Latest YouTube Video
Saturday, April 23, 2016
Orioles Video: Chris Davis crushes a solo shot to deep left field for his 6th homer of the season in 8-3 win vs. Royals (ESPN)
via IFTTT
DARPA Wants To Build Ultra Secure Messaging App for US Military
from The Hacker News http://ift.tt/1YNOlkt
via IFTTT
Orioles: P Yovani Gallardo (right shoulder bicep tendonitis) placed on 15-day DL; P Brian Matusz activated from DL (ESPN)
via IFTTT
Bank with No Firewall. That's How Hackers Managed to Steal $80 Million
from The Hacker News http://ift.tt/1YMrTIk
via IFTTT
Luohan #2 =. anonymous artist - Picture of Royal Ontario Museum, Toronto
from Google Alert - anonymous http://ift.tt/1SAoECc
via IFTTT
NGC 7635: The Bubble Nebula

Friday, April 22, 2016
I have a new follower on Twitter
Will Corry
Will Corry. Ex MD of Thomson Publications and Trade Fairs and Promotions, South Africa. Now his pride and joy - theMarketingblog in the UK
Englefield Green, UK
https://t.co/Swelrn2rVV
Following: 5924 - Followers: 8330
April 22, 2016 at 09:16PM via Twitter http://twitter.com/slievemore
I have a new follower on Twitter
3degreeZ Marketing
We fill up your Sales Funnel!
Fort Lauderdale, FL
https://t.co/5VR9RODfTJ
Following: 3330 - Followers: 3778
April 22, 2016 at 09:16PM via Twitter http://twitter.com/3degreezM
Lead Generation for Anonymous News/Secrets/Gossip app
from Google Alert - anonymous http://ift.tt/1U9br5K
via IFTTT
Hacker Installed a Secret Backdoor On Facebook Server to Steal Passwords
from The Hacker News http://ift.tt/1WL2Mad
via IFTTT
More than 1 million People now access Facebook Over Tor Network
from The Hacker News http://ift.tt/1WKJz8R
via IFTTT
Unable to enable anonymous logins with Business Glossary Anywhere version 11.3
from Google Alert - anonymous http://ift.tt/214GXmk
via IFTTT
This anonymous Twitter account keeps leaking the NFL's biggest news
from Google Alert - anonymous http://ift.tt/1YKQzRB
via IFTTT
Sony PlayStation Network to Get Two-Factor Authentication
from The Hacker News http://ift.tt/1XMtuxv
via IFTTT
ISS Daily Summary Report 04/21/16
from ISS On-Orbit Status Report http://ift.tt/1Wh5FPD
via IFTTT
I have a new follower on Twitter
Joy Lierman
Psychology and English student | Tree Hugger | Madridista
Following: 191 - Followers: 98
April 22, 2016 at 08:03AM via Twitter http://twitter.com/Joy207890
[FD] SEC Consult SA-20160422-1 :: Multiple vulnerabilities in Digitalstrom Konfigurator
Source: Gmail -> IFTTT-> Blogger
[FD] SEC Consult SA-20160422-0 :: Insecure credential storage in my devolo Android app
Source: Gmail -> IFTTT-> Blogger
FBI paid Hacker $1.3 Million to Unlock San Bernardino Shooter's iPhone
from The Hacker News http://ift.tt/26iTs1G
via IFTTT
Permission Setting for Anonymous User doesn't work
from Google Alert - anonymous http://ift.tt/1r3lA8P
via IFTTT
The Anonymous De Rebus Bellicis and the Ethics of Empire in Late Antiquity
from Google Alert - anonymous http://ift.tt/246s3hh
via IFTTT
The Comet the Owl and the Galaxy

Thursday, April 21, 2016
Task scheduling system for UAV operations in indoor environment. (arXiv:1604.06223v1 [cs.AI])
Application of UAV in indoor environment is emerging nowadays due to the advancements in technology. UAV brings more space-flexibility in an occupied or hardly-accessible indoor environment, e.g., shop floor of manufacturing industry, greenhouse, nuclear powerplant. UAV helps in creating an autonomous manufacturing system by executing tasks with less human intervention in time-efficient manner. Consequently, a scheduler is one essential component to be focused on; yet the number of reported studies on UAV scheduling has been minimal. This work proposes a methodology with a heuristic (based on Earliest Available Time algorithm) which assigns tasks to UAVs with an objective of minimizing the makespan. In addition, a quick response towards uncertain events and a quick creation of new high-quality feasible schedule are needed. Hence, the proposed heuristic is incorporated with Particle Swarm Optimization (PSO) algorithm to find a quick near optimal schedule. This proposed methodology is implemented into a scheduler and tested on a few scales of datasets generated based on a real flight demonstration. Performance evaluation of scheduler is discussed in detail and the best solution obtained from a selected set of parameters is reported.
