Latest YouTube Video
Saturday, December 12, 2015
Anonymous says it took down Trump Tower website
from Google Alert - anonymous http://ift.tt/1NW6CoA
via IFTTT
My Lady Careys Dompe (Anonymous)
from Google Alert - anonymous http://ift.tt/1QbN7iy
via IFTTT
48 comments
from Google Alert - anonymous http://ift.tt/1OYQ1pk
via IFTTT
Ravens: LT Eugene Monroe placed on IR, ending his season; started 6 games this season, signed 5-year deal in March 2014 (ESPN)
via IFTTT
I have a new follower on Twitter
Ravens Report
Voted #1 Sports News App! Get It (http://t.co/QuvnqIDOBZ) and see why it's the easiest way to keep up with the Ravens. @Fanly
Baltimore, MD
http://t.co/QuvnqIDOBZ
Following: 3606 - Followers: 2928
December 12, 2015 at 10:50AM via Twitter http://twitter.com/ravens_fanly
[FD] Windows Authentication UI DLL side loading vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] Event Viewer Snapin multiple DLL side loading vulnerabilities
Source: Gmail -> IFTTT-> Blogger
[FD] COM+ Services DLL side loading vulnerability
Source: Gmail -> IFTTT-> Blogger
Anonymous Declares War On Donald Trump — #OpTrump
from The Hacker News http://ift.tt/1NhlWPA
via IFTTT
The Brightest Spot on Ceres
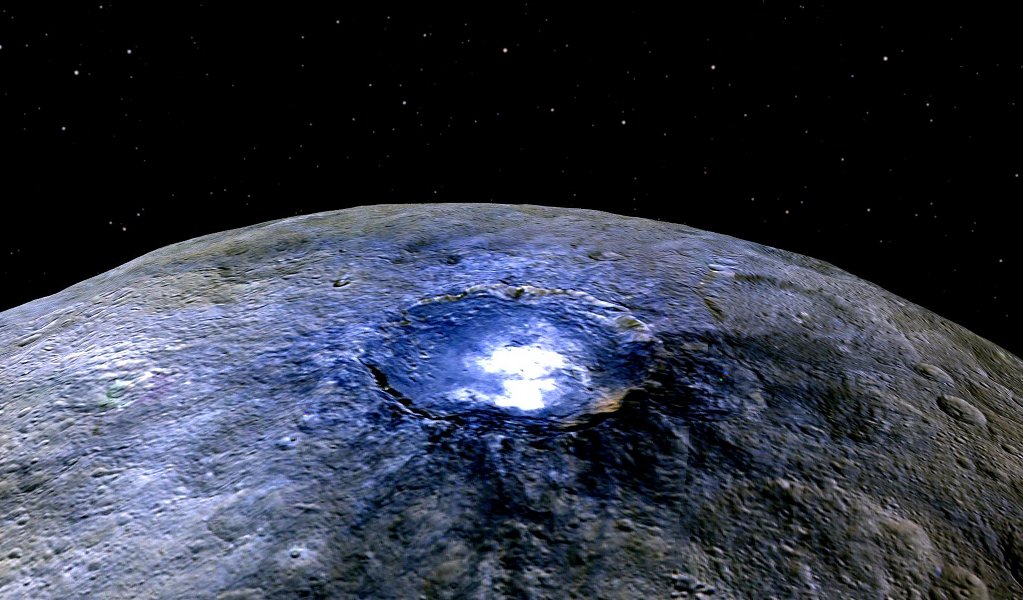
Space Weather to the Edge of the Solar System
from NASA's Scientific Visualization Studio: Most Popular
via IFTTT
Moon Phase and Libration, 2016
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/1QitViS
via IFTTT
Moon Phase and Libration, 2016 South Up
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/1jUk849
via IFTTT
Friday, December 11, 2015
Sex and Love Addicts Anonymous
from Google Alert - anonymous http://ift.tt/1OY0srq
via IFTTT
[FD] APPLE-SA-2015-12-11-1 iTunes 12.3.2
Source: Gmail -> IFTTT-> Blogger
[FD] Polycom VVX-Series Business Media Phones Path Traversal Vulnerability
Source: Gmail -> IFTTT-> Blogger
Trump Tower website taken down by…
from Google Alert - anonymous http://ift.tt/1RJ0SEK
via IFTTT
Ravens: QB Matt Schaub (chest) misses third day of practice; Jimmy Clausen expected to start Sunday vs. Seahawks (ESPN)
via IFTTT
Webform title displays for Anonymous, but not webform's fields
from Google Alert - anonymous http://ift.tt/1Qjiszz
via IFTTT
Orioles: Resolving Chris Davis situation still at top of GM Dan Duquette's \"hefty to-do list\" for the offseason - Matz (ESPN)
via IFTTT
Recent Comments Widgets shows names as "Anonymous"
from Google Alert - anonymous http://ift.tt/1UdyNEK
via IFTTT
ISS Daily Summary Report – 12/10/15
from ISS On-Orbit Status Report http://ift.tt/1UcNojS
via IFTTT
Hacker-Friendly Search Engine that Lists Every Internet-Connected Device
from The Hacker News http://ift.tt/1NRQ1Cf
via IFTTT
Government Could Hack Children's Toys to Spy on You
from The Hacker News http://ift.tt/1QA2AY3
via IFTTT
France will not Ban Public Wi-Fi Or Tor Network, Prime Minister Valls Confirms
from The Hacker News http://ift.tt/1QzSEOg
via IFTTT
Daytime Moon Meets Morning Star

Thursday, December 10, 2015
Convolutional Monte Carlo Rollouts in Go. (arXiv:1512.03375v1 [cs.LG])
In this work, we present a MCTS-based Go-playing program which uses convolutional networks in all parts. Our method performs MCTS in batches, explores the Monte Carlo search tree using Thompson sampling and a convolutional network, and evaluates convnet-based rollouts on the GPU. We achieve strong win rates against open source Go programs and attain competitive results against state of the art convolutional net-based Go-playing programs.
