dKZ4dU
via IFTTT
Feinstein: Anonymous Sources Are Inexcusable
from Google Alert - anonymous http://ift.tt/2eRHaXy
via IFTTT
Ravens: QB Joe Flacco assesses his play entering the bye; "I'm obviously not playing well enough" (ESPN)
via IFTTT
The Hacker News launches Online Deals Store – Get Best Deals & Offers
from The Hacker News http://ift.tt/2eFqGFH
via IFTTT
SAP Ideas Forum: Anonymous Extraordinaries to the Rescue
from Google Alert - anonymous http://ift.tt/2dK6a2g
via IFTTT
ISS Daily Summary Report – 10/25/2016
from ISS On-Orbit Status Report http://ift.tt/2eRmaSe
via IFTTT
Hacking Firmware from Mobile Phone Hacking Company Leaked Online
from The Hacker News http://ift.tt/2feDkw8
via IFTTT
I have a new follower on Twitter
Dan Twing
President and COO at EMA Research. Early adopter of tech things, lover of consumer electronics, skiing, woodworking, blues music and billiards.
http://t.co/Y01siy4iJ1
Following: 9093 - Followers: 11519
October 26, 2016 at 03:45AM via Twitter http://twitter.com/dtwing
Anonymous user 507ec9
from Google Alert - anonymous http://ift.tt/2dV9H0Q
via IFTTT
[FD] New VMSA-2016-0017 - VMware product updates address multiple information disclosure issues
Source: Gmail -> IFTTT-> Blogger
STEREO in stereo: Spring 2007 at 171 Angstroms
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2etyzh0
via IFTTT
STEREO in stereo: Spring 2007 at 195 Angstroms
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2eQNhwJ
via IFTTT
STEREO in stereo: Spring 2007 at 284 Angstroms
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2etwr8N
via IFTTT
STEREO in stereo: Spring 2007 at 304 Angstroms
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2eQMQCJ
via IFTTT
Clouds Near Jupiters South Pole from Juno

Tuesday, October 25, 2016
1st Timers Encouraged.
from Google Alert - anonymous http://ift.tt/2f5Zz81
via IFTTT
Surprisal-Driven Zoneout. (arXiv:1610.07675v1 [cs.LG])
We propose a novel method of regularization for recurrent neural networks called suprisal-driven zoneout. In this method, states \textit{zoneout} (maintain their previous value rather than updating), when the \textit{suprisal} (discrepancy between the last state's prediction and target) is small. Thus regularization is adaptive and input-driven on a per-neuron basis. We demonstrate the effectiveness of this idea by achieving state-of-the-art bits per character of 1.32 on the Hutter Prize Wikipedia dataset, significantly reducing the gap to the best known highly-engineered compression methods.
from cs.AI updates on arXiv.org http://ift.tt/2dGBDab
via IFTTT
Knowledge will Propel Machine Understanding of Content: Extrapolating from Current Examples. (arXiv:1610.07708v1 [cs.AI])
Machine Learning has been a big success story during the AI resurgence. One particular stand out success relates to unsupervised learning from a massive amount of data, albeit much of it relates to one modality/type of data at a time. In spite of early assertions of the unreasonable effectiveness of data, there is increasing recognition of utilizing knowledge whenever it is available or can be created purposefully. In this paper, we focus on discussing the indispensable role of knowledge for deeper understanding of complex text and multimodal data in situations where (i) large amounts of training data (labeled/unlabeled) are not available or labor intensive to create, (ii) the objects (particularly text) to be recognized are complex (i.e., beyond simple entity-person/location/organization names), such as implicit entities and highly subjective content, and (iii) applications need to use complementary or related data in multiple modalities/media. What brings us to the cusp of rapid progress is our ability to (a) create knowledge, varying from comprehensive or cross domain to domain or application specific, and (b) carefully exploit the knowledge to further empower or extend the applications of ML/NLP techniques. Using the early results in several diverse situations - both in data types and applications - we seek to foretell unprecedented progress in our ability for deeper understanding and exploitation of multimodal data.
from cs.AI updates on arXiv.org http://ift.tt/2eCZOpZ
via IFTTT
Intelligence in Artificial Intelligence. (arXiv:1610.07862v1 [cs.AI])
The elusive quest for intelligence in artificial intelligence prompts us to consider that instituting human-level intelligence in systems may be (still) in the realm of utopia. In about a quarter century, we have witnessed the winter of AI (1990) being transformed and transported to the zenith of tabloid fodder about AI (2015). The discussion at hand is about the elements that constitute the canonical idea of intelligence. The delivery of intelligence as a pay-per-use-service, popping out of an app or from a shrink-wrapped software defined point solution, is in contrast to the bio-inspired view of intelligence as an outcome, perhaps formed from a tapestry of events, cross-pollinated by instances, each with its own microcosm of experiences and learning, which may not be discrete all-or-none functions but continuous, over space and time. The enterprise world may not require, aspire or desire such an engaged solution to improve its services for enabling digital transformation through the deployment of digital twins, for example. One might ask whether the "work-flow on steroids" version of decision support may suffice for intelligence? Are we harking back to the era of rule based expert systems? The image conjured by the publicity machines offers deep solutions with human-level AI and preposterous claims about capturing the "brain in a box" by 2020. Even emulating insects may be difficult in terms of real progress. Perhaps we can try to focus on worms (Caenorhabditis elegans) which may be better suited for what business needs to quench its thirst for so-called intelligence in AI.