from cs.AI updates on arXiv.org http://ift.tt/1U7QEPT
via IFTTT
A Deliberation Procedure for Judgment Aggregation Problems. (arXiv:1604.06356v1 [cs.AI])
Judgment aggregation problems are a class of collective decision-making problems represented in an abstract way, subsuming some well known collective decision-making problems such voting problems. A collective decision can be reached either by aggregation of individual decisions or by deliberation -- allowing each decision-maker to change their individual decision in response to the individual decisions the other decision-makers made in the previous step. Impossibility results exist for judgment aggregation operators, voting operators, and judgment deliberation operators. However, while specific aggregation operators were constructed for aggregation of judgments and votes, deliberation procedures have only been studied for voting problems. Here we propose a deliberation procedure for judgment aggregation, based on movements in an undirected graph, and we study for which instances it produces a consensus. We also compare the computational complexity of our deliberation procedure with that of related judgment aggregation operators.
from cs.AI updates on arXiv.org http://ift.tt/1YJEOuu
via IFTTT
Computing rational decisions in extensive games with limited foresight. (arXiv:1502.03683v5 [cs.AI] UPDATED)
We introduce a class of extensive form games where players might not be able to foresee the possible consequences of their decisions and form a model of their opponents which they exploit to achieve a more profitable outcome. We improve upon existing models of games with limited foresight, endowing players with the ability of higher-order reasoning and proposing a novel solution concept to address intuitions coming from real game play. We analyse the resulting equilibria, devising an effective procedure to compute them.
from cs.AI updates on arXiv.org http://ift.tt/1D1Dwnu
via IFTTT
Norm Monitoring under Partial Action Observability. (arXiv:1505.03996v2 [cs.MA] UPDATED)
In the context of using norms for controlling multi-agent systems, a vitally important question that has not yet been addressed in the literature is the development of mechanisms for monitoring norm compliance under partial action observability. This paper proposes the reconstruction of unobserved actions to tackle this problem. In particular, we formalise the problem of reconstructing unobserved actions, and propose an information model and algorithms for monitoring norms under partial action observability using two different processes for reconstructing unobserved actions. Our evaluation shows that reconstructing unobserved actions increases significantly the number of norm violations and fulfilments detected.
from cs.AI updates on arXiv.org http://ift.tt/1FscsjI
via IFTTT
Orioles: 3B Manny Machado should be in the conversation for best player in baseball with Mike Trout Bryce Harper - Matz (ESPN)
via IFTTT
Alcoholics Anonymous: Family
from Google Alert - anonymous http://ift.tt/1SwXTP5
via IFTTT
Ravens: N.D. OT Ronnie Stanley goes 6th in Todd McShay's Mock Draft 5.0; Jamison Hensley says it \"comes as a surprise\" (ESPN)
via IFTTT
[FD] CVE-2016-3074: libgd: signedness vulnerability
Source: Gmail -> IFTTT-> Blogger
how to moderate topic for anonymous users
from Google Alert - anonymous http://ift.tt/1YJfrsZ
via IFTTT
user.role.anonymous.yml
from Google Alert - anonymous http://ift.tt/1SyzaNu
via IFTTT
Encrypted Smartphone Network Seized by Dutch Police for Criminal Investigation
from The Hacker News http://ift.tt/1MKPg4e
via IFTTT
[FD] Wordpress iThemes Security (Better WP Security) Insecure Backup/Logfile Generation (access rights)
Source: Gmail -> IFTTT-> Blogger
[FD] Time-based SQL Injection in Admin panel ImpressCMS <= v1.3.9
Source: Gmail -> IFTTT-> Blogger
Alcoholics Anonymous: Friends
from Google Alert - anonymous http://ift.tt/1SmSS9s
via IFTTT
moderation anonymous frontend
from Google Alert - anonymous http://ift.tt/1rpN5tz
via IFTTT
'Anonymous' Weeden Focuses on Blocks
from Google Alert - anonymous http://ift.tt/1SmSRT7
via IFTTT
ISS Daily Summary Report 04/20/16
from ISS On-Orbit Status Report http://ift.tt/1QpHkQz
via IFTTT
Opera Browser Now Offers Free and Unlimited Built-in VPN Service
from The Hacker News http://ift.tt/1TkK6ey
via IFTTT
CMA Meeting Directory
from Google Alert - anonymous http://ift.tt/20ZMRVZ
