Latest YouTube Video
Saturday, July 16, 2016
Orioles Video: J.J. Hardy powers the offense with a 2-run homer down the left field line in 2-1 win over the Rays (ESPN)
via IFTTT
Anonymous-Sensei
from Google Alert - anonymous http://ift.tt/2a1QCrf
via IFTTT
Here's How Riffle Anonymity Network Protects Your Privacy better than Tor
from The Hacker News http://ift.tt/29JIitF
via IFTTT
How to Stay Anonymous Online
from Google Alert - anonymous http://ift.tt/2ahFJRo
via IFTTT
NGC 2736: The Pencil Nebula

Friday, July 15, 2016
Orioles Video: Jonathan Schoop takes Chris Archer deep for a solo homer to break open a tie game in 4-3 win vs. Rays (ESPN)
via IFTTT
Q&A with Nightline Volunteer (Anonymous)
from Google Alert - anonymous http://ift.tt/29E4hCn
via IFTTT
Ravens, K Justin Tucker agree to 4-year, $16.8M deal that includes $10.8M guaranteed (most ever for a kicker) - Schefter (ESPN)
via IFTTT
Ubuntu Linux Forum Hacked! Once Again
from The Hacker News http://ift.tt/29UGFNO
via IFTTT
[FD] x-originating-ip: [25.162.68.132]
Source: Gmail -> IFTTT-> Blogger
[FD] opensshd - user enumeration
Source: Gmail -> IFTTT-> Blogger
[FD] Blind SQL Injection PivotX <= v2.3.11
Source: Gmail -> IFTTT-> Blogger
[FD] missing input validation in pmount: arbitrary mount as non-root
Source: Gmail -> IFTTT-> Blogger
Anonymous Already Pursuing Justice for Nice Attack
from Google Alert - anonymous http://ift.tt/29UAM3d
via IFTTT
[FD] [ERPSCAN-16-021] SAP xMII - Reflected XSS vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] [ERPSCAN-16-019] SAP NetWeaver Enqueue Server - DoS vulnerability
Source: Gmail -> IFTTT-> Blogger
Can't get intellisense to link params for anonymous functions
from Google Alert - anonymous http://ift.tt/29UXrLi
via IFTTT
Microsoft Wins! Govt Can't Force Tech Companies to Hand Over Data Stored Overseas
from The Hacker News http://ift.tt/29NLKqK
via IFTTT
NGC 1309: Spiral Galaxy and Friends

Thursday, July 14, 2016
Resource Planning For Rescue Operations. (arXiv:1607.03979v1 [cs.AI])
After an earthquake, disaster sites pose a multitude of health and safety concerns. A rescue operation of people trapped in the ruins after an earthquake disaster requires a series of intelligent behavior, including planning. For a successful rescue operation, given a limited number of available actions and regulations, the role of planning in rescue operations is crucial. Fortunately, recent developments in automated planning by artificial intelligence community can help different organization in this crucial task. Due to the number of rules and regulations, we believe that a rule based system for planning can be helpful for this specific planning problem. In this research work, we use logic rules to represent rescue and related regular regulations, together with a logic based planner to solve this complicated problem. Although this research is still in the prototyping and modeling stage, it clearly shows that rule based languages can be a good infrastructure for this computational task. The results of this research can be used by different organizations, such as Iranian Red Crescent Society and International Institute of Seismology and Earthquake Engineering (IISEE).
from cs.AI updates on arXiv.org http://ift.tt/29GaayD
via IFTTT
Using Recurrent Neural Network for Learning Expressive Ontologies. (arXiv:1607.04110v1 [cs.CL])
Recently, Neural Networks have been proven extremely effective in many natural language processing tasks such as sentiment analysis, question answering, or machine translation. Aiming to exploit such advantages in the Ontology Learning process, in this technical report we present a detailed description of a Recurrent Neural Network based system to be used to pursue such goal.
from cs.AI updates on arXiv.org http://ift.tt/29TQw56
via IFTTT
Multi-modal dictionary learning for image separation with application in art investigation. (arXiv:1607.04147v1 [cs.CV])
In support of art investigation, we propose a new source separation method that unmixes a single X-ray scan acquired from double-sided paintings. In this problem, the X-ray signals to be separated have similar morphological characteristics, which brings previous source separation methods to their limits. Our solution is to use photographs taken from the front and back-side of the panel to drive the separation process. The crux of our approach relies on the coupling of the two imaging modalities (photographs and X-rays) using a novel coupled dictionary learning framework able to capture both common and disparate features across the modalities using parsimonious representations; the common component models features shared by the multi-modal images, whereas the innovation component captures modality-specific information. As such, our model enables the formulation of appropriately regularized convex optimization procedures that lead to the accurate separation of the X-rays. Our dictionary learning framework can be tailored both to a single- and a multi-scale framework, with the latter leading to a significant performance improvement. Moreover, to improve further on the visual quality of the separated images, we propose to train coupled dictionaries that ignore certain parts of the painting corresponding to craquelure. Experimentation on synthetic and real data - taken from digital acquisition of the Ghent Altarpiece (1432) - confirms the superiority of our method against the state-of-the-art morphological component analysis technique that uses either fixed or trained dictionaries to perform image separation.
