Latest YouTube Video
Saturday, March 10, 2018
Anonymous Creativity
from Google Alert - anonymous http://ift.tt/2FHkWsE
via IFTTT
telegram anonymous chat
from Google Alert - anonymous http://ift.tt/2DgF53a
via IFTTT
Anonymous pastebin
from Google Alert - anonymous http://ift.tt/2p4BAbn
via IFTTT
Anonymous ddos attack download
from Google Alert - anonymous http://ift.tt/2IhCMku
via IFTTT
Friday, March 9, 2018
Disable creator/editor fields for a survey shared to a group or organization for anonymous survey
from Google Alert - anonymous http://ift.tt/2DfvB8u
via IFTTT
APT Hackers Infect Routers to Covertly Implant Slingshot Spying Malware
from The Hacker News http://ift.tt/2Fu8KIc
via IFTTT
GlobaLeaks The Software Enabling Secure and Anonymous
from Google Alert - anonymous http://ift.tt/2DewXQW
via IFTTT
Single mother by anonymous sperm donor no dad needed
from Google Alert - anonymous http://ift.tt/2IcgAYV
via IFTTT
Anonymous Recruiter
from Google Alert - anonymous http://ift.tt/2FqIHG4
via IFTTT
ISPs Caught Injecting Cryptocurrency Miners and Spyware In Some Countries
from The Hacker News http://ift.tt/2DdWud1
via IFTTT
Orioles: Manny Machado on list of players we'd love to see in Aaron Judge-less HR Derby field - Buster Olney (ESPN)
via IFTTT
[FD] DSA-2018-020: Dell EMC Data Protection Advisor Hardcoded Password Vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] Multiple SQL injection vulnerabilities in Bacula-Web (CVE-2017-15367)
| 5.7.19-0ubuntu0.16.04.1 | backupjob-report.php?backupjob_name= [...] Other parameters (eg. client_id) are also vulnerable, since there is no protection against SQL Injections at all. 2) The /backupjob-report.php script is affected by a SQL Injection vulnerability. The following GET request can be used to extract the result of "select @@version" query. Request: GET /client-report.php?period=7&client_id=21%20UNION%20ALL%20SELECT%20NULL,@@version%23 3) The /client-report.php is affected by a SQL Injection vulnerability in the "client_id" parameter. ## Vulnerability Disclosure Timeline 2017-08-01 - Vulnerabilities discovered by Cinta Infinita 2017-08-09 - Vulnerabilities reported to Bacula-Web 2017-08-09 - Vulnerabilities confirmed by Bacula-Web 2017-10-15 - CVE-2017-15367 is assigned 2017-10-16 - Bacula-Web fixes backupjob-report.php and client-report.php in dev branch 2018-03-02 - Bacula-Web fixes jobs.php in dev branch 2018-03-02 - Version 8.0.0-RC2 is published 2018-03-07 - Full disclosure ## Related fixes and releases http://ift.tt/2oXQT6l http://ift.tt/2Hk6fbV http://ift.tt/2oZ5Yo4 ## About Cinta Infinita Cinta Infinita offers Information Security related services. Our Headquarters are in Buenos Aires, Argentina. For more information, visit http://ift.tt/2tu3iUd Source: Gmail -> IFTTT-> Blogger |