via IFTTT
Creators of SpyEye Virus Sentenced to 24 Years in Prison
from The Hacker News http://ift.tt/1pjR5tA
via IFTTT
Galaxy Einstein Ring
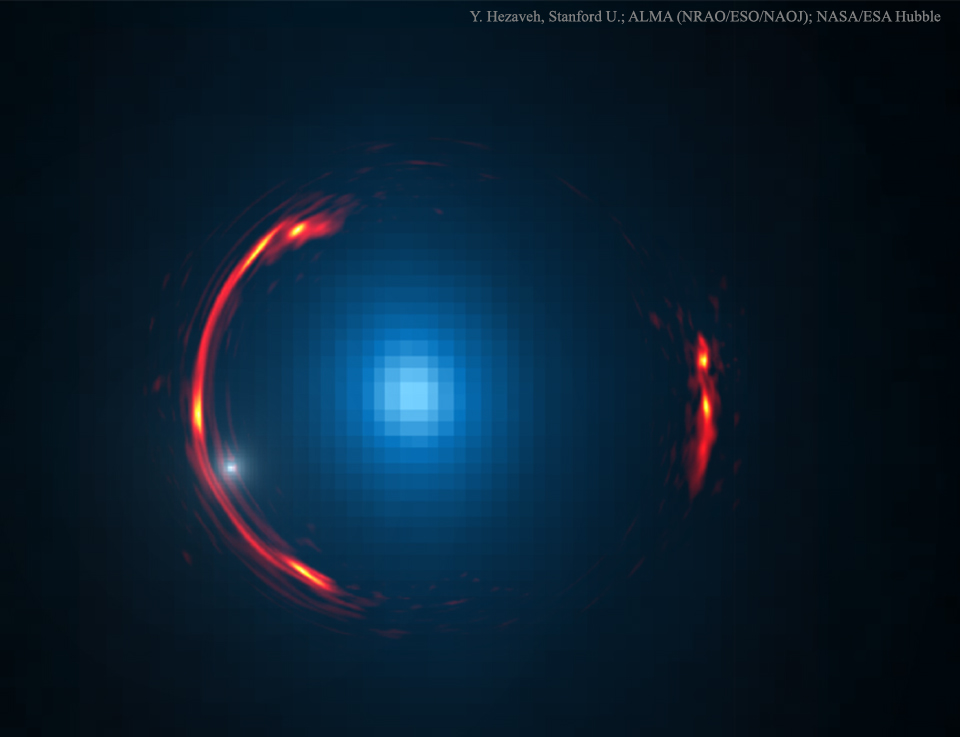
Wednesday, April 20, 2016
Orioles Video: Adam Jones lays out to make a diving catch robbing Jose Bautista of RBI in 4-3 victory vs. the Blue Jays (ESPN)
via IFTTT
I have a new follower on Twitter
Cortney Sargent, Sr.
Proud father, husband, radio host, and entrepreneur. Founder/lead designer of Sargent Branding Firm. https://t.co/8gV7gxbwC9
Tupelo, MS
https://t.co/KXfU5mQdS2
Following: 1288 - Followers: 1529
April 20, 2016 at 08:49PM via Twitter http://twitter.com/cortneyssargent
Procedural urban environments for FPS games. (arXiv:1604.05791v1 [cs.AI])
This paper presents a novel approach to procedural generation of urban maps for First Person Shooter (FPS) games. A multi-agent evolutionary system is employed to place streets, buildings and other items inside the Unity3D game engine, resulting in playable video game levels. A computational agent is trained using machine learning techniques to capture the intent of the game designer as part of the multi-agent system, and to enable a semi-automated aesthetic selection for the underlying genetic algorithm.
from cs.AI updates on arXiv.org http://ift.tt/1Qoq527
via IFTTT
Estimating 3D Trajectories from 2D Projections via Disjunctive Factored Four-Way Conditional Restricted Boltzmann Machines. (arXiv:1604.05865v1 [cs.CV])
Estimation, recognition, and near-future prediction of 3D trajectories based on their two dimensional projections available from one camera source is an exceptionally difficult problem due to uncertainty in the trajectories and environment, high dimensionality of the specific trajectory states, lack of enough labeled data and so on. In this article, we propose a solution to solve this problem based on a novel deep learning model dubbed Disjunctive Factored Four-Way Conditional Restricted Boltzmann Machine (DFFW-CRBM). Our method improves state-of-the-art deep learning techniques for high dimensional time-series modeling by introducing a novel tensor factorization capable of driving forth order Boltzmann machines to considerably lower energy levels, at no computational costs. DFFW-CRBMs are capable of accurately estimating, recognizing, and performing near-future prediction of three-dimensional trajectories from their 2D projections while requiring limited amount of labeled data. We evaluate our method on both simulated and real-world data, showing its effectiveness in predicting and classifying complex ball trajectories and human activities.
from cs.AI updates on arXiv.org http://ift.tt/20YUmMT
via IFTTT
A Factorization Machine Framework for Testing Bigram Embeddings in Knowledgebase Completion. (arXiv:1604.05878v1 [cs.CL])
Embedding-based Knowledge Base Completion models have so far mostly combined distributed representations of individual entities or relations to compute truth scores of missing links. Facts can however also be represented using pairwise embeddings, i.e. embeddings for pairs of entities and relations. In this paper we explore such bigram embeddings with a flexible Factorization Machine model and several ablations from it. We investigate the relevance of various bigram types on the fb15k237 dataset and find relative improvements compared to a compositional model.
from cs.AI updates on arXiv.org http://ift.tt/1Qoq7aa
via IFTTT
Multiplayer Games for Learning Multirobot Coordination Algorithms. (arXiv:1604.05942v1 [cs.RO])
Humans have an impressive ability to solve complex coordination problems in a fully distributed manner. This ability, if learned as a set of distributed multirobot coordination strategies, can enable programming large groups of robots to collaborate towards complex coordination objectives in a way similar to humans. Such strategies would offer robustness, adaptability, fault-tolerance, and, importantly, distributed decision-making. To that end, we have designed a networked gaming platform to investigate human group behavior, specifically in solving complex collaborative coordinated tasks. Through this platform, we are able to limit the communication, sensing, and actuation capabilities provided to the players. With the aim of learning coordination algorithms for robots in mind, we define these capabilities to mimic those of a simple ground robot.