from cs.AI updates on arXiv.org http://ift.tt/29Ih6yE
via IFTTT
Large-scale Analysis of Chess Games with Chess Engines: A Preliminary Report. (arXiv:1607.04186v1 [cs.AI])
The strength of chess engines together with the availability of numerous chess games have attracted the attention of chess players, data scientists, and researchers during the last decades. State-of-the-art engines now provide an authoritative judgement that can be used in many applications like cheating detection, intrinsic ratings computation, skill assessment, or the study of human decision-making. A key issue for the research community is to gather a large dataset of chess games together with the judgement of chess engines. Unfortunately the analysis of each move takes lots of times. In this paper, we report our effort to analyse almost 5 millions chess games with a computing grid. During summer 2015, we processed 270 millions unique played positions using the Stockfish engine with a quite high depth (20). We populated a database of 1+ tera-octets of chess evaluations, representing an estimated time of 50 years of computation on a single machine. Our effort is a first step towards the replication of research results, the supply of open data and procedures for exploring new directions, and the investigation of software engineering/scalability issues when computing billions of moves.
from cs.AI updates on arXiv.org http://ift.tt/29UjmFz
via IFTTT
Managing Overstaying Electric Vehicles in Park-and-Charge Facilities. (arXiv:1604.05471v2 [cs.AI] UPDATED)
With the increase in adoption of Electric Vehicles (EVs), proper utilization of the charging infrastructure is an emerging challenge for service providers. Overstaying of an EV after a charging event is a key contributor to low utilization. Since overstaying is easily detectable by monitoring the power drawn from the charger, managing this problem primarily involves designing an appropriate "penalty" during the overstaying period. Higher penalties do discourage overstaying; however, due to uncertainty in parking duration, less people would find such penalties acceptable, leading to decreased utilization (and revenue). To analyze this central trade-off, we develop a novel framework that integrates models for realistic user behavior into queueing dynamics to locate the optimal penalty from the points of view of utilization and revenue, for different values of the external charging demand. Next, when the model parameters are unknown, we show how an online learning algorithm, such as UCB, can be adapted to learn the optimal penalty. Our experimental validation, based on charging data from London, shows that an appropriate penalty can increase both utilization and revenue while significantly reducing overstaying.
from cs.AI updates on arXiv.org http://ift.tt/1QlwX0e
via IFTTT
Ravens: Franchise K Justin Tucker vowing not to re-sign if long-term deal not done by Friday, agent tells Adam Schefter (ESPN)
via IFTTT
Completion will not show doc comments for symbols containing anonymous types in them.
from Google Alert - anonymous http://ift.tt/29BPGr7
via IFTTT
I have a new follower on Twitter
mjbasgall
Information Systems Engineer - PhD student in Computer Science - CONICET - UNLP - #BigData #MachineLearning and other things
Buenos Aires, Argentina
https://t.co/NTiNqveWRR
Following: 176 - Followers: 25
July 14, 2016 at 04:39PM via Twitter http://twitter.com/mjbasgall
I'm Warning You, Don't Read this Article. It's a Federal Crime!
from The Hacker News http://ift.tt/29St6A9
via IFTTT
Anonymous complaints can be examined if charge is serious: CVC
from Google Alert - anonymous http://ift.tt/29z6mQL
via IFTTT
ISS Daily Summary Report – 07/13/16
from ISS On-Orbit Status Report http://ift.tt/29G3a5T
via IFTTT
3 Popular Drupal Modules Found Vulnerable — Patch Released
from The Hacker News http://ift.tt/29FfR69
via IFTTT
What is Anonymous Call Rejection?
from Google Alert - anonymous http://ift.tt/29S8LLf
via IFTTT
DARPA Challenges Hackers to Create Automated Hacking System — WIN $2 Million
from The Hacker News http://ift.tt/2a02wV4
via IFTTT
I have a new follower on Twitter
Gayle Nixon, MBA
Why fit in when you were born to stand out? ~Dr. Seuss | Strategic B2B Marketing Leader who loves to inspire others & drive revenue thru innovative campaigns!
https://t.co/Y6INRImUqw
Following: 8076 - Followers: 9494
July 14, 2016 at 12:55AM via Twitter http://twitter.com/GayleNixon_
M7: Open Star Cluster in Scorpius

Wednesday, July 13, 2016
I have a new follower on Twitter
David A. Chapa
David A. Chapa is a CTO with @elovatetech, and coworker at @conxspot. Tweets and comments are his own. oh, and he rides a Harley, thinks that makes him bad ass.