[FD] Hola VPN 1.79.859 - Insecure service permissions
Source: Gmail -> IFTTT-> Blogger
[FD] WPS Free Office 10.2.0.5978 - NULL DACL grants full access
Source: Gmail -> IFTTT-> Blogger
[FD] Panda Global Security 17.0.1 - NULL DACL grants full access
Source: Gmail -> IFTTT-> Blogger
School district takes down anonymous tip line
from Google Alert - anonymous http://ift.tt/2tz8kii
via IFTTT
[FD] Panda Global Security 17.0.1 - Unquoted service path
Source: Gmail -> IFTTT-> Blogger
[FD] BitDefender Total Security 2018 - Insecure Pipe Permissions
Source: Gmail -> IFTTT-> Blogger
[FD] 10-Strike Network Monitor 5.4 - Unquoted Service Path
Source: Gmail -> IFTTT-> Blogger
[FD] WebLog Expert Web Server Enterprise v9.4 / Remote Denial Of Service CVE-2018-7582
Source: Gmail -> IFTTT-> Blogger
[FD] Tuleap SQL Injection
Source: Gmail -> IFTTT-> Blogger
[FD] WebLog Expert Web Server Enterprise v9.4 / Authentication Bypass CVE-2018-7581
Source: Gmail -> IFTTT-> Blogger
NFL Free Agency: Best and worst case scenarios for Ravens and rest of the league - Jamison Hensley (ESPN)
via IFTTT
waa %28we architech anonymous
from Google Alert - anonymous http://ift.tt/2oX2YIP
via IFTTT
ISS Daily Summary Report – 3/08/2018
from ISS On-Orbit Status Report http://ift.tt/2HkY2Vd
via IFTTT
Over 15,000 Memcached DDoS Attacks Hit 7100 Sites in Last 10 Days
from The Hacker News http://ift.tt/2FuVqn4
via IFTTT
Windows 10 'S Mode' Coming Soon — For Security and Performance
from The Hacker News http://ift.tt/2G8vm2b
via IFTTT
Horsehead: A Wider View

Thursday, March 8, 2018
Head Chef
from Google Alert - anonymous http://ift.tt/2G7YdDQ
via IFTTT
Plasterer in Chelmsford (CM1) | Anonymous
from Google Alert - anonymous http://ift.tt/2Fq0vgd
via IFTTT
How to set up a sweepstakes in an anonymous survey
from Google Alert - anonymous http://ift.tt/2FnLpvO
via IFTTT
ISS Daily Summary Report – 3/07/2018
from ISS On-Orbit Status Report http://ift.tt/2FzIkrU
via IFTTT
Alternatives to Alcoholics Anonymous Work as Well as 12-Step Programs
from Google Alert - anonymous http://ift.tt/2FBquVr
via IFTTT
New Cryptocurrency Mining Malware Infected Over 500,000 PCs in Just Few Hours