from cs.AI updates on arXiv.org http://ift.tt/1NCcHYs
via IFTTT
A topological insight into restricted Boltzmann machines. (arXiv:1604.05978v1 [cs.NE])
Restricted Boltzmann Machines (RBMs) and models derived from them have been successfully used as basic building blocks in deep artificial neural networks for automatic features extraction, unsupervised weights initialization, but also as density estimators. Thus, their generative and discriminative capabilities, but also their computational time are instrumental to a wide range of applications. Our main contribution is to look at RBMs from a topological perspective, bringing insights from network science. Firstly, here we show that RBMs and Gaussian RBMs (GRBMs) are bipartite graphs which naturally have a small-world topology. Secondly, we demonstrate both on synthetic and real-world databases that by constraining RBMs and GRBMs to a scale-free topology (while still considering local neighborhoods and data distribution), we reduce the number of weights that need to be computed by a few orders of magnitude, at virtually no loss in generative performance. Thirdly, we show that, given the same number of weights, our proposed sparse models (which by design have a higher number of hidden neurons) achieve better generative capabilities than standard fully connected RBMs and GRBMs (which by design have a smaller number of hidden neurons) at no additional computational costs.
from cs.AI updates on arXiv.org http://ift.tt/1Sc5aoE
via IFTTT
Constructive Preference Elicitation by Setwise Max-margin Learning. (arXiv:1604.06020v1 [stat.ML])
In this paper we propose an approach to preference elicitation that is suitable to large configuration spaces beyond the reach of existing state-of-the-art approaches. Our setwise max-margin method can be viewed as a generalization of max-margin learning to sets, and can produce a set of "diverse" items that can be used to ask informative queries to the user. Moreover, the approach can encourage sparsity in the parameter space, in order to favor the assessment of utility towards combinations of weights that concentrate on just few features. We present a mixed integer linear programming formulation and show how our approach compares favourably with Bayesian preference elicitation alternatives and easily scales to realistic datasets.
from cs.AI updates on arXiv.org http://ift.tt/1Tk3Kr9
via IFTTT
Hierarchical Deep Reinforcement Learning: Integrating Temporal Abstraction and Intrinsic Motivation. (arXiv:1604.06057v1 [cs.LG])
Learning goal-directed behavior in environments with sparse feedback is a major challenge for reinforcement learning algorithms. The primary difficulty arises due to insufficient exploration, resulting in an agent being unable to learn robust value functions. Intrinsically motivated agents can explore new behavior for its own sake rather than to directly solve problems. Such intrinsic behaviors could eventually help the agent solve tasks posed by the environment. We present hierarchical-DQN (h-DQN), a framework to integrate hierarchical value functions, operating at different temporal scales, with intrinsically motivated deep reinforcement learning. A top-level value function learns a policy over intrinsic goals, and a lower-level function learns a policy over atomic actions to satisfy the given goals. h-DQN allows for flexible goal specifications, such as functions over entities and relations. This provides an efficient space for exploration in complicated environments. We demonstrate the strength of our approach on two problems with very sparse, delayed feedback: (1) a complex discrete MDP with stochastic transitions, and (2) the classic ATARI game `Montezuma's Revenge'.
from cs.AI updates on arXiv.org http://ift.tt/1Qoq3Yd
via IFTTT
Question Answering via Integer Programming over Semi-Structured Knowledge. (arXiv:1604.06076v1 [cs.AI])
Answering science questions posed in natural language is an important AI challenge. Answering such questions often requires non-trivial inference and knowledge that goes beyond factoid retrieval. Yet, most systems for this task are based on relatively shallow Information Retrieval (IR) and statistical correlation techniques operating on large unstructured corpora. We propose a structured inference system for this task, formulated as an Integer Linear Program (ILP), that answers natural language questions using a semi-structured knowledge base derived from text, including questions requiring multi-step inference and a combination of multiple facts. On a dataset of real, unseen science questions, our system significantly outperforms (+14%) the best previous attempt at structured reasoning for this task, which used Markov Logic Networks (MLNs). It also improves upon a previous ILP formulation by 17.7%. When combined with unstructured inference methods, the ILP system significantly boosts overall performance (+10%). Finally, we show our approach is substantially more robust to a simple answer perturbation compared to statistical correlation methods.
from cs.AI updates on arXiv.org http://ift.tt/23KxANJ
via IFTTT
The Backtracking Survey Propagation Algorithm for Solving Random K-SAT Problems. (arXiv:1508.05117v3 [cs.CC] UPDATED)
Satisfiability of large random Boolean formulas with K variables per clause (random K-satisfiability) is a fundamental problem in combinatorial discrete optimization. Here we study random K -satisfiability for K = 3, 4 by the Backtracking Survey Propagation (BSP) algorithm, which is able to find, in a time almost linear in the problem size, solutions within a region never reached before: for K = 3 the algorithmic threshold practically coincides with the SAT-UNSAT threshold, while for K=4 it extrapolates beyond the rigidity threshold, where most of the solutions acquire a positive density of frozen variables. All solutions found by BSP have no frozen variables, thus supporting the conjecture that only unfrozen solutions can be found in linear time. The iterative algorithm for determining which variables are frozen in a solution (whitening) reaches the all-variables-unfrozen fixed point following a two step process and has a relaxation time diverging at the algorithmic threshold.