from cs.AI updates on arXiv.org http://ift.tt/2eJs0p8
via IFTTT
Artificial Intelligence Safety and Cybersecurity: a Timeline of AI Failures. (arXiv:1610.07997v1 [cs.AI])
In this work, we present and analyze reported failures of artificially intelligent systems and extrapolate our analysis to future AIs. We suggest that both the frequency and the seriousness of future AI failures will steadily increase. AI Safety can be improved based on ideas developed by cybersecurity experts. For narrow AIs safety failures are at the same, moderate, level of criticality as in cybersecurity, however for general AI, failures have a fundamentally different impact. A single failure of a superintelligent system may cause a catastrophic event without a chance for recovery. The goal of cybersecurity is to reduce the number of successful attacks on the system; the goal of AI Safety is to make sure zero attacks succeed in bypassing the safety mechanisms. Unfortunately, such a level of performance is unachievable. Every security system will eventually fail; there is no such thing as a 100% secure system.
from cs.AI updates on arXiv.org http://ift.tt/2eCWhYK
via IFTTT
Backdoors into Heterogeneous Classes of SAT and CSP. (arXiv:1509.05725v2 [cs.AI] UPDATED)
In this paper we extend the classical notion of strong and weak backdoor sets for SAT and CSP by allowing that different instantiations of the backdoor variables result in instances that belong to different base classes; the union of the base classes forms a heterogeneous base class. Backdoor sets to heterogeneous base classes can be much smaller than backdoor sets to homogeneous ones, hence they are much more desirable but possibly harder to find. We draw a detailed complexity landscape for the problem of detecting strong and weak backdoor sets into heterogeneous base classes for SAT and CSP.
from cs.AI updates on arXiv.org http://ift.tt/1LH8wbX
via IFTTT
Recurrent Instance Segmentation. (arXiv:1511.08250v3 [cs.CV] UPDATED)
Instance segmentation is the problem of detecting and delineating each distinct object of interest appearing in an image. Current instance segmentation approaches consist of ensembles of modules that are trained independently of each other, thus missing opportunities for joint learning. Here we propose a new instance segmentation paradigm consisting in an end-to-end method that learns how to segment instances sequentially. The model is based on a recurrent neural network that sequentially finds objects and their segmentations one at a time. This net is provided with a spatial memory that keeps track of what pixels have been explained and allows occlusion handling. In order to train the model we designed a principled loss function that accurately represents the properties of the instance segmentation problem. In the experiments carried out, we found that our method outperforms recent approaches on multiple person segmentation, and all state of the art approaches on the Plant Phenotyping dataset for leaf counting.
from cs.AI updates on arXiv.org http://ift.tt/1TfqNCg
via IFTTT
Quadripolar Relational Model: a framework for the description of borderline and narcissistic personality disorders. (arXiv:1512.05875v4 [q-bio.NC] UPDATED)
Borderline personality disorder and narcissistic personality disorder are important nosographic entities and have been subject of intensive investigations. The currently prevailing psychodynamic theory for mental disorders is based on the repertoire of defense mechanisms employed. Another line of research is concerned with the study of psychological traumas and dissociation as a defensive response. Both theories can be used to shed light on some aspects of pathological mental functioning, and have many points of contact. This work merges these two psychological theories, and builds a model of mental function in a relational context called Quadripolar Relational Model. The model, which is enriched with ideas borrowed from the field of computer science, leads to a new therapeutic proposal for psychological traumas and personality disorders.
from cs.AI updates on arXiv.org http://ift.tt/1QAee7l
via IFTTT
Directed expected utility networks. (arXiv:1608.00810v2 [cs.AI] UPDATED)
A variety of statistical graphical models have been defined to represent the conditional independences underlying a random vector of interest. Similarly, many different graphs embedding various types of preferential independences, as for example conditional utility independence and generalized additive independence, have more recently started to appear. In this paper we define a new graphical model, called a directed expected utility network, whose edges depict both probabilistic and utility conditional independences. These embed a very flexible class of utility models, much larger than those usually conceived in standard influence diagrams. Our graphical representation, and various transformations of the original graph into a tree structure, are then used to guide fast routines for the computation of a decision problem's expected utilities. We show that our routines generalize those usually utilized in standard influence diagrams' evaluations under much more restrictive conditions. We then proceed with the construction of a directed expected utility network to support decision makers in the domain of household food security.