from The Hacker News http://ift.tt/2FE0rwI
via IFTTT
Hard-Coded Password in Cisco Software Lets Attackers Take Over Linux Servers
from The Hacker News http://ift.tt/2oZaLVT
via IFTTT
Why Jake Arrieta, Lance Lynn and Alex Cobb would be a good fit with Orioles - David Schoenfield (ESPN)
via IFTTT
Anonymous woman to donate up to $50 million of $559 million Powerball winnings to charities ...
from Google Alert - anonymous http://ift.tt/2FszkkW
via IFTTT
Anonymous woman to donate roughly $250000 of $559 million Powerball winnings to charities ...
from Google Alert - anonymous http://ift.tt/2Fiyrzo
via IFTTT
Anonymous
from Google Alert - anonymous http://ift.tt/2FmvkXe
via IFTTT
[FD] [RT-SA-2018-001] Arbitrary Redirect in Tuleap
Source: Gmail -> IFTTT-> Blogger
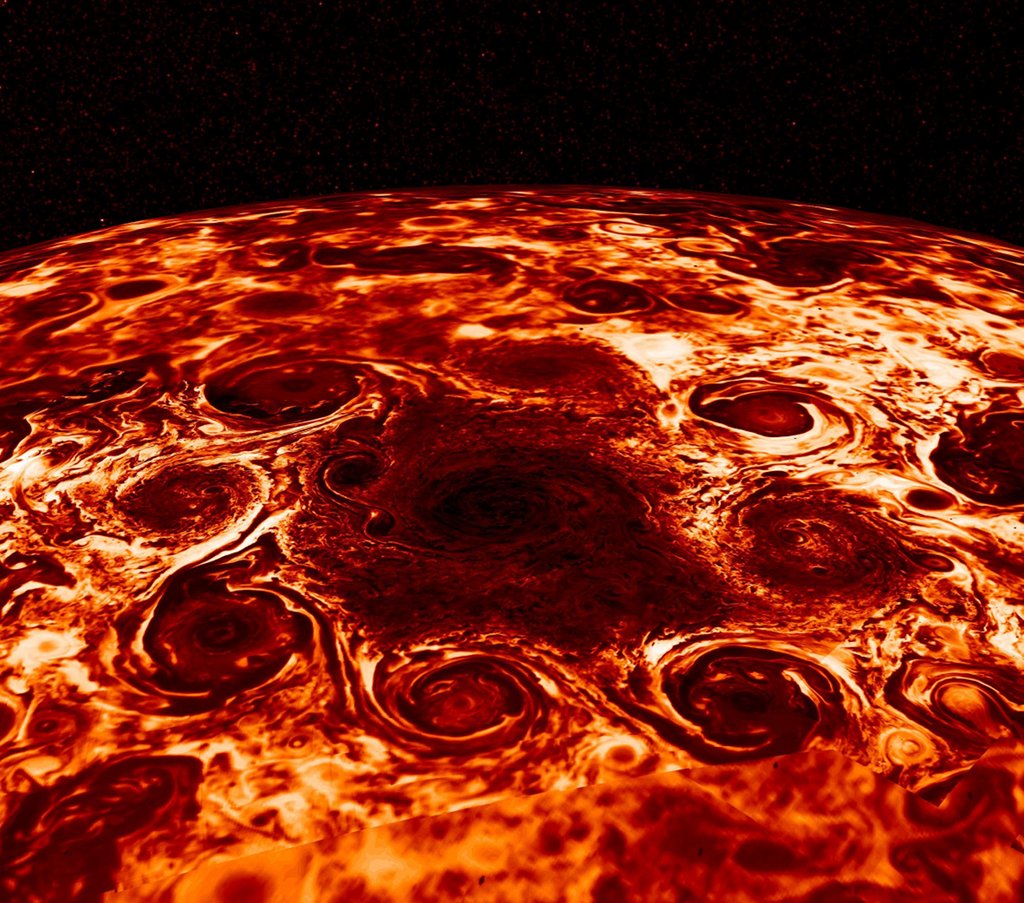
Cyclones at Jupiter s North Pole
Wednesday, March 7, 2018
Anonymous woman to donate up to $50 million of $559 million Powerball winnings to charities ...
from Google Alert - anonymous http://ift.tt/2oThTE5
via IFTTT
8th St.'s surf is Good
8th St. Summary
Surf: head high to 2 ft overhead
Maximum: 2.142m (7.03ft)
Minimum: 1.53m (5.02ft)
Maryland-Delaware Summary
from Surfline http://ift.tt/1kVmigH
via IFTTT
Anonymous woman to donate roughly $250000 of $559 million Powerball winnings to charities ...
from Google Alert - anonymous http://ift.tt/2FmvCNN
via IFTTT
Anonymous Powerball Winner's Lawyers Announce Donation
from Google Alert - anonymous http://ift.tt/2DasUF5
via IFTTT
China Duke Kunshan University|Medical Physics
from Google Alert - anonymous http://ift.tt/2Fmvz4z
via IFTTT
Anonymous Donors Challenge Eagle Nation to Support Athletics' Endowments
from Google Alert - anonymous http://ift.tt/2FlTnS9
via IFTTT
8th St.'s surf is Good
8th St. Summary
Surf: head high to 2 ft overhead
Maximum: 2.142m (7.03ft)
Minimum: 1.53m (5.02ft)
Maryland-Delaware Summary
from Surfline http://ift.tt/1kVmigH
via IFTTT
Memcached DDoS Exploit Code and List of 17,000 Vulnerable Servers Released
from The Hacker News http://ift.tt/2oOzGfw
via IFTTT
ISS Daily Summary Report – 3/06/2018
from ISS On-Orbit Status Report http://ift.tt/2G3tQOQ
via IFTTT
Predictions for every team's top free agent: Will Ravens re-sign C Ryan Jensen? (ESPN)
via IFTTT
Would Ravens shock everyone (including owner) and draft Baker Mayfield? - Jamison Hensley (ESPN)
via IFTTT
I have a new follower on Twitter

Fly Me Away
Drone enthusiast. 26. Aerial photographer and lover of life.
