Latest YouTube Video
Saturday, February 13, 2016
alcoholics anonymous coin
from Google Alert - anonymous http://ift.tt/1TiD6B1
via IFTTT
33 minutes ago
from Google Alert - anonymous http://ift.tt/1R1JitO
via IFTTT
Russia Wants to Kick Foreign Tech Companies Out Of The Nation
from The Hacker News http://ift.tt/1PtPdrg
via IFTTT
I have a new follower on Twitter
FinTech
Let's disrupt them.
Following: 1602 - Followers: 2251
February 13, 2016 at 07:12AM via Twitter http://twitter.com/Fin__Tech
Here's How to Decrypt Hydracrypt & Umbrecrypt Ransomware Files
from The Hacker News http://ift.tt/1R13b4l
via IFTTT
Nasdaq to Use Bitcoin-style Blockchain to Record Shareholder Votes
from The Hacker News http://ift.tt/1KMwoR3
via IFTTT
British Intelligence is Legally Allowed to Hack Anyone, Court Says
from The Hacker News http://ift.tt/1Xpe9TR
via IFTTT
Friday Playlist: Anonymous
from Google Alert - anonymous http://ift.tt/20RhH6M
via IFTTT
Friday, February 12, 2016
[FD] [ERPSCAN-15-032] SAP PCo agent – DoS vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] [ERPSCAN-15-031] SAP MII – Encryption Downgrade vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] BSides Hannover 2016
Source: Gmail -> IFTTT-> Blogger
[FD] RVAsec 2016 CFP is now Open!
Source: Gmail -> IFTTT-> Blogger
[FD] Serena Business Manager < 10.01 DOM XSS Vulnerability
1337 >>
Source: Gmail -> IFTTT-> Blogger
[FD] KL-001-2016-001 : Arris DG1670A Cable Modem Remote Command Execution
Source: Gmail -> IFTTT-> Blogger
Police Arrest 16-year-old Boy Who Hacked CIA Director
from The Hacker News http://ift.tt/1Qc1tKc
via IFTTT
Anonymous user cannot create isbn2node
from Google Alert - anonymous http://ift.tt/1RwFFyr
via IFTTT
I have a new follower on Twitter
Get Free Followers
Get up to 10,000 new followers! Try our website today @ https://t.co/iaEBJ0THOO!
United States
Following: 1520 - Followers: 247
February 12, 2016 at 12:40PM via Twitter http://twitter.com/MarthaHolt__
ISS Daily Summary Report – 02/11/16
from ISS On-Orbit Status Report http://ift.tt/20PVki5
via IFTTT
New York Police Used Cell Phone Spying Tool Over 1000 Times Without Warrant
from The Hacker News http://ift.tt/1KK3RvB
via IFTTT
Microsoft Edge's InPrivate Mode Finally Keeps Your Activity Private
from The Hacker News http://ift.tt/1QZvIHq
via IFTTT
[FD] HD Video Player v2.5 iOS - Multiple Web Vulnerabilities
Source: Gmail -> IFTTT-> Blogger
Hey, Apple User! Check If You are also Affected by the Sparkle Vulnerability
from The Hacker News http://ift.tt/1KfhbIv
via IFTTT
LIGO Detects Gravitational Waves from Merging Black Holes
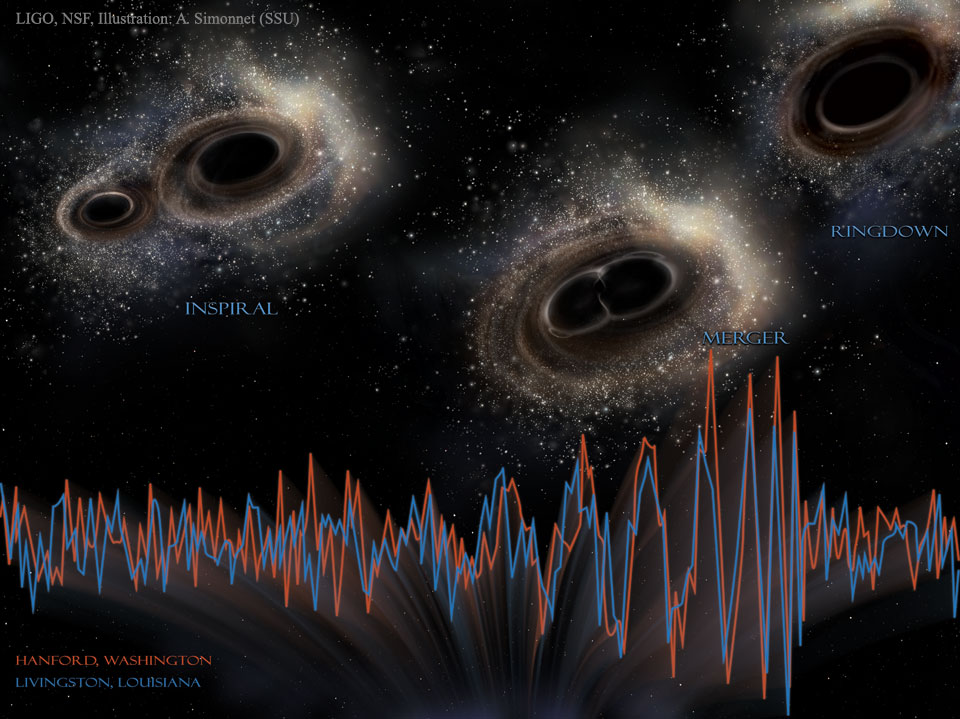
Thursday, February 11, 2016
Network of Bandits. (arXiv:1602.03779v1 [cs.AI])
The distribution of the best arm identification task on the user's devices offers several advantages for application purposes: scalability, reduction of deployment costs and privacy. We propose a distributed version of the algorithm Successive Elimination using a simple architecture based on a single server which synchronizes each task executed on the user's devices. We show that this algorithm is optimal in terms of transmitted number of bits and is optimal up to logarithmic factors in terms to number of pulls per player. Finally, we propose an extension of this approach to distribute the contextual bandit algorithm Bandit Forest, which is able to finely exploit the user's data while guaranteeing the privacy.