from cs.AI updates on arXiv.org http://ift.tt/1I5Y6A4
via IFTTT
Format Manuscripts/Mixed Material
from Google Alert - anonymous http://ift.tt/242exLK
via IFTTT
[FD] Lock Browser 5.3 (Browser Security Open Source Python)
Source: Gmail -> IFTTT-> Blogger
[FD] [ERPSCAN-16-005] SAP HANA hdbxsengine JSON DoS vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] [ERPSCAN-16-004] SAP NetWeaver 7.4 (Pmitest servlet) XSS vulnerability
Source: Gmail -> IFTTT-> Blogger
Orioles: P Ubaldo Jimenez dominates Blue Jays' Big 3 mashers holding them to a .127 lifetime batting average - Crasnick (ESPN)
via IFTTT
Researcher releases Free Ransomware Detection Tool for Mac OS X Users
from The Hacker News http://ift.tt/1XJ0FSE
via IFTTT
'We no nothing about that letter' says anonymous Oakbay employee
from Google Alert - anonymous http://ift.tt/20XPnfl
via IFTTT
Anonymous Register Link not showing in Login Block
from Google Alert - anonymous http://ift.tt/1SvKDgK
via IFTTT
Virtual Special Issues: Aerospace & Astrobiology Top Cited Articles
The Elsevier’s Aerospace & Astrobiology multidisciplinary team has put together this “virtual” special issue, which consists of the top two most highly cited articles (publication dates 2013-2015) from Elsevier’s Aerospace, Earth & Planetary Sciences collections.
from Icarus http://ift.tt/1SvtHae
via IFTTT
ISS Daily Summary Report 04/19/16
from ISS On-Orbit Status Report http://ift.tt/1VjzKiF
via IFTTT
China wants Apple's Source Code but the Company Refused
from The Hacker News http://ift.tt/1TiOZ7X
via IFTTT
Hypocrisy on anonymous donors
from Google Alert - anonymous http://ift.tt/1MHEcoC
via IFTTT
Tuesday, April 19, 2016
Text-based LSTM networks for Automatic Music Composition. (arXiv:1604.05358v1 [cs.AI])
In this paper, we introduce new methods and discuss results of text-based LSTM (Long Short-Term Memory) networks for automatic music composition. The proposed network is designed to learn relationships within text documents that represent chord progressions and drum tracks in two case studies. In the experiments, word-RNNs (Recurrent Neural Networks) show good results for both cases, while character-based RNNs (char-RNNs) only succeed to learn chord progressions. The proposed system can be used for fully automatic composition or as semi-automatic systems that help humans to compose music by controlling a diversity parameter of the model.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1VCKuIB
via IFTTT
Extending the Harper Identity to Iterated Belief Change. (arXiv:1604.05419v1 [cs.AI])
The field of iterated belief change has focused mainly on revision, with the other main operator of AGM belief change theory, i.e. contraction, receiving relatively little attention. In this paper we extend the Harper Identity from single-step change to define iterated contraction in terms of iterated revision. Specifically, just as the Harper Identity provides a recipe for defining the belief set resulting from contracting A in terms of (i) the initial belief set and (ii) the belief set resulting from revision by not-A, we look at ways to define the plausibility ordering over worlds resulting from contracting A in terms of (iii) the initial plausibility ordering, and (iv) the plausibility ordering resulting from revision by not-A. After noting that the most straightforward such extension leads to a trivialisation of the space of permissible orderings, we provide a family of operators for combining plausibility orderings that avoid such a result. These operators are characterised in our domain of interest by a pair of intuitively compelling properties, which turn out to enable the derivation of a number of iterated contraction postulates from postulates for iterated revision. We finish by observing that a salient member of this family allows for the derivation of counterparts for contraction of some well known iterated revision operators, as well as for defining new iterated contraction operators.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1QlwVW7
via IFTTT
Understanding Rating Behaviour and Predicting Ratings by Identifying Representative Users. (arXiv:1604.05468v1 [cs.IR])
Online user reviews describing various products and services are now abundant on the web. While the information conveyed through review texts and ratings is easily comprehensible, there is a wealth of hidden information in them that is not immediately obvious. In this study, we unlock this hidden value behind user reviews to understand the various dimensions along which users rate products. We learn a set of users that represent each of these dimensions and use their ratings to predict product ratings. Specifically, we work with restaurant reviews to identify users whose ratings are influenced by dimensions like 'Service', 'Atmosphere' etc. in order to predict restaurant ratings and understand the variation in rating behaviour across different cuisines. While previous approaches to obtaining product ratings require either a large number of user ratings or a few review texts, we show that it is possible to predict ratings with few user ratings and no review text. Our experiments show that our approach outperforms other conventional methods by 16-27% in terms of RMSE.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1VCKs3t
via IFTTT
Managing Overstaying Electric Vehicles in Park-and-Charge Facilities. (arXiv:1604.05471v1 [cs.AI])
With the increase in adoption of Electric Vehicles (EVs), proper utilization of the charging infrastructure is an emerging challenge for service providers. Overstaying of an EV after a charging event is a key contributor to low utilization. Since overstaying is easily detectable by monitoring the power drawn from the charger, managing this problem primarily involves designing an appropriate penalty during the overstaying period. Higher penalties do discourage overstaying; however, due to uncertainty in parking duration, less people would find such penalties acceptable, leading to decreased utilization (and revenue). To analyze this central trade-off, we develop a novel framework that integrates models for realistic user behavior into queueing dynamics to locate the optimal penalty from the points of view of utilization and revenue, for different values of the external charging demand. Next, when the model parameters are unknown, we show how an online learning algorithm, such as UCB, can be adapted to learn the optimal penalty. Our experimental validation, based on charging data from London, shows that an appropriate penalty can increase both utilization and revenue while significantly reducing overstaying events.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1QlwX0e