ÜT: 39.787929,-104.724543
https://t.co/1oIsMN17WB
Following: 2968 - Followers: 3852
July 13, 2016 at 11:27PM via Twitter http://twitter.com/davidchapa
Police Seek Anonymous Tipster in Cold Case
from Google Alert - anonymous http://ift.tt/29F4IxX
via IFTTT
I have a new follower on Twitter
Metiora
Conecting things for smart decisions #iot #ioe. Instagram: @mymetiora Metiora an Unlimiteck Company https://t.co/yB8SndNnkm @myunlimiteck
https://t.co/P7z5EyDMJq
Following: 4033 - Followers: 4426
July 13, 2016 at 10:27PM via Twitter http://twitter.com/MyMetiora
Characterizing Driving Styles with Deep Learning. (arXiv:1607.03611v1 [cs.AI])
Characterizing driving styles of human drivers using vehicle sensor data, e.g., GPS, is an interesting research problem and an important real-world requirement from automotive industries. A good representation of driving features can be highly valuable for autonomous driving, auto insurance, and many other application scenarios. However, traditional methods mainly rely on handcrafted features, which limit machine learning algorithms to achieve a better performance. In this paper, we propose a novel deep learning solution to this problem, which could be the first attempt of studying deep learning for driving behavior analysis. The proposed approach can effectively extract high level and interpretable features describing complex driving patterns from GPS data. It also requires significantly less human experience and work. The power of the learned driving style representations are validated through the driver identification problem using a large real dataset.
from cs.AI updates on arXiv.org http://ift.tt/29FDj0h
via IFTTT
Possibilistic Networks: Parameters Learning from Imprecise Data and Evaluation strategy. (arXiv:1607.03705v1 [cs.AI])
There has been an ever-increasing interest in multidisciplinary research on representing and reasoning with imperfect data. Possibilistic networks present one of the powerful frameworks of interest for representing uncertain and imprecise information. This paper covers the problem of their parameters learning from imprecise datasets, i.e., containing multi-valued data. We propose in the rst part of this paper a possibilistic networks sampling process. In the second part, we propose a likelihood function which explores the link between random sets theory and possibility theory. This function is then deployed to parametrize possibilistic networks.
from cs.AI updates on arXiv.org http://ift.tt/2aaM4hu
via IFTTT
Computation of Stackelberg Equilibria of Finite Sequential Games. (arXiv:1507.07677v2 [cs.GT] UPDATED)
The Stackelberg equilibrium solution concept describes optimal strategies to commit to: Player 1 (termed the leader) publicly commits to a strategy and Player 2 (termed the follower) plays a best response to this strategy (ties are broken in favor of the leader). We study Stackelberg equilibria in finite sequential games (or extensive-form games) and provide new exact algorithms, approximate algorithms, and hardness results for several classes of these sequential games.
from cs.AI updates on arXiv.org http://ift.tt/1OAk03z
via IFTTT
Causal Discovery from Subsampled Time Series Data by Constraint Optimization. (arXiv:1602.07970v2 [cs.AI] UPDATED)
This paper focuses on causal structure estimation from time series data in which measurements are obtained at a coarser timescale than the causal timescale of the underlying system. Previous work has shown that such subsampling can lead to significant errors about the system's causal structure if not properly taken into account. In this paper, we first consider the search for the system timescale causal structures that correspond to a given measurement timescale structure. We provide a constraint satisfaction procedure whose computational performance is several orders of magnitude better than previous approaches. We then consider finite-sample data as input, and propose the first constraint optimization approach for recovering the system timescale causal structure. This algorithm optimally recovers from possible conflicts due to statistical errors. More generally, these advances allow for a robust and non-parametric estimation of system timescale causal structures from subsampled time series data.
from cs.AI updates on arXiv.org http://ift.tt/21vgteo
via IFTTT
The AGI Containment Problem. (arXiv:1604.00545v3 [cs.AI] UPDATED)
There is considerable uncertainty about what properties, capabilities and motivations future AGIs will have. In some plausible scenarios, AGIs may pose security risks arising from accidents and defects. In order to mitigate these risks, prudent early AGI research teams will perform significant testing on their creations before use. Unfortunately, if an AGI has human-level or greater intelligence, testing itself may not be safe; some natural AGI goal systems create emergent incentives for AGIs to tamper with their test environments, make copies of themselves on the internet, or convince developers and operators to do dangerous things. In this paper, we survey the AGI containment problem - the question of how to build a container in which tests can be conducted safely and reliably, even on AGIs with unknown motivations and capabilities that could be dangerous. We identify requirements for AGI containers, available mechanisms, and weaknesses that need to be addressed.
from cs.AI updates on arXiv.org http://ift.tt/227J5bZ
via IFTTT
Demand Prediction and Placement Optimization for Electric Vehicle Charging Stations. (arXiv:1604.05472v2 [cs.AI] UPDATED)
Effective placement of charging stations plays a key role in Electric Vehicle (EV) adoption. In the placement problem, given a set of candidate sites, an optimal subset needs to be selected with respect to the concerns of both (a) the charging station service provider, such as the demand at the candidate sites and the budget for deployment, and (b) the EV user, such as charging station reachability and short waiting times at the station. This work addresses these concerns, making the following three novel contributions: (i) a supervised multi-view learning framework using Canonical Correlation Analysis (CCA) for demand prediction at candidate sites, using multiple datasets such as points of interest information, traffic density, and the historical usage at existing charging stations; (ii) a mixed-packing-and- covering optimization framework that models competing concerns of the service provider and EV users; (iii) an iterative heuristic to solve these problems by alternately invoking knapsack and set cover algorithms. The performance of the demand prediction model and the placement optimization heuristic are evaluated using real world data.