from cs.AI updates on arXiv.org http://ift.tt/1XmBDce
via IFTTT
Enabling Basic Normative HRI in a Cognitive Robotic Architecture. (arXiv:1602.03814v1 [cs.RO])
Collaborative human activities are grounded in social and moral norms, which humans consciously and subconsciously use to guide and constrain their decision-making and behavior, thereby strengthening their interactions and preventing emotional and physical harm. This type of norm-based processing is also critical for robots in many human-robot interaction scenarios (e.g., when helping elderly and disabled persons in assisted living facilities, or assisting humans in assembly tasks in factories or even the space station). In this position paper, we will briefly describe how several components in an integrated cognitive architecture can be used to implement processes that are required for normative human-robot interactions, especially in collaborative tasks where actions and situations could potentially be perceived as threatening and thus need a change in course of action to mitigate the perceived threats.
from cs.AI updates on arXiv.org http://ift.tt/1QvbcM4
via IFTTT
Lift-Based Bidding in Ad Selection. (arXiv:1507.04811v2 [cs.GT] UPDATED)
Real-time bidding (RTB) has become one of the largest online advertising markets in the world. Today the bid price per ad impression is typically decided by the expected value of how it can lead to a desired action event (e.g., registering an account or placing a purchase order) to the advertiser. However, this industry standard approach to decide the bid price does not consider the actual effect of the ad shown to the user, which should be measured based on the performance lift among users who have been or have not been exposed to a certain treatment of ads. In this paper, we propose a new bidding strategy and prove that if the bid price is decided based on the performance lift rather than absolute performance value, advertisers can actually gain more action events. We describe the modeling methodology to predict the performance lift and demonstrate the actual performance gain through blind A/B test with real ad campaigns in an industry-leading Demand-Side Platform (DSP). We also discuss the relationship between attribution models and bidding strategies. We prove that, to move the DSPs to bid based on performance lift, they should be rewarded according to the relative performance lift they contribute.
from cs.AI updates on arXiv.org http://ift.tt/1Oq2mjN
via IFTTT
Alternative Markov and Causal Properties for Acyclic Directed Mixed Graphs. (arXiv:1511.05835v3 [stat.ML] UPDATED)
We extend AMP chain graphs by (i) relaxing the semidirected acyclity constraint so that only directed cycles are forbidden, and (ii) allowing up to two edges between any pair of nodes. We introduce global, ordered local and pairwise Markov properties for the new models. We show the equivalence of these properties for strictly positive probability distributions. We also show that when the random variables are continuous, the new models can be interpreted as systems of structural equations with correlated errors. This enables us to adapt Pearl's do-calculus to them. Finally, we describe an exact algorithm for learning the new models from observational and interventional data via answer set programming.