via IFTTT
Demand Prediction and Placement Optimization for Electric Vehicle Charging Stations. (arXiv:1604.05472v1 [cs.AI])
Effective placement of charging stations plays a key role in Electric Vehicle (EV) adoption. In the placement problem, given a set of candidate sites, an optimal subset needs to be selected with respect to the concerns of both (a) the charging station service provider, such as the demand at the candidate sites and the budget for deployment, and (b) the EV user, such as charging station reachability and short waiting times at the station. This work addresses these concerns, making the following three novel contributions: (i) a supervised multi-view learning framework using Canonical Correlation Analysis (CCA) for demand prediction at candidate sites, using multiple datasets such as points of interest information, traffic density, and the historical usage at existing charging stations; (ii) a mixed-packing-and- covering optimization framework that models competing concerns of the service provider and EV users; (iii) an iterative heuristic to solve these problems by alternately invoking knapsack and set cover algorithms. The performance of the demand prediction model and the placement optimization heuristic are evaluated using real world data.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1pfq2zz
via IFTTT
The SP theory of intelligence and the representation and processing of knowledge in the brain. (arXiv:1604.05535v1 [cs.AI])
The "SP theory of intelligence", with its realisation in the "SP computer model", aims to simplify and integrate observations and concepts across AI-related fields, with information compression as a unifying theme. This paper describes how abstract structures and processes in the theory may be realised in terms of neurons, their interconnections, and the transmission of signals between neurons. This part of the SP theory -- "SP-neural" -- is a tentative and partial model for the representation and processing of knowledge in the brain. In the SP theory (apart from SP-neural), all kinds of knowledge are represented with "patterns", where a pattern is an array of atomic symbols in one or two dimensions. In SP-neural, the concept of a "pattern" is realised as an array of neurons called a "pattern assembly", similar to Hebb's concept of a "cell assembly" but with important differences. Central to the processing of information in the SP system is the powerful concept of "multiple alignment", borrowed and adapted from bioinformatics. Processes such as pattern recognition, reasoning and problem solving are achieved via the building of multiple alignments, while unsupervised learning -- significantly different from the "Hebbian" kinds of learning -- is achieved by creating patterns from sensory information and also by creating patterns from multiple alignments in which there is a partial match between one pattern and another. Short-lived neural structures equivalent to multiple alignments will be created via an inter-play of excitatory and inhibitory neural signals. The paper discusses several associated issues, with relevant empirical evidence.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1VCKusm
via IFTTT
AGI and Reflexivity. (arXiv:1604.05557v1 [cs.AI])
We define a property of intelligent systems, which we call Reflexivity. In human beings, it is one aspect of consciousness, and an element of deliberation. We propose a conjecture, that this property is conditioned by a topological property of the processes which implement this reflexivity. These processes may be symbolic, or non symbolic e.g. connexionnist. An architecture which implements reflexivity may be based on the interaction of one or several modules of deep learning, which may be specialized or not, and interconnected in a relevant way. A necessary condition of reflexivity is the existence of recurrence in its processes, we will examine in which cases this condition may be sufficient. We will then examine how this topology and this property make possible the expression of a second property, the deliberation. In a final paragraph, we propose an evaluation of intelligent systems, based on the fulfillment of all or some of these properties.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1QlwVW2
via IFTTT
Contribution to the Formal Specification and Verification of a Multi-Agent Robotic System. (arXiv:1604.05577v1 [cs.SE])
It is important to have multi-agent robotic system specifications that ensure correctness properties of safety and liveness. As these systems have concurrency, and often have dynamic environment, the formal specification and verification of these systems along with step-wise refinement from abstract to concrete concepts play a major role in system correctness. Formal verification is used for exhaustive investigation of the system space thus ensuring that undetected failures in the behavior are excluded. We construct the system incrementally from subcomponents, based on software architecture. The challenge is to develop a safe multi-agent robotic system, more specifically to ensure the correctness properties of safety and liveness. Formal specifications based on model-checking are flexible, have a concrete syntax, and play vital role in correctness of a multi-agent robotic system. To formally verify safety and liveness of such systems is important because they have high concurrency and in most of the cases have dynamic environment. We have considered a case-study of a multi-agent robotic system for the transport of stock between storehouses to exemplify our formal approach. Our proposed development approach allows for formal verification during specification definition. The development process has been classified in to four major phases of requirement specifications, verification specifications, architecture specifications and implementation.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1VCKrN9
via IFTTT
Pattern-Based Approach to the Workflow Satisfiability Problem with User-Independent Constraints. (arXiv:1604.05636v1 [cs.AI])
The fixed parameter tractable (FPT) approach is a powerful tool in tackling computationally hard problems. In this paper we link FPT results to classic artificial intelligence techniques to show how they complement each other. Specifically, we consider the workflow satisfiability problem (WSP) which asks whether there exists an assignment of authorised users to the steps in a workflow specification, subject to certain constraints on the assignment. It was shown that WSP restricted to the class of user-independent constraints (UI), covering many practical cases, admits FPT algorithms.