from cs.AI updates on arXiv.org http://ift.tt/1pfq2zz
via IFTTT
Anonymous-12414261
from Google Alert - anonymous http://ift.tt/29QQZbm
via IFTTT
I have a new follower on Twitter
Portray.al
Portray.al is a #creativeagency and #talentpool based in LA & Bangkok. We help #dynamicpeople build their #brand and change the world. #showupbeseen
International
https://t.co/VsZdfgj8pM
Following: 420 - Followers: 460
July 13, 2016 at 06:45PM via Twitter http://twitter.com/portrayalteam
Thumb-Suckers Anonymous
from Google Alert - anonymous http://ift.tt/29z3N0f
via IFTTT
[FD] Cross-Site Scripting vulnerability in Google Forms WordPress Plugin
Source: Gmail -> IFTTT-> Blogger
[FD] Cross-Site Scripting vulnerability in WP No External Links WordPress Plugin
Source: Gmail -> IFTTT-> Blogger
[FD] Cross-Site Scripting vulnerability in Top 10 - Popular posts plugin for WordPress
Source: Gmail -> IFTTT-> Blogger
[FD] Cross-Site Scripting vulnerability in Simple Membership WordPress Plugin
Source: Gmail -> IFTTT-> Blogger
I have a new follower on Twitter
Karolina Kocalevski
Marketer, Aussie New Yorker, devoted mom, wife, global friend. Wannabe designer. Aspiring runner. Serenity seeker. Coffee lover. Views my own.
New York
http://t.co/yOwCcztPEO
Following: 223 - Followers: 457
July 13, 2016 at 10:28AM via Twitter http://twitter.com/KKocalevski
NOW HIRING: Computer Vision and OpenCV Correspondence Coordinator
The PyImageSearch blog has grown a lot since I published that first post back in January 2014. It’s been an incredible journey and I have you, the reader, to thank for all the support over the past 2.5 years.
However, due to the whirlwind growth of PyImageSearch, I now receive 100+ emails per day — and it’s gotten to the point where I can’t keep up with them all.
Believe it or not, I have been the only employee of PyImageSearch for the past 2.5 years — and I’ve personally answered each and every email I’ve received during that time.
Interacting with you is honestly one of the highlights of my day.
For example:
Have you emailed me a question, no matter how basic or advanced, regarding computer vision?
Yep, I answered it.
Did you email me, asking about Practical Python and OpenCV? Or inquiring regarding the PyImageSearch Gurus course?
I was the one who responded.
Did you need technical support of some kind?
I was there offer assistance.
But due to the volume, it has gotten to the point where I need a correspondence coordinator to come in and help me:
- Prioritize and triage emails and inquiries.
- Answer general questions and comments regarding content on the PyImageSearch blog.
- Point readers in the right direction if they have a question you can answer.
- Categorize more advanced questions/business inquiries that you cannot answer for me to personally respond to.
In short, the primary role of this job consists of two elements:
- Help me answer questions regarding computer vision and OpenCV.
- Categorize incoming emails and questions, so I have a clear, prioritized view when I login to respond.
This will help me serve the PyImageSearch community even more, since I’ll be able to focus on the tasks that specifically need my experience and expertise.
JOB DETAILS
- Part time: 2-4 hours per day, every day Monday-Friday
- Paid on an hourly rate (this is flexible — I will consider a fixed weekly or monthly payment as well)
- Work remotely
- Compensation based on experience ($25-$55 per hour, depending on experience)
Of course, if you’re an exceptional fit for this position, the roles of and responsibilities for this job can grow as well. Think of this as your entry point to working with me.
SKILLS AND REQUIREMENTS
To be successful in this role, you need to have the following skills and qualities:
- You hold yourself to high standards.
- You have STRONG written and verbal communication skills in the ENGLISH language.
- You have previous experience in computer vision (the more experience, the better).
- You have knowledge of the OpenCV library and have used it in previous projects (the more experience, the better).
- You have the ability to write clear, coherent responses to questions involving computer vision, image processing, and OpenCV.
- You enjoy answering questions, providing feedback, offering suggestions, and really helping people.
- You are professional in your responses.
- You can maintain a positive attitude when responding to questions.
- You have basic Python programming skills.
- You have basic Unix experience.
BONUS POINTS IF:
- You are a long-time reader of the PyImageSearch blog.
- You have read through the Practical Python and OpenCV book.
- You have graduated from the PyImageSearch Gurus course.
- You have earned a college-level degree with coursework/final project/thesis involving computer vision, or similar real world experience.
- You have an awesome StackOverflow reputation.
- You have experience with the Raspberry Pi.
AM I RIGHT FOR THIS JOB?
You are the right person for this job if:
- You enjoy computer vision and like helping others.
- You want to work with a successful entrepreneur in a small company — and help shape the future of PyImageSearch.