from cs.AI updates on arXiv.org http://ift.tt/1OfZpCV
via IFTTT
Column-Oriented Datalog Materialization for Large Knowledge Graphs (Extended Technical Report). (arXiv:1511.08915v2 [cs.DB] UPDATED)
The evaluation of Datalog rules over large Knowledge Graphs (KGs) is essential for many applications. In this paper, we present a new method of materializing Datalog inferences, which combines a column-based memory layout with novel optimization methods that avoid redundant inferences at runtime. The pro-active caching of certain subqueries further increases efficiency. Our empirical evaluation shows that this approach can often match or even surpass the performance of state-of-the-art systems, especially under restricted resources.
from cs.AI updates on arXiv.org http://ift.tt/1SsW2K1
via IFTTT
Activist Hacker Group, Anonymous, Launches Flint Operation
from Google Alert - anonymous http://ift.tt/1Xmuusl
via IFTTT
Conservatives Anonymous
from Google Alert - anonymous http://ift.tt/20rvjQL
via IFTTT
Ravens: LT Eugene Monroe has missed 16 games in the last two seasons, could use change of scenery - Jamison Hensley (ESPN)
via IFTTT
IMMEDIATE need for Anonymous Donors!
from Google Alert - anonymous http://ift.tt/1KecfDK
via IFTTT
Ocean City, MD's surf is at least 5.86ft high
Ocean City, MD Summary
At 2:00 AM, surf min of 1.51ft. At 8:00 AM, surf min of 4.52ft. At 2:00 PM, surf min of 5.86ft. At 8:00 PM, surf min of 3.0ft.
Surf maximum: 7.01ft (2.14m)
Surf minimum: 5.86ft (1.79m)
Tide height: 2.71ft (0.83m)
Wind direction: WNW
Wind speed: 20.95 KTS
from Surfline http://ift.tt/1kVmigH
via IFTTT
anonymous-doser
from Google Alert - anonymous http://ift.tt/1KdZIQv
via IFTTT
Integration of a Multiple Anonymous Function Which Depends on Parameters of an Integral
from Google Alert - anonymous http://ift.tt/1LjqrWJ
via IFTTT
ENCRYPT Act of 2016 — Proposed Bill Restricts States to Ban Encryption
from The Hacker News http://ift.tt/1O4BkM7
via IFTTT
ISS Daily Summary Report – 02/10/16
from ISS On-Orbit Status Report http://ift.tt/1KHuHV1
via IFTTT
Deep Web Search Engines to Explore the Hidden Internet
from The Hacker News http://ift.tt/1KdboTF
via IFTTT
I have a new follower on Twitter
Hazelcast
The Leading In-Memory Data Grid
Palo Alto, CA
http://t.co/Lpn6F676KF
Following: 314 - Followers: 3840
February 11, 2016 at 04:12AM via Twitter http://twitter.com/hazelcast
Galaxies in the River

Wednesday, February 10, 2016
I have a new follower on Twitter
RenewableEnergySols
Leading Renewable Energy strategy consulting company. Focus: M&A, growth, and industry consolidation. Speciality: Wind. Background: Shipping, logistics, and SCM
Copenhagen, Denmark
http://t.co/O5VQQ0Nqua
Following: 6959 - Followers: 7827
February 10, 2016 at 10:14PM via Twitter http://twitter.com/RenewablNrgySls
Time Resource Networks. (arXiv:1602.03203v1 [cs.AI])
The problem of scheduling under resource constraints is widely applicable. One prominent example is power management, in which we have a limited continuous supply of power but must schedule a number of power-consuming tasks. Such problems feature tightly coupled continuous resource constraints and continuous temporal constraints.
We address such problems by introducing the Time Resource Network (TRN), an encoding for resource-constrained scheduling problems. The definition allows temporal specifications using a general family of representations derived from the Simple Temporal network, including the Simple Temporal Network with Uncertainty, and the probabilistic Simple Temporal Network (Fang et al. (2014)).