from cs.AI updates on arXiv.org http://ift.tt/2awhr8q
via IFTTT
Knowledge Semantic Representation: A Generative Model for Interpretable Knowledge Graph Embedding. (arXiv:1608.07685v2 [cs.LG] UPDATED)
Knowledge representation is an important, long-history topic in AI, and there have been a large amount of work for knowledge graph embedding which projects symbolic entities and relations into low-dimensional, real-valued vector space. However, most embedding methods merely concentrate on data fitting and ignore the explicit semantic expression, leading to uninterpretable representations. Thus, traditional embedding methods have limited potentials for many applications such as question answering, and entity classification. To this end, this paper proposes a semantic representation method for knowledge graph \textbf{(KSR)}, which imposes a two-level hierarchical generative process that globally extracts many aspects and then locally assigns a specific category in each aspect for every triple. Since both aspects and categories are semantics-relevant, the collection of categories in each aspect is treated as the semantic representation of this triple. Extensive experiments justify our model outperforms other state-of-the-art baselines substantially.
from cs.AI updates on arXiv.org http://ift.tt/2bA0s2h
via IFTTT
Verifier Theory and Unverifiability. (arXiv:1609.00331v3 [cs.AI] UPDATED)
Despite significant developments in Proof Theory, surprisingly little attention has been devoted to the concept of proof verifier. In particular, the mathematical community may be interested in studying different types of proof verifiers (people, programs, oracles, communities, superintelligences) as mathematical objects. Such an effort could reveal their properties, their powers and limitations (particularly in human mathematicians), minimum and maximum complexity, as well as self-verification and self-reference issues. We propose an initial classification system for verifiers and provide some rudimentary analysis of solved and open problems in this important domain. Our main contribution is a formal introduction of the notion of unverifiability, for which the paper could serve as a general citation in domains of theorem proving, as well as software and AI verification.
from cs.AI updates on arXiv.org http://ift.tt/2bNpI54
via IFTTT
Anonymous post possible?
from Google Alert - anonymous http://ift.tt/2fcZizC
via IFTTT
Ravens LB Terrell Suggs practice Tuesday, just nine days after tearing his biceps (ESPN)
via IFTTT
I have a new follower on Twitter
Andrea Stockton
#Internet #Marketing Executive. #Twitter #Instagram #Facebook #Social #Media #Marketing
Toronto, Ontario
Following: 2169 - Followers: 2761
October 25, 2016 at 02:24PM via Twitter http://twitter.com/AndreaStockton6
[FD] AST-2016-007: UPDATE
Source: Gmail -> IFTTT-> Blogger
I have a new follower on Twitter
Riser Digital
Riser Digital is a results-driven #digitalmarketing agency for small businesses & startups, with #strategy, #creative, & #marketing expertise.
Everywhere!
https://t.co/mrVng1rr5S
Following: 4690 - Followers: 5234
October 25, 2016 at 01:59PM via Twitter http://twitter.com/riserdigital
I have a new follower on Twitter
Debra Mitchel
Following: 1804 - Followers: 1412
October 25, 2016 at 01:59PM via Twitter http://twitter.com/DebraDebramitch
Anonymous Human Being
from Google Alert - anonymous http://ift.tt/2eraXMd
via IFTTT
Ravens (3-4) down 3 spots to No. 21 in Week 8 NFL Power Rankings; on BYE this week, host Steelers on Nov. 6 (ESPN)
via IFTTT
Joomla Joomla! Two Critical Flaws Discovered — Update to Protect Your Site
from The Hacker News http://ift.tt/2eFTGvG
via IFTTT
Missing dependency breaks anonymous users validation for custom forms
from Google Alert - anonymous http://ift.tt/2dSyhQ7
via IFTTT
Support and Site Caps: Good News
from Google Alert - anonymous http://ift.tt/2eNjFiy
via IFTTT
Anonymous, Authenticated summary should be displayed in roles list page
from Google Alert - anonymous http://ift.tt/2eNiAqZ
via IFTTT
ISS Daily Summary Report – 10/24/2016
from ISS On-Orbit Status Report http://ift.tt/2ejYmGU
via IFTTT
I have a new follower on Twitter
Tammo Mueller
Entrepreneur, Technologist, Founder & CTO Scientific.ly - 'Life has no rehearsals, only performances.'
NYC
http://t.co/28wFRtVnqj
Following: 1288 - Followers: 1432
October 25, 2016 at 05:59AM via Twitter http://twitter.com/tammomueller
WhatsApp Video Calling is Now Available for Android – Download Beta Version Now!
from The Hacker News http://ift.tt/2ejiVDF
via IFTTT
Warning! Your iPhone Can Get Hacked Just by Opening a JPEG Image, PDF or Font File
from The Hacker News http://ift.tt/2eAqGqu
via IFTTT
facebook-anonymous-publisher/graph-api
from Google Alert - anonymous http://ift.tt/2eq8csg
via IFTTT
Anonymous v Hillary
from Google Alert - anonymous http://ift.tt/2f2KUum
via IFTTT
Monday, October 24, 2016
I have a new follower on Twitter
Alexander Jones
☎️ restoring failed initiatives + ⛱ founder @PassionOurGuide +💡 @BiviHQ + 🎯 https://t.co/V0Dxw7WhqI + 📚 writing https://t.co/ShsAzuUZUd + UX design + startups
Chicago
https://t.co/3Omf4hq5CO
Following: 7767 - Followers: 10497
October 24, 2016 at 11:44PM via Twitter http://twitter.com/MrJonesEdition