Taking this job is more than answering questions regarding computer vision, image processing, and OpenCV. It’s a chance to work with me and learn from me. You don’t have to be an entrepreneur yourself to apply for this job, but I would expect that you’re interested (at some level) in startups and small business.
WHEN DOES THIS JOB START?
As soon as possible — I am targeting mid-August as a start date, but I will be flexible if you have circumstances that prevent you from starting then (you have to be the right fit for the job, of course).
HOW DO I APPLY?
To apply for this job, please use this link:
I’ll be accepting applications until July 31st at 11:59PM EST, so make sure you get your applications in by then!
WHAT HAPPENS AFTER I APPLY?
After you apply, I’ll be personally reviewing your application.
From there, I’ll follow up with you over email, ask any additional questions, and if necessary, set up a formal interview, etc., normally within 3-4 days.
I’ll also be asking you to answer a few sample emails to get a feel for your writing style and computer vision/OpenCV knowledge. Don’t worry, there aren’t any “right” or “wrong” responses to these examples — I just need to get a feeling of how you write and interact with others. If you applied, be sure to keep an eye on your inbox for this next series of emails!
The post NOW HIRING: Computer Vision and OpenCV Correspondence Coordinator appeared first on PyImageSearch.
from PyImageSearch http://ift.tt/29NPokG
via IFTTT
Search not working on /search/* page for anonymous users
from Google Alert - anonymous http://ift.tt/2a9bMCR
via IFTTT
Several Critical Remotely Exploitable Flaws Found in Drupal Modules, patch ASAP!
from The Hacker News http://ift.tt/29vtAv4
via IFTTT
ISS Daily Summary Report – 07/12/16
from ISS On-Orbit Status Report http://ift.tt/29NJAYD
via IFTTT
State-Sponsored SCADA Malware targeting European Energy Companies
from The Hacker News http://ift.tt/29NoklF
via IFTTT
Critical Print Spooler Bug allows Attackers to Hack any version of Microsoft Windows
from The Hacker News http://ift.tt/29QRqil
via IFTTT
prod unexpected token: name (BroccoliPlugin BundlePlugin failed)
from Google Alert - anonymous http://ift.tt/29weEck
via IFTTT
Self-tallying quantum anonymous voting
from Google Alert - anonymous http://ift.tt/29uQRNm
via IFTTT
Chasing Juno

Tuesday, July 12, 2016
Orioles: Zach Britton gets the save for AL in 4-2 All-Star Game victory; allowed one hit before inducing game-ending DP (ESPN)
via IFTTT
I have a new follower on Twitter
Digital Trends
Tech for the way we live. | Instagram: @DigitalTrends | Snapchat: digitaltrends
Portland, OR, and New York, NY
https://t.co/wxxwes6lsF
Following: 670135 - Followers: 744224
July 12, 2016 at 11:13PM via Twitter http://twitter.com/DigitalTrends
A Framework for Estimating Long Term Driver Behavior. (arXiv:1607.03189v1 [cs.RO])
The authors present a cyber-physical systems study on the estimation of driver behavior in autonomous vehicles and vehicle safety systems. Extending upon previous work, the approach described is suitable for the long term estimation and tracking of autonomous vehicle behavior. The proposed system makes use of a previously defined Hybrid State System and Hidden Markov Model (HSS+HMM) system which has provided good results for driver behavior estimation. The HSS+HMM system utilizes the hybrid characteristics of decision-behavior coupling of many systems such as the driver and the vehicle, uses Kalman Filter estimates of observable parameters to track the instantaneous continuous state, and estimates the most likely driver state. The HSS+HMM system is encompassed in a HSS structure and inter-system connectivity is determined by using Signal Processing and Pattern Recognition techniques. The proposed method is suitable for scenarios that involve unknown decisions of other individuals, such as lane changes or intersection precedence/access. The long term driver behavior estimation system involves an extended HSS+HMM structure that is capable of including external information in the estimation process. Through the grafting and pruning of metastates, the HSS+HMM system can be dynamically updated to best represent driver choices given external information. Three application examples are also provided to elucidate the theoretical system.
from cs.AI updates on arXiv.org http://ift.tt/29CX3Se
via IFTTT
Automatic Bridge Bidding Using Deep Reinforcement Learning. (arXiv:1607.03290v1 [cs.AI])
Bridge is among the zero-sum games for which artificial intelligence has not yet outperformed expert human players. The main difficulty lies in the bidding phase of bridge, which requires cooperative decision making under partial information. Existing artificial intelligence systems for bridge bidding rely on and are thus restricted by human-designed bidding systems or features. In this work, we propose a pioneering bridge bidding system without the aid of human domain knowledge. The system is based on a novel deep reinforcement learning model, which extracts sophisticated features and learns to bid automatically based on raw card data. The model includes an upper-confidence-bound algorithm and additional techniques to achieve a balance between exploration and exploitation. Our experiments validate the promising performance of our proposed model. In particular, the model advances from having no knowledge about bidding to achieving superior performance when compared with a champion-winning computer bridge program that implements a human-designed bidding system.
from cs.AI updates on arXiv.org http://ift.tt/2a7pVQS
via IFTTT
Populations can be essential in tracking dynamic optima. (arXiv:1607.03317v1 [cs.NE])
Real-world optimisation problems are often dynamic. Previously good solutions must be updated or replaced due to changes in objectives and constraints. It is often claimed that evolutionary algorithms are particularly suitable for dynamic optimisation because a large population can contain different solutions that may be useful in the future. However, rigorous theoretical demonstrations for how populations in dynamic optimisation can be essential are sparse and restricted to special cases.