We show that the FPT nature of WSP with UI constraints decomposes the problem into two levels, and exploit this in a new FPT algorithm that is by many orders of magnitude faster then the previous state-of-the-art WSP algorithm.
The WSP with UI constraints can also be viewed as an extension of the hypergraph list colouring problem. Inspired by a classic graph colouring method called Zykov's Contraction, we designed a new pseudo-boolean (PB) formulation of WSP with UI constraints that also exploits the two-level split of the problem. Our experiments showed that, in many cases, this formulation being solved with a general purpose PB solver demonstrated performance comparable to that of our bespoke FPT algorithm. This raises the potential of using general purpose solvers to tackle FPT problems efficiently.
We also study the practical, average-case, performance of various algorithms. To support this we extend studies of phase transition phenomena in the understanding of the average computational effort needed to solve decision problems. We investigate, for the first time, the phase transition properties of the WSP, under a model for generation of random instances, and note that the methods of the phase transition study need to be adjusted to FPT problems.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1QlwVFL
via IFTTT
Proving the Incompatibility of Efficiency and Strategyproofness via SMT Solving. (arXiv:1604.05692v1 [cs.GT])
Two important requirements when aggregating the preferences of multiple agents are that the outcome should be economically efficient and the aggregation mechanism should not be manipulable. In this paper, we provide a computer-aided proof of a sweeping impossibility using these two conditions for randomized aggregation mechanisms. More precisely, we show that every efficient aggregation mechanism can be manipulated for all expected utility representations of the agents' preferences. This settles a conjecture by Aziz et al. [2013b] and strengthens a number of existing theorems, including statements that were shown within the special domain of assignment. Our proof is obtained by formulating the claim as a satisfiability problem over predicates from real-valued arithmetic, which is then checked using an SMT (satisfiability modulo theories) solver. To the best of our knowledge, this is the first application of SMT solvers in computational social choice.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1SS54hL
via IFTTT
Time-Sensitive Bayesian Information Aggregation for Crowdsourcing Systems. (arXiv:1510.06335v2 [cs.AI] UPDATED)
Crowdsourcing systems commonly face the problem of aggregating multiple judgments provided by potentially unreliable workers. In addition, several aspects of the design of efficient crowdsourcing processes, such as defining worker's bonuses, fair prices and time limits of the tasks, involve knowledge of the likely duration of the task at hand. Bringing this together, in this work we introduce a new time--sensitive Bayesian aggregation method that simultaneously estimates a task's duration and obtains reliable aggregations of crowdsourced judgments. Our method, called BCCTime, builds on the key insight that the time taken by a worker to perform a task is an important indicator of the likely quality of the produced judgment. To capture this, BCCTime uses latent variables to represent the uncertainty about the workers' completion time, the tasks' duration and the workers' accuracy. To relate the quality of a judgment to the time a worker spends on a task, our model assumes that each task is completed within a latent time window within which all workers with a propensity to genuinely attempt the labelling task (i.e., no spammers) are expected to submit their judgments. In contrast, workers with a lower propensity to valid labeling, such as spammers, bots or lazy labelers, are assumed to perform tasks considerably faster or slower than the time required by normal workers. Specifically, we use efficient message-passing Bayesian inference to learn approximate posterior probabilities of (i) the confusion matrix of each worker, (ii) the propensity to valid labeling of each worker, (iii) the unbiased duration of each task and (iv) the true label of each task. Using two real-world public datasets for entity linking tasks, we show that BCCTime produces up to 11% more accurate classifications and up to 100% more informative estimates of a task's duration compared to state-of-the-art methods.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1MU61b9
via IFTTT
Convolutional Models for Joint Object Categorization and Pose Estimation. (arXiv:1511.05175v6 [cs.CV] UPDATED)
In the task of Object Recognition, there exists a dichotomy between the categorization of objects and estimating object pose, where the former necessitates a view-invariant representation, while the latter requires a representation capable of capturing pose information over different categories of objects. With the rise of deep architectures, the prime focus has been on object category recognition. Deep learning methods have achieved wide success in this task. In contrast, object pose regression using these approaches has received relatively much less attention. In this paper we show how deep architectures, specifically Convolutional Neural Networks (CNN), can be adapted to the task of simultaneous categorization and pose estimation of objects. We investigate and analyze the layers of various CNN models and extensively compare between them with the goal of discovering how the layers of distributed representations of CNNs represent object pose information and how this contradicts with object category representations. We extensively experiment on two recent large and challenging multi-view datasets. Our models achieve better than state-of-the-art performance on both datasets.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/1WY53kr
via IFTTT
Orioles: Former P Milt Pappas dies at 76; 110-74 in 9 seasons with team part of trade that brought Frank Robinson there (ESPN)
via IFTTT
Viber adds End-to-End Encryption and PIN protected Hidden Chats features
from The Hacker News http://ift.tt/20V2e1S
via IFTTT
I have a new follower on Twitter
Thorsten Heller
Co-#Founder & Über-#Geek at @greenbirdIT with way too many thoughts on #IoT, #BigData, #AI, #ApacheSpark, #ApacheKafka, #Docker, #Containers, #PaaS & #Startups.