Asheville, NC
Following: 1798 - Followers: 2302
March 07, 2018 at 05:59AM via Twitter http://twitter.com/KingQuadcopter
Leaked NSA Dump Also Contains Tools Agency Used to Track Other Hackers
from The Hacker News http://ift.tt/2FvZGWr
via IFTTT
Finding Approximate Location of Anonymous Poster
from Google Alert - anonymous http://ift.tt/2HaQ3de
via IFTTT
Arcs, Jets, and Shocks near NGC 1999

Tuesday, March 6, 2018
The Taxes page is accessible over the web by anonymous
from Google Alert - anonymous http://ift.tt/2HaZYPL
via IFTTT
Anonymous - FOH & BOH Positions
from Google Alert - anonymous http://ift.tt/2Fnp1Pm
via IFTTT
[FD] DSA-2018-011: RSA Identity Governance and Lifecycle Privilege Escalation Vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] DSA-2018-038: RSA Archer GRC Platform Multiple Vulnerabilities
Source: Gmail -> IFTTT-> Blogger
[FD] Rapid Scada - 5.5.0 - Insecure Permissions
Source: Gmail -> IFTTT-> Blogger
[FD] DefenseCode Security Advisory: Magento Stored Cross-Site Scripting – Product Attributes
Source: Gmail -> IFTTT-> Blogger
[FD] DefenseCode Security Advisory: Magento Stored Cross-Site Scripting – Downloadable Products
Source: Gmail -> IFTTT-> Blogger
[FD] DefenseCode Security Advisory: Magento Multiple Stored Cross-Site Scripting Vulnerabilities
Source: Gmail -> IFTTT-> Blogger
[FD] DefenseCode Security Advisory: Magento Backups Cross-Site Request Forgery
Source: Gmail -> IFTTT-> Blogger
[FD] Softros Network Time System Server v2.3.4 / Denial Of Service CVE-2018-7658
Source: Gmail -> IFTTT-> Blogger
[FD] KL-001-2018-007 : Sophos UTM 9 loginuser Privilege Escalation via confd Service
Source: Gmail -> IFTTT-> Blogger
Calvin Ridley at No. 16? Ravens' pipe dream is suddenly a possibility - Jamison Hensley (ESPN)
via IFTTT
ISS Daily Summary Report – 3/05/2018
from ISS On-Orbit Status Report http://ift.tt/2oMy5Xv
via IFTTT
Anonymous Cart Migration to Existing User Cart
from Google Alert - anonymous http://ift.tt/2HdBfdH
via IFTTT
Run 'Kali Linux' Natively On Windows 10 — Just Like That!
from The Hacker News http://ift.tt/2oXqdC2
via IFTTT
Territory Manager
from Google Alert - anonymous http://ift.tt/2oLacjk
via IFTTT
1.7 Tbps DDoS Attack — Memcached UDP Reflections Set New Record
from The Hacker News http://ift.tt/2tjG5UH
via IFTTT
Colorful Airglow Bands Surround Milky Way

Monday, March 5, 2018
An improved anonymous authentication scheme for roaming in ubiquitous networks
from Google Alert - anonymous http://ift.tt/2oRNc1b
via IFTTT
New 4G LTE Network Attacks Let Hackers Spy, Track, Spoof and Spam
from The Hacker News http://ift.tt/2oRi2Xz
via IFTTT
NFL Insiders predict: Why Jimmy Graham will end up with Ravens - Dan Graziano (ESPN)
via IFTTT
ISS Daily Summary Report – 3/02/2018
from ISS On-Orbit Status Report http://ift.tt/2thSdWf
via IFTTT
600 Powerful Bitcoin-Mining Computers Worth $2 Million Stolen In Iceland
from The Hacker News http://ift.tt/2H6oOR5
via IFTTT
The 7 best deep learning books you should be reading right now

In today’s post I’m going to share with you the 7 best deep learning books (in no particular order) I have come across and would personally recommend you read.
Some of these deep learning books are heavily theoretical, focusing on the mathematics and associated assumptions behind neural networks and deep learning.
Other deep learning books are entirely practical and teach through code rather than theory.
And even other deep learning books straddle the line, giving you a healthy dose of theory while enabling you to “get your hands dirty” and learn by implementing (these tend to be my favorite deep learning books).
For each deep learning book I’ll discuss the core concepts covered, the target audience, and if the book is appropriate for you.
To discover the 7 best books for studying deep learning, just keep reading!
The 7 best deep learning books you should be reading right now
Before you choose a deep learning book, it’s best to assess your own personal learning style to ensure you get the most out of the book.
Start by asking yourself the following question:
How do I best learn? Do I like to learn from theoretical texts? Or do I like to learn from code snippets and implementation?
Everyone has their own personal learning style and your answers here will dictate which deep learning books you should be reading.
For me personally, I like to strike a balance between the two.
Deep learning books that are entirely theoretical and go too far into the abstract make it far too easy for my eyes to gloss over.
But on the other hand, if a deep learning book skips theory entirely and jumps straight into implementation, I know I’m missing out on core theoretical underpinnings that may help me approach a new deep learning problem or project.
In my opinion, a good deep learning book needs to carefully balance the two.
We need theory to help us understand the core fundamentals of deep learning — and at the same time we need implementation and code snippets to help us reinforce what we just learned.
 1. Deep Learning
1. Deep Learning
It’s hard (if not impossible) to write a blog post regarding the best deep learning books without mentioning Goodfellow, Bengio, and Courville’s Deep Learning text.
This book is meant to be a textbook used to teach the fundamentals and theory surrounding deep learning in a college-level classroom.