This paper provides theoretical explanations of how populations can be essential in evolutionary dynamic optimisation in a general and natural setting. We describe a natural class of dynamic optimisation problems where a sufficiently large population is necessary to keep track of moving optima reliably. We establish a relationship between the population-size and the probability that the algorithm loses track of the optimum.
from cs.AI updates on arXiv.org http://ift.tt/29CWPKK
via IFTTT
Extended Graded Modalities in Strategy Logic. (arXiv:1607.03354v1 [cs.GT])
Strategy Logic (SL) is a logical formalism for strategic reasoning in multi-agent systems. Its main feature is that it has variables for strategies that are associated to specific agents with a binding operator. We introduce Graded Strategy Logic (GradedSL), an extension of SL by graded quantifiers over tuples of strategy variables, i.e., "there exist at least g different tuples (x_1,...,x_n) of strategies" where g is a cardinal from the set N union {aleph_0, aleph_1, 2^aleph_0}. We prove that the model-checking problem of GradedSL is decidable. We then turn to the complexity of fragments of GradedSL. When the g's are restricted to finite cardinals, written GradedNSL, the complexity of model-checking is no harder than for SL, i.e., it is non-elementary in the quantifier rank. We illustrate our formalism by showing how to count the number of different strategy profiles that are Nash equilibria (NE), or subgame-perfect equilibria (SPE). By analyzing the structure of the specific formulas involved, we conclude that the important problems of checking for the existence of a unique NE or SPE can both be solved in 2ExpTime, which is not harder than merely checking for the existence of such equilibria.
from cs.AI updates on arXiv.org http://ift.tt/2a7pUMO
via IFTTT
A New Learning Method for Inference Accuracy, Core Occupation, and Performance Co-optimization on TrueNorth Chip. (arXiv:1604.00697v2 [cs.NE] UPDATED)
IBM TrueNorth chip uses digital spikes to perform neuromorphic computing and achieves ultrahigh execution parallelism and power efficiency. However, in TrueNorth chip, low quantization resolution of the synaptic weights and spikes significantly limits the inference (e.g., classification) accuracy of the deployed neural network model. Existing workaround, i.e., averaging the results over multiple copies instantiated in spatial and temporal domains, rapidly exhausts the hardware resources and slows down the computation. In this work, we propose a novel learning method on TrueNorth platform that constrains the random variance of each computation copy and reduces the number of needed copies. Compared to the existing learning method, our method can achieve up to 68.8% reduction of the required neuro-synaptic cores or 6.5X speedup, with even slightly improved inference accuracy.
from cs.AI updates on arXiv.org http://ift.tt/227J7AB
via IFTTT
Iterative Judgment Aggregation. (arXiv:1604.06356v3 [cs.AI] UPDATED)
Judgment aggregation problems form a class of collective decision-making problems represented in an abstract way, subsuming some well known problems such as voting. A collective decision can be reached in many ways, but a direct one-step aggregation of individual decisions is arguably most studied. Another way to reach collective decisions is by iterative consensus building -- allowing each decision-maker to change their individual decision in response to the choices of the other agents until a consensus is reached. Iterative consensus building has so far only been studied for voting problems. Here we propose an iterative judgment aggregation algorithm, based on movements in an undirected graph, and we study for which instances it terminates with a consensus. We also compare the computational complexity of our iterative procedure with that of related judgment aggregation operators.
from cs.AI updates on arXiv.org http://ift.tt/1YJEOuu
via IFTTT
[FD] [RCESEC-2016-004][CVE-2016-5005] Apache Archiva 1.3.9 admin/addProxyConnector_commit.action connector.sourceRepoId Persistent Cross-Site Scripting

XSS
Are you sure you want to delete proxy connector [ XSS , maven2-repository.dev.java.net ] ?
Source: Gmail -> IFTTT-> Blogger
[FD] [RCESEC-2016-003][CVE-2016-4469] Apache Archiva 1.3.9 Multiple Cross-Site Request Forgeries
Source: Gmail -> IFTTT-> Blogger
[FD] WSO2 SOA Enablement Server - Reflected Cross Site Scripting vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] WSO2 SOA Enablement Server - XML External Entity Injection
Source: Gmail -> IFTTT-> Blogger
[FD] WSO2 SOA Enablement Server - Server Side Request Forgery
Source: Gmail -> IFTTT-> Blogger
[FD] RCE by abusing NAC to gain Domain Persistence.