We propose two algorithms for determining the consistency of a TRN: one based on Mixed Integer Programing and the other one based on Constraint Programming, which we evaluate on scheduling problems with Simple Temporal Constraints and Probabilistic Temporal Constraints.
from cs.AI updates on arXiv.org http://ift.tt/1LidaxU
via IFTTT
Feature Based Task Recommendation in Crowdsourcing with Implicit Observations. (arXiv:1602.03291v1 [cs.AI])
Existing research in crowdsourcing has investigated how to recommend tasks to workers based on which task the workers have already completed, referred to as {\em implicit feedback}. We, on the other hand, investigate the task recommendation problem, where we leverage both implicit feedback and explicit features of the task. We assume that we are given a set of workers, a set of tasks, interactions (such as the number of times a worker has completed a particular task), and the presence of explicit features of each task (such as, task location). We intend to recommend tasks to the workers by exploiting the implicit interactions, and the presence or absence of explicit features in the tasks. We formalize the problem as an optimization problem, propose two alternative problem formulations and respective solutions that exploit implicit feedback, explicit features, as well as similarity between the tasks. We compare the efficacy of our proposed solutions against multiple state-of-the-art techniques using two large scale real world datasets.
from cs.AI updates on arXiv.org http://ift.tt/1KcDjDf
via IFTTT
Iterative Hierarchical Optimization for Misspecified Problems (IHOMP). (arXiv:1602.03348v1 [cs.LG])
Reinforcement Learning (RL) aims to learn an optimal policy for a Markov Decision Process (MDP). For complex, high-dimensional MDPs, it may only be feasible to represent the policy with function approximation. If the policy representation used cannot represent good policies, the problem is misspecified and the learned policy may be far from optimal. We introduce IHOMP as an approach for solving misspecified problems. IHOMP iteratively refines a set of specialized policies based on a limited representation. We refer to these policies as policy threads. At the same time, IHOMP stitches these policy threads together in a hierarchical fashion to solve a problem that was otherwise misspecified. We prove that IHOMP enjoys theoretical convergence guarantees and extend IHOMP to exploit Option Interruption (OI) enabling it to learn where policy threads can be reused. Our experiments demonstrate that IHOMP can find near-optimal solutions to otherwise misspecified problems and that OI can further improve the solutions.
from cs.AI updates on arXiv.org http://ift.tt/1KcDiiK
via IFTTT
Adaptive Skills, Adaptive Partitions (ASAP). (arXiv:1602.03351v1 [cs.LG])
We introduce the Adaptive Skills, Adaptive Partitions (ASAP) algorithm that (1) learns skills (i.e., temporally extended actions or options) as well as (2) where to apply them to solve a Markov decision process. ASAP is initially provided with a misspecified hierarchical model and is able to correct this model and learn a near-optimal set of skills to solve a given task. We believe that (1) and (2) are the core components necessary for a truly general skill learning framework, which is a key building block needed to scale up to lifelong learning agents. ASAP is also able to solve related new tasks simply by adapting where it applies its existing learned skills. We prove that ASAP converges to a local optimum under natural conditions. Finally, our extensive experimental results, which include a RoboCup domain, demonstrate the ability of ASAP to learn where to reuse skills as well as solve multiple tasks with considerably less experience than solving each task from scratch.
from cs.AI updates on arXiv.org http://ift.tt/1KcDjDb
via IFTTT
Learning Distributed Representations of Sentences from Unlabelled Data. (arXiv:1602.03483v1 [cs.CL])
Unsupervised methods for learning distributed representations of words are ubiquitous in today's NLP research, but far less is known about the best ways to learn distributed phrase or sentence representations from unlabelled data. This paper is a systematic comparison of models that learn such representations. We find that the optimal approach depends critically on the intended application. Deeper, more complex models are preferable for representations to be used in supervised systems, but shallow log-linear models work best for building representation spaces that can be decoded with simple spatial distance metrics. We also propose two new unsupervised representation-learning objectives designed to optimise the trade-off between training time, domain portability and performance.
from cs.AI updates on arXiv.org http://ift.tt/1KcDjD8
via IFTTT
Research Priorities for Robust and Beneficial Artificial Intelligence. (arXiv:1602.03506v1 [cs.AI])
Success in the quest for artificial intelligence has the potential to bring unprecedented benefits to humanity, and it is therefore worthwhile to investigate how to maximize these benefits while avoiding potential pitfalls. This article gives numerous examples (which should by no means be construed as an exhaustive list) of such worthwhile research aimed at ensuring that AI remains robust and beneficial.