Goodfellow et al.’s Deep Learning is entirely theoretical and written for an academic audience. There is no code covered in the book.
The book starts with a discussion on machine learning basics, including the applied mathematics needed to effectively study deep learning (linear algebra, probability and information theory, etc.) from an academic perspective.
From there, the book moves into modern deep learning algorithms and techniques.
The final part of Deep Learning focuses more on current research trends and where the deep learning field is moving.
I’ve personally read through this book twice, cover to cover, and have found it incredibly valuable, provided you have the mathematical/academic rigor required for such a textbook.
Deep Learning is available for online viewing for free from the book’s homepage. You can purchase a hardcopy of the text from Amazon.
You should read this deep learning book if…
- You learn from theory rather than implementation
- You enjoy academic writing
- You are a professor, undergraduate, or graduate student doing work in deep learning
2. Neural Networks and Deep Learning
My second theory-based deep learning (e)book recommendation is Neural Networks and Deep Learning by Michael Nielsen.
The book does include some code but it’s important to underline the “some” — there are a total of seven Python scripts accompanying the book, all discussing a various fundamental machine learning, neural network, or deep learning technique on the MNIST dataset. The implementations are not the most “exciting” in the world, but they will help demonstrate some of the theoretical concepts in the text.
If you are new to machine learning and deep learning but are eager to dive into a theory-based learning approach, Nielsen’s book should be your first stop.
The book is a much quicker read than Goodfellow’s Deep Learning and Nielsen’s writing style combined with occasional code snippets makes it easier to work through.
You should read this deep learning book if…
- You are looking for a theory-based deep learning text
- Are new to machine learning/deep learning and want to approach the field from a more academic standpoint
 3. Deep Learning with Python
3. Deep Learning with Python
Francois Chollet, Google AI researcher and creator of the popular Keras deep learning library, published his book, Deep Learning with Python in October 2017.
Francois’ book takes a practitioner’s approach to deep learning. Some theory and discussion is included, but for every few paragraphs of theory, you’ll find a Keras implementation of the technique.
One of my favorite aspects of this book is how Francois includes examples for deep learning applied to computer vision, text, and sequences, making it a well rounded book for readers who want to learn the Keras library while studying machine learning and deep learning fundamentals.
I found Francois’ writing to be clear and accessible. His additional commentary on deep learning trends and history is phenomenal and insightful.
It’s important to note that this book is not meant to be a super deep dive into deep learning. Instead, it’s primary use is to teach you (1) the fundamentals of deep learning (2) through the Keras library (3) using practical examples in a variety of deep learning domains.
You should read this deep learning book if…
- You are interested in the Keras library
- You “learn by doing/implementing”
- You want a quick understanding of how deep learning is applied to various fields, such as computer vision, sequence learning, and text
4. Hands-On Machine Learning with Scikit-Learn and TensorFlow
When I first purchased a copy of Aurélien Géron’s Hands-on Machine Learning with Scikit-Learn and TensorFlow, I wasn’t sure what to expect — had the title not included the word “TensorFlow” I may have breezed right by it, thinking it was only a basic introduction to machine learning.
But at the same time, appending the word “TensorFlow” to an already lengthy title that seems to focus on basic machine learning made me think it was a cheap marketing tactic to sell more copies — everyone is interested in deep learning, right?
Luckily, I was wrong — the book is a good read and the title shouldn’t deter you from reading through it.
Géron’s deep learning book is organized in two parts.
The first part covers basic machine learning algorithms such as Support Vector Machines (SVMs), Decision, Trees, Random Forests, ensemble methods, and basic unsupervised learning algorithms. Scikit-learn examples for each of the algorithms are included.
The second part then covers elementary deep learning concepts through the TensorFlow library.
You should read this deep learning book if…
- You are new to machine learning and want to start with core principles with code examples
- You are interested in the popular scikit-learn machine learning library
- You want to quickly learn how to operate the TensorFlow library for basic deep learning tasks
5. TensorFlow Deep Learning Cookbook
If you like the “cookbook” style of teaching (little-to-no theory and lots of code), I would suggest taking a look at Gulli and Kapoor’s TensorFlow Deep Learning Cookbook.
This deep learning book is entirely hands-on and is a great reference for TensorFlow users.
Again, this book is not meant to necessarily teach deep learning, but instead show you how to operate the TensorFlow library in the context of deep learning.
Don’t get me wrong — you will absolutely learn new deep learning concepts, techniques, and algorithms along the way, but the book takes a heavy-handed cookbook approach: lots of code and explanations of what the code is doing.