Source: Gmail -> IFTTT-> Blogger
[FD] RootExplorer remote code execution
Source: Gmail -> IFTTT-> Blogger
Warning: Millions of Xiaomi Phones Vulnerable to Remote Hacking
from The Hacker News http://ift.tt/29UEydS
via IFTTT
Doesn't work in Chrome anonymous mode
from Google Alert - anonymous http://ift.tt/29BvnL3
via IFTTT
[FD] Easy Forms for MailChimp Local File Inclusion vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] WP Fastest Cache Member Local File Inclusion vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] Cross-Site Scripting vulnerability in Profile Builder WordPress Plugin
Source: Gmail -> IFTTT-> Blogger
[FD] Cross-Site Scripting vulnerability in Master Slider WordPress Plugin
Source: Gmail -> IFTTT-> Blogger
[FD] Cross-Site Scripting vulnerability in Email Users WordPress Plugin
Source: Gmail -> IFTTT-> Blogger
How to run Graphical Ubuntu Linux from Bash Shell in Windows 10
from The Hacker News http://ift.tt/29BSiIr
via IFTTT
Only authenticated user can create anotations and anonymous users can view the created anotations
from Google Alert - anonymous http://ift.tt/29vf1mO
via IFTTT
I have a new follower on Twitter
Zip Code
Zip Code Wilmington is an employer-driven code school teaching the exact skills that #fortune500 employers need. #Java in 12 wks. Paid apprenticeships available
Wilmington, DE
http://t.co/nOPpLep0gZ
Following: 4566 - Followers: 5782
July 12, 2016 at 08:21AM via Twitter http://twitter.com/zipcodewilm
ISS Daily Summary Report – 07/11/16
from ISS On-Orbit Status Report http://ift.tt/2a5m72E
via IFTTT
I have a new follower on Twitter
InsightBrief
Short documents for busy professionals, summarising longer reports & events so that readers can swiftly become acquainted with a larger body of knowledge.
London
http://t.co/jHIq9FJSrD
Following: 13278 - Followers: 16740
July 12, 2016 at 07:35AM via Twitter http://twitter.com/InsightBrief
accessing anonymous json object
from Google Alert - anonymous http://ift.tt/29T4QgX
via IFTTT
Uh-Oh! Pokémon GO grants itself 'Full Access' to your Google Account — Fix It NOW
from The Hacker News http://ift.tt/29FiSRp
via IFTTT
Re: [giampaolo/psutil] Extend open_files (#859)
Source: Gmail -> IFTTT-> Blogger
Lambda (anonymous/first class procedures) and custom reporters
from Google Alert - anonymous http://ift.tt/29AT1IF
via IFTTT
I have a new follower on Twitter
Steph Nissen
Social Media Marketer for Small Biz and Startups, CEO @Nissen_Media, @AgoraPulse Writer, Proud #Mompreneur and #SproutAllStar!
St Louis, MO
https://t.co/P5O7yHnzmq
Following: 15389 - Followers: 20346
July 12, 2016 at 02:04AM via Twitter http://twitter.com/stephnissen_
Aurorae on Jupiter
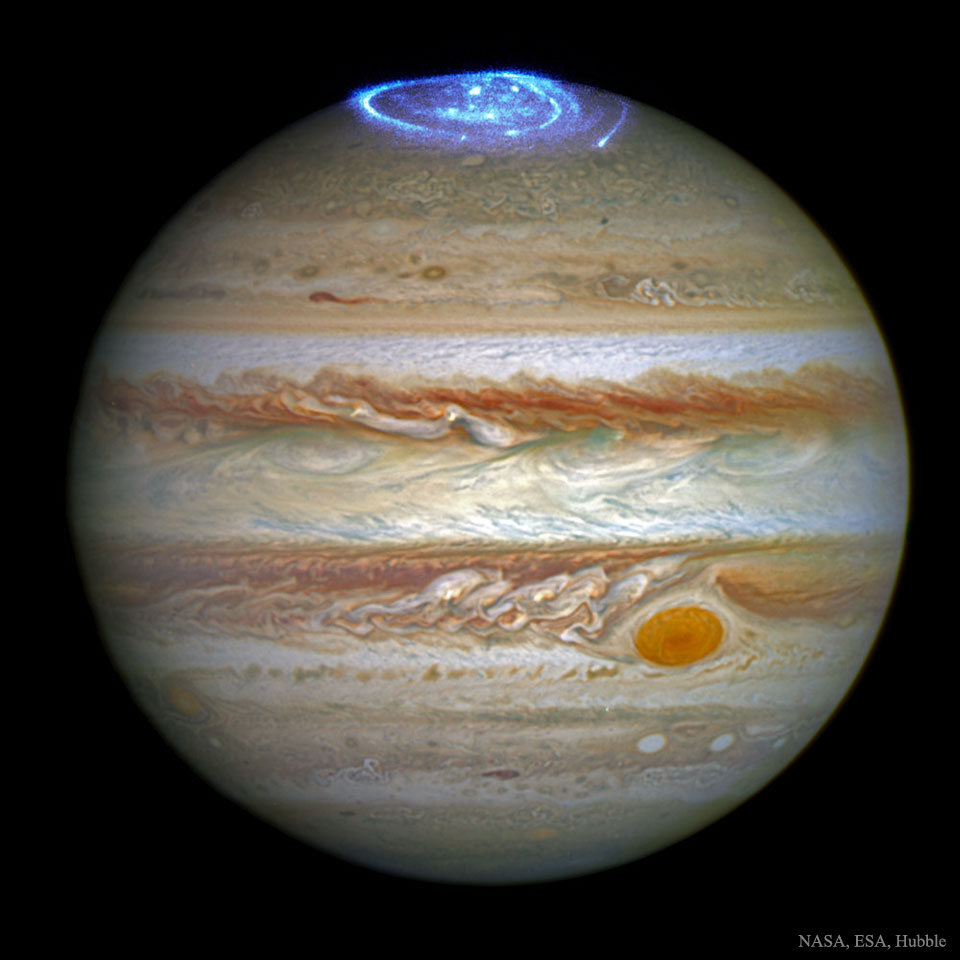
Monday, July 11, 2016
Home Run Derby: Mark Trumbo (13 HR) eliminated by Marlins' Giancarlo Stanton (17 HR) in the semifinals (ESPN)
via IFTTT
I have a new follower on Twitter
Clarissa Wilson
I'm Clarissa Wilson, a money relationship coach, helping women develop their relationship with their money for financial freedom.