from cs.AI updates on arXiv.org http://ift.tt/1Lid8WF
via IFTTT
Improved and Generalized Upper Bounds on the Complexity of Policy Iteration. (arXiv:1306.0386v4 [math.OC] UPDATED)
Given a Markov Decision Process (MDP) with $n$ states and a totalnumber $m$ of actions, we study the number of iterations needed byPolicy Iteration (PI) algorithms to converge to the optimal$\gamma$-discounted policy. We consider two variations of PI: Howard'sPI that changes the actions in all states with a positive advantage,and Simplex-PI that only changes the action in the state with maximaladvantage. We show that Howard's PI terminates after at most $O\left(\frac{m}{1-\gamma}\log\left(\frac{1}{1-\gamma}\right)\right)$iterations, improving by a factor $O(\log n)$ a result by Hansen etal., while Simplex-PI terminates after at most $O\left(\frac{nm}{1-\gamma}\log\left(\frac{1}{1-\gamma}\right)\right)$iterations, improving by a factor $O(\log n)$ a result by Ye. Undersome structural properties of the MDP, we then consider bounds thatare independent of the discount factor~$\gamma$: quantities ofinterest are bounds $\tau\_t$ and $\tau\_r$---uniform on all states andpolicies---respectively on the \emph{expected time spent in transientstates} and \emph{the inverse of the frequency of visits in recurrentstates} given that the process starts from the uniform distribution.Indeed, we show that Simplex-PI terminates after at most $\tilde O\left(n^3 m^2 \tau\_t \tau\_r \right)$ iterations. This extends arecent result for deterministic MDPs by Post & Ye, in which $\tau\_t\le 1$ and $\tau\_r \le n$, in particular it shows that Simplex-PI isstrongly polynomial for a much larger class of MDPs. We explain whysimilar results seem hard to derive for Howard's PI. Finally, underthe additional (restrictive) assumption that the state space ispartitioned in two sets, respectively states that are transient andrecurrent for all policies, we show that both Howard's PI andSimplex-PI terminate after at most $\tilde O(m(n^2\tau\_t+n\tau\_r))$iterations.
from cs.AI updates on arXiv.org http://ift.tt/15Aq7j5
via IFTTT
Beyond Temporal Pooling: Recurrence and Temporal Convolutions for Gesture Recognition in Video. (arXiv:1506.01911v3 [cs.CV] UPDATED)
Recent studies have demonstrated the power of recurrent neural networks for machine translation, image captioning and speech recognition. For the task of capturing temporal structure in video, however, there still remain numerous open research questions. Current research suggests using a simple temporal feature pooling strategy to take into account the temporal aspect of video. We demonstrate that this method is not sufficient for gesture recognition, where temporal information is more discriminative compared to general video classification tasks. We explore deep architectures for gesture recognition in video and propose a new end-to-end trainable neural network architecture incorporating temporal convolutions and bidirectional recurrence. Our main contributions are twofold; first, we show that recurrence is crucial for this task; second, we show that adding temporal convolutions leads to significant improvements. We evaluate the different approaches on the Montalbano gesture recognition dataset, where we achieve state-of-the-art results.
from cs.AI updates on arXiv.org http://ift.tt/1QDgN3j
via IFTTT
Beauty and Brains: Detecting Anomalous Pattern Co-Occurrences. (arXiv:1512.07048v2 [cs.AI] UPDATED)
Our world is filled with both beautiful and brainy people, but how often does a Nobel Prize winner also wins a beauty pageant? Let us assume that someone who is both very beautiful and very smart is more rare than what we would expect from the combination of the number of beautiful and brainy people. Of course there will still always be some individuals that defy this stereotype; these beautiful brainy people are exactly the class of anomaly we focus on in this paper. They do not posses intrinsically rare qualities, it is the unexpected combination of factors that makes them stand out.
In this paper we define the above described class of anomaly and propose a method to quickly identify them in transaction data. Further, as we take a pattern set based approach, our method readily explains why a transaction is anomalous. The effectiveness of our method is thoroughly verified with a wide range of experiments on both real world and synthetic data.
from cs.AI updates on arXiv.org http://ift.tt/1mz8bms
via IFTTT
Keeping it Short and Simple: Summarising Complex Event Sequences with Multivariate Patterns. (arXiv:1512.07056v2 [cs.AI] UPDATED)
We study how to obtain concise descriptions of discrete multivariate sequential data. In particular, how to do so in terms of rich multivariate sequential patterns that can capture potentially highly interesting (cor)relations between sequences. To this end we allow our pattern language to span over the domains (alphabets) of all sequences, allow patterns to overlap temporally, as well as allow for gaps in their occurrences.