My only criticism of the book is that there are some typos in the code snippets. This can be expected when writing a book that is entirely code focused. Typos happen, I can certainly attest to that. Just be aware of this when you are working through the text.
You should read this deep learning book if…
- You have already studied the fundamentals of deep learning
- You are interested in the TensorFlow library
- You enjoy the “cookbook” style of teaching where code is provided to solve a particular problem but the underlying theory is not discussed
6. Deep Learning: A Practitioners Approach
While most deep learning books that include code samples use Python, Adam Gibson and Josh Patterson’s Deep Learning: A Practitioners Approach instead use Java and the DL4J library.
Why Java?
Java is the most used programming language in large corporations, especially at the enterprise level.
The first few chapters in Gibson and Patterson’s book discuss basic machine learning and deep learning fundamentals. The rest of the book includes Java-based deep learning code examples using DL4J.
You should read this deep learning book if…
- You have a specific use case where the Java programming language needs to be utilized
- You work for a large company or enterprise organization where Java is primarily used
- You want to understand how to operate the DL4J library
7. Deep Learning for Computer Vision with Python
I’ll be completely honest and forthcoming and admit that I’m biased — I wrote Deep Learning for Computer Vision with Python.
That said, my book really has become one of the best deep learning and computer vision resources available today (take a look at this review and this one as well if you need an honest second opinion).
Francois Chollet, AI researcher at Google and creator of Keras, had this to say about my new deep learning book:
This book is a great, in-depth dive into practical deep learning for computer vision. I found it to be an approachable and enjoyable read: explanations are clear and highly detailed. You’ll find many practical tips and recommendations that are rarely included in other books or in university courses. I highly recommend it, both to practitioners and beginners. — Francois Chollet
And Adam Geitgey, the author of the popular Machine Learning is Fun! blog series, said this:
I highly recommend grabbing a copy of Deep Learning for Computer Vision with Python. It goes into a lot of detail and has tons of detailed examples. It’s the only book I’ve seen so far that covers both how things work and how to actually use them in the real world to solve difficult problems. Check it out! — Adam Geitgey
If you’re interested in studying deep learning applied to computer vision (image classification, object detection, image understanding, etc.), this is the perfect book for you.
Inside my book you will:
- Learn the foundations of machine learning and deep learning in an accessible manner that balances both theory and implementation
- Study advanced deep learning techniques, including object detection, multi-GPU training, transfer learning, and Generative Adversarial Networks (GANs)
- Replicate the results of state-of-the-art papers, including ResNet, SqueezeNet, VGGNet, and others on the 1.2 million ImageNet dataset
Furthermore, I provide the best possible balance of both theory and hands-on implementation. For each theoretical deep learning concept you’ll find an associated Python implementation to help you cement the knowledge.
Be sure to take a look — and while you’re checking out the book, don’t forget to grab your (free) table of contents + sample chapters PDF of the book.
You should read this deep learning book if…
- You are specifically interested in deep learning applied to computer vision and image understanding
- You want an excellent balance between theory and implementation
- You want a deep learning book that makes seemingly complicated algorithms and techniques easy to grasp and understand
- You want a clear, easy to follow book to guide you on your path to deep learning mastery
Summary
In this post you discovered my seven favorite books for studying deep learning.
Have you purchased or read through one of these books? If so, leave a comment and let me know what you think of it.
Did I miss a book that you think should be on this list? If so, be sure to contact me or leave a comment.
The post The 7 best deep learning books you should be reading right now appeared first on PyImageSearch.
from PyImageSearch http://ift.tt/2FfB9la
via IFTTT
anonymous-php/containers
from Google Alert - anonymous http://ift.tt/2oPe5mc
via IFTTT
FICTION_L Digest - 28 Feb 2018 to 4 Mar 2018 (#2018-39)
Source: Gmail -> IFTTT-> Blogger
Slow Arrow
from Google Alert - anonymous http://ift.tt/2oGSSvE
via IFTTT
Sunday, March 4, 2018
EventSubscriber not run on Cached pages for Anonymous users
from Google Alert - anonymous http://ift.tt/2FSl0Dl
via IFTTT
Anonymous UBC
from Google Alert - anonymous http://ift.tt/2FdcJJd
via IFTTT
Clouds, Birds, Moon, Venus

anonymous 75x75
from Google Alert - anonymous http://ift.tt/2tjpznK
via IFTTT