PA, USA
http://t.co/7DhftF1moK
Following: 2773 - Followers: 3108
July 11, 2016 at 09:50PM via Twitter http://twitter.com/clarissaawilson
Home Run Derby: Giancarlo Stanton vs. Mark Trumbo, Todd Frazier vs. Adam Duvall in semifinals; watch live in ESPN App (ESPN)
via IFTTT
Coach K explains his anonymous social media accounts
from Google Alert - anonymous http://ift.tt/29DeLGp
via IFTTT
Home Run Derby Video: Mark Trumbo uncorks mammoth blasts into the upper decks in 1st-round victory over Corey Seager (ESPN)
via IFTTT
Analysis of opinionated text for opinion mining. (arXiv:1607.02576v1 [cs.CL])
In sentiment analysis, the polarities of the opinions expressed on an object/feature are determined to assess the sentiment of a sentence or document whether it is positive/negative/neutral. Naturally, the object/feature is a noun representation which refers to a product or a component of a product, let us say, the "lens" in a camera and opinions emanating on it are captured in adjectives, verbs, adverbs and noun words themselves. Apart from such words, other meta-information and diverse effective features are also going to play an important role in influencing the sentiment polarity and contribute significantly to the performance of the system. In this paper, some of the associated information/meta-data are explored and investigated in the sentiment text. Based on the analysis results presented here, there is scope for further assessment and utilization of the meta-information as features in text categorization, ranking text document, identification of spam documents and polarity classification problems.
from cs.AI updates on arXiv.org http://ift.tt/29JF3Ii
via IFTTT
Augmenting Supervised Emotion Recognition with Rule-Based Decision Model. (arXiv:1607.02660v1 [cs.HC])
The aim of this research is development of rule based decision model for emotion recognition. This research also proposes using the rules for augmenting inter-corporal recognition accuracy in multimodal systems that use supervised learning techniques. The classifiers for such learning based recognition systems are susceptible to over fitting and only perform well on intra-corporal data. To overcome the limitation this research proposes using rule based model as an additional modality. The rules were developed using raw feature data from visual channel, based on human annotator agreement and existing studies that have attributed movement and postures to emotions. The outcome of the rule evaluations was combined during the decision phase of emotion recognition system. The results indicate rule based emotion recognition augment recognition accuracy of learning based systems and also provide better recognition rate across inter corpus emotion test data.
from cs.AI updates on arXiv.org http://ift.tt/29L82Zh
via IFTTT
Extending Weakly-Sticky Datalog+/-: Query-Answering Tractability and Optimizations. (arXiv:1607.02682v1 [cs.DB])
Weakly-sticky (WS) Datalog+/- is an expressive member of the family of Datalog+/- programs that is based on the syntactic notions of stickiness and weak-acyclicity. Query answering over the WS programs has been investigated, but there is still much work to do on the design and implementation of practical query answering (QA) algorithms and their optimizations. Here, we study sticky and WS programs from the point of view of the behavior of the chase procedure, extending the stickiness property of the chase to that of generalized stickiness of the chase (gsch-property). With this property we specify the semantic class of GSCh programs, which includes sticky and WS programs, and other syntactic subclasses that we identify. In particular, we introduce joint-weakly-sticky (JWS) programs, that include WS programs. We also propose a bottom-up QA algorithm for a range of subclasses of GSCh. The algorithm runs in polynomial time (in data) for JWS programs. Unlike the WS class, JWS is closed under a general magic-sets rewriting procedure for the optimization of programs with existential rules. We apply the magic-sets rewriting in combination with the proposed QA algorithm for the optimization of QA over JWS programs.
from cs.AI updates on arXiv.org http://ift.tt/29JEOwP
via IFTTT