We formalise our goal by the Minimum Description Length principle, by which our objective is to discover the set of patterns that provides the most succinct description of the data. To discover high-quality pattern sets directly from data, we introduce DITTO, a highly efficient algorithm that approximates the ideal result very well.
Experiments show that DITTO correctly discovers the patterns planted in synthetic data. Moreover, it scales favourably with the length of the data, the number of attributes, the alphabet sizes. On real data, ranging from sensor networks to annotated text, DITTO discovers easily interpretable summaries that provide clear insight in both the univariate and multivariate structure.
from cs.AI updates on arXiv.org http://ift.tt/1TgfF8q
via IFTTT
I have a new follower on Twitter
Fastvue
Internet Activity Reports that make sense of the modern web. For Sophos, Barracuda, Forefront TMG and more.
San Francisco, CA
http://t.co/82WkT8WSi3
Following: 1307 - Followers: 479
February 10, 2016 at 07:34PM via Twitter http://twitter.com/fastvue
MLB Buzz: Orioles deep in negotiations with SP Yovani Gallardo on deal for 3 years in range of $40M to $45M - reports (ESPN)
via IFTTT
I have a new follower on Twitter
David Brown
All things Oracle, web, database, application development, beekeeper. Now starting up PITSS UK - An engineered approach to modernising Oracle Forms
Twickenham
https://t.co/ODfI9yt4FJ
Following: 690 - Followers: 772
February 10, 2016 at 05:59PM via Twitter http://twitter.com/dbrownukk
Ung doulx baiser m'est bien permis de prendre (Anonymous)
from Google Alert - anonymous http://ift.tt/1SJ3KDq
via IFTTT
[FD] Multiple vulnerabilities in Open Real Estate v 1.15.1
Source: Gmail -> IFTTT-> Blogger
[FD] D-Link router DSL-2750B firmware 1.01 to 1.03 - remote command execution no auth required
Source: Gmail -> IFTTT-> Blogger
Re: [FD] OLE DB Provider for Oracle multiple DLL side loading vulnerabilities
Source: Gmail -> IFTTT-> Blogger
[FD] MapsUpdateTask Task DLL side loading vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] BDA MPEG2 Transport Information Filter DLL side loading vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] NPS Datastore server DLL side loading vulnerability
Source: Gmail -> IFTTT-> Blogger
I have a new follower on Twitter
Launch Crowdfunding
Crowdfunding Agency. Helping clients architect and execute strategic equity and rewards-based crowdfunding campaigns. #crowdfunding #equitycrowdfunding
Los Angeles
https://t.co/m7mTTGQugR
Following: 1594 - Followers: 1034
February 10, 2016 at 12:43PM via Twitter http://twitter.com/LaunchCrowdfund
Orioles Buzz: Pursuit of free-agent SP Yovani Gallardo \"making progress\" - multiple reports; 13-11 in 2015 with Rangers (ESPN)
via IFTTT
ISS Daily Summary Report – 02/9/16
from ISS On-Orbit Status Report http://ift.tt/1SfYFCg
via IFTTT
Bye bye, Flash! Google to Ban Flash-based Advertising
from The Hacker News http://ift.tt/1PkQmkO
via IFTTT
Windows 10 Sends Your Data 5500 Times Every Day Even After Tweaking Privacy Settings
from The Hacker News http://ift.tt/1RpcIEq
via IFTTT
On the 8th anniversary of the Anonymous protests, more signs of Scientology's desperation
from Google Alert - anonymous http://ift.tt/20omEhX
via IFTTT
[FD] Apache Sling Framework v2.3.6 (Adobe AEM) [CVE-2016-0956] - Information Disclosure Vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] Getdpd Bug Bounty #6 - (Import - FTP) Persistent Vulnerability
Source: Gmail -> IFTTT-> Blogger
Vigilante Hackers Aim to Hijack 200,000 Routers to Make Them More Secure
from The Hacker News http://ift.tt/1XhYYfc
via IFTTT
Hackers Are Offering Apple Employees $23,000 for Corporate Login Details
from The Hacker News http://ift.tt/20oc22q
via IFTTT
[FD] SEC Consult SA-20160210-0 :: Yeager CMS Multiple Vulnerabilities
Source: Gmail -> IFTTT-> Blogger
All Versions of Windows affected by Critical Security Vulnerability
from The Hacker News http://ift.tt/20UPEjn
via IFTTT
Anonymous hero casually trips suspect running from cops
from Google Alert - anonymous http://ift.tt/20UF9MZ
via IFTTT
Tuesday, February 9, 2016
The IMP game: Learnability, approximability and adversarial learning beyond $\Sigma^0_1$. (arXiv:1602.02743v1 [cs.LO])
We introduce a problem set-up we call the Iterated Matching Pennies (IMP) game and show that it is a powerful framework for the study of three problems: adversarial learnability, conventional (i.e., non-adversarial) learnability and approximability. Using it, we are able to derive the following theorems. (1) It is possible to learn by example all of $\Sigma^0_1 \cup \Pi^0_1$ as well as some supersets; (2) in adversarial learning (which we describe as a pursuit-evasion game), the pursuer has a winning strategy (in other words, $\Sigma^0_1$ can be learned adversarially, but $\Pi^0_1$ not); (3) some languages in $\Pi^0_1$ cannot be approximated by any language in $\Sigma^0_1$.