San Francisco, CA | Oslo, NO
https://t.co/i7YzkDZyKX
Following: 7857 - Followers: 8778
April 19, 2016 at 03:21PM via Twitter http://twitter.com/ThoHeller
Ravens: QB Joe Flacco says he has made \"big improvements\" over the last 3 weeks of rehab following December knee surgery (ESPN)
via IFTTT
MIT builds Artificial Intelligence system that can detect 85% of Cyber Attacks
from The Hacker News http://ift.tt/23X8W9e
via IFTTT
error TS1206
from Google Alert - anonymous http://ift.tt/1qWPtYh
via IFTTT
I have a new follower on Twitter
Masaya & Company
Handmade modern wood furniture, sustainably sourced from seedling to finished product. We plant 100 trees for every furniture piece sold.
nicaragua & nashville
https://t.co/kIWv9qAGvy
Following: 3305 - Followers: 2994
April 19, 2016 at 12:44PM via Twitter http://twitter.com/masayacompany
Empirical study of PROXTONE and PROXTONE$$ for Fast Learning of Large Scale Sparse Models. (arXiv:1604.05024v1 [cs.LG])
PROXTONE is a novel and fast method for optimization of large scale non-smooth convex problem \cite{shi2015large}. In this work, we try to use PROXTONE method in solving large scale \emph{non-smooth non-convex} problems, for example training of sparse deep neural network (sparse DNN) or sparse convolutional neural network (sparse CNN) for embedded or mobile device. PROXTONE converges much faster than first order methods, while first order method is easy in deriving and controlling the sparseness of the solutions. Thus in some applications, in order to train sparse models fast, we propose to combine the merits of both methods, that is we use PROXTONE in the first several epochs to reach the neighborhood of an optimal solution, and then use the first order method to explore the possibility of sparsity in the following training. We call such method PROXTONE plus (PROXTONE$^+$). Both PROXTONE and PROXTONE$^+$ are tested in our experiments, and which demonstrate both methods improved convergence speed twice as fast at least on diverse sparse model learning problems, and at the same time reduce the size to 0.5\% for DNN models. The source of all the algorithms is available upon request.
Help us improve arXiv so we can better serve you. Take our user survey.
from cs.AI updates on arXiv.org http://ift.tt/22JgiuA
via IFTTT
ISS Daily Summary Report 04/18/16
from ISS On-Orbit Status Report http://ift.tt/1MFqxhR
via IFTTT
Google makes it mandatory for Chrome Apps to tell Users what Data they collect
from The Hacker News http://ift.tt/1S7SajS
via IFTTT
Crystal Meth Anonymous - Crystal Meth Anonymous
from Google Alert - anonymous http://ift.tt/1SrXIaW
via IFTTT
Anonymous users cannot subscribe to content
from Google Alert - anonymous http://ift.tt/1Si2sdM
via IFTTT
Hackers can spy on your calls and track location using just your phone number
from The Hacker News http://ift.tt/1SrNsQ7
via IFTTT
Monday, April 18, 2016
I have a new follower on Twitter
Jacobo Guerra
Technology Innovator, A.I. Advocate & Entrepeneur #CreativeDirector #SystemDesigner #Startups #TechnologyConsultant #AppDeveloper #MediaProducer #Entrepeneur
Islas Baleares, España
Following: 1548 - Followers: 351
April 18, 2016 at 10:21PM via Twitter http://twitter.com/JacoboGuerra1
Why Artificial Intelligence Needs a Task Theory --- And What It Might Look Like. (arXiv:1604.04660v1 [cs.AI])
The concept of "task" is at the core of artificial intelligence (AI) --- the raison d'\^etre of AI systems. Tasks are used in system evaluation, pedagogy and decision making (through task decomposition and subtask selection). Other fields have strong theories of tasks in their domain that allows them to thoroughly evaluate their designs by methodical manipulation of well understood parameters of known importance; this allows an aeronautics engineer, for instance, to systematically assess the effects of wind speed on an airplane's stability. No framework exists that allows the kind of methodical manipulation found in other disciplines: Results on the few tasks in current use (c.f. board games, question-answering) cannot be easily compared, however similar or different. A task theory would address this by providing the appropriate formalization and classification of tasks, environments, and their parameters, enabling more rigorous ways of measuring, comparing, and evaluating intelligent behavior. Furthermore, analysis and (de)construction of tasks can help teachers devise appropriate challenges for learning systems, and help AI systems make more informed decisions about what (sub)tasks to pursue. Here we discuss the main elements of this argument and propose what such a theory might look like for physical tasks.
from cs.AI updates on arXiv.org http://ift.tt/1Vf09ht
via IFTTT