We show corresponding results also for $\Sigma^0_i$ and $\Pi^0_i$ for arbitrary $i$.
from cs.AI updates on arXiv.org http://ift.tt/20JPpLz
via IFTTT
Value Iteration Networks. (arXiv:1602.02867v1 [cs.AI])
We introduce the value iteration network: a fully differentiable neural network with a `planning module' embedded within. Value iteration networks are suitable for making predictions about outcomes that involve planning-based reasoning, such as predicting a desired trajectory from an observation of a map. Key to our approach is a novel differentiable approximation of the value-iteration algorithm, which can be represented as a convolutional neural network, and trained end-to-end using standard backpropagation. We evaluate our value iteration networks on the task of predicting optimal obstacle-avoiding trajectories from an image of a landscape, both on synthetic data, and on challenging raw images of the Mars terrain.
from cs.AI updates on arXiv.org http://ift.tt/1XhcmQD
via IFTTT
Approximate Probabilistic Inference via Word-Level Counting. (arXiv:1511.07663v3 [cs.AI] UPDATED)
Hashing-based model counting has emerged as a promising approach for large-scale probabilistic inference on graphical models. A key component of these techniques is the use of xor-based 2-universal hash functions that operate over Boolean domains. Many counting problems arising in probabilistic inference are, however, naturally encoded over finite discrete domains. Techniques based on bit-level (or Boolean) hash functions require these problems to be propositionalized, making it impossible to leverage the remarkable progress made in SMT (Satisfiability Modulo Theory) solvers that can reason directly over words (or bit-vectors). In this work, we present the first approximate model counter that uses word-level hashing functions, and can directly leverage the power of sophisticated SMT solvers. Empirical evaluation over an extensive suite of benchmarks demonstrates the promise of the approach.
from cs.AI updates on arXiv.org http://ift.tt/1If6AGI
via IFTTT
Anonymous email calls for transparency
from Google Alert - anonymous http://ift.tt/1KE1eLC
via IFTTT
Anonymous hero casually trips suspect running from cops
from Google Alert - anonymous http://ift.tt/1PATqas
via IFTTT
I have a new follower on Twitter
Owl Eyes
Owl Eyes is an improved reading experience for students, teachers, and everyday readers. Create your free account and start reading today!
http://t.co/2hwDBPkVZQ
Following: 1807 - Followers: 278
February 09, 2016 at 03:59PM via Twitter http://twitter.com/OwlEyesReader
France Orders Facebook To Stop Tracking Non-Users or Face Fines
from The Hacker News http://ift.tt/1Lesr2x
via IFTTT
Orioles: Patrick Palmeiro, 26, signs minor league contract; son of Rafael Palmeiro, who hit 223 of his 569 HR with BAL (ESPN)
via IFTTT
Donate: Members
from Google Alert - anonymous http://ift.tt/20m08WS
via IFTTT
Here's the Facebook Hacking Tool that Can Really Hack Accounts, But...
from The Hacker News http://ift.tt/20lVt7w
via IFTTT
How to Crack GCHQ Crypto Puzzle? — Here's the Solution
from The Hacker News http://ift.tt/1Rlq2cZ
via IFTTT
ISS Daily Summary Report – 02/8/16
from ISS On-Orbit Status Report http://ift.tt/1T2ZoFF
via IFTTT