from cs.AI updates on arXiv.org http://ift.tt/1RHylzi
via IFTTT
Exploration and Exploitation of Victorian Science in Darwin's Reading Notebooks. (arXiv:1509.07175v2 [cs.CL] UPDATED)
Search in an environment with an uncertain distribution of resources involves a trade-off between local exploitation and distant exploration. This extends to the problem of information foraging, where a knowledge-seeker shifts between reading in depth and studying new domains. To study this, we examine the reading choices made by one of the most celebrated scientists of the modern era: Charles Darwin. Darwin built his theory of natural selection in part by synthesizing disparate parts of Victorian science. When we analyze his extensively self-documented reading, we find he does not follow a pattern of surprise-minimization. Rather, he shifts between phases in which he either remains with familiar topics or seeks cognitive surprise in novel fields. On the longest timescales, these shifts correlate with major intellectual epochs of his career, as detected by Bayesian epoch estimation. When we compare Darwin's reading path with publication order of the same texts, we find Darwin more adventurous than the culture as a whole. These results provide novel quantitative evidence for historical hypotheses previously debated only qualitatively.
from cs.AI updates on arXiv.org http://ift.tt/1FxghEk
via IFTTT
Learning Linguistic Biomarkers for Predicting Mild Cognitive Impairment using Compound Skip-grams. (arXiv:1511.02436v2 [cs.CL] UPDATED)
Predicting Mild Cognitive Impairment (MCI) is currently a challenge as existing diagnostic criteria rely on neuropsychological examinations. Automated Machine Learning (ML) models that are trained on verbal utterances of MCI patients can aid diagnosis. Using a combination of skip-gram features, our model learned several linguistic biomarkers to distinguish between 19 patients with MCI and 19 healthy control individuals from the DementiaBank language transcript clinical dataset. Results show that a model with compound of skip-grams has better AUC and could help ML prediction on small MCI data sample.
from cs.AI updates on arXiv.org http://ift.tt/1Hsj82r
via IFTTT
Deep Reinforcement Learning in Parameterized Action Space. (arXiv:1511.04143v2 [cs.AI] UPDATED)
Recent work has shown that deep neural networks are capable of approximating both value functions and policies in reinforcement learning domains featuring continuous state and action spaces. However, to the best of our knowledge no previous work has succeeded at using deep neural networks in structured (parameterized) continuous action spaces. To fill this gap, this paper focuses on learning within the domain of simulated RoboCup soccer, which features a small set of discrete action types, each of which is parameterized with continuous variables. The best learned agent can score goals more reliably than the 2012 RoboCup champion agent. As such, this paper represents a successful extension of deep reinforcement learning to the class of parameterized action space MDPs.
from cs.AI updates on arXiv.org http://ift.tt/1PJCj9f
via IFTTT
Anonymous woman pays off strangers' $20K Toys R Us layaways
from Google Alert - anonymous http://ift.tt/1jRLwzY
via IFTTT
[FD] BFS-SA-2015-003: Internet Explorer CObjectElement Use-After-Free Vulnerability
Source: Gmail -> IFTTT-> Blogger
Orioles Buzz: Baltimore reportedly inquired about Rockies OF Carlos Gonzalez; don't want to part with SP Kevin Gausman (ESPN)
via IFTTT
I have a new follower on Twitter
B.J. Rains
Boise State football and basketball beat writer, Idaho Press-Tribune. AP Top 25 hoops voter. Contributor to ESPN Boise, KBOI TV. Email: bjrains@idahopress.com.
Boise, Idaho
http://t.co/unLpQMH0hj
Following: 3006 - Followers: 11092
December 10, 2015 at 03:00PM via Twitter http://twitter.com/BJRains
[vue-router] Components show as .
from Google Alert - anonymous http://ift.tt/1NY69Zf
via IFTTT
The case for anonymous case studies
from Google Alert - anonymous http://ift.tt/1NPWv4I
via IFTTT
'Create a new account for an anonymous order' rule don't work
from Google Alert - anonymous http://ift.tt/1lxYsws
via IFTTT
SportsCenter Video: Orioles \"don't want to wait\" for Chris Davis, pulled offer - Buster Olney; willing to re-open talks (ESPN)
via IFTTT
Wednesday, December 9, 2015
I have a new follower on Twitter
Cordny Nederkoorn
Building a community about bird behaviour worldwide
https://t.co/BRsMfyyZpf
Following: 14964 - Followers: 16264
December 09, 2015 at 10:21PM via Twitter http://twitter.com/BirdsBehaviour
A Novel Regularized Principal Graph Learning Framework on Explicit Graph Representation. (arXiv:1512.02752v1 [cs.AI])
Many scientific datasets are of high dimension, and the analysis usually requires visual manipulation by retaining the most important structures of data. Principal curve is a widely used approach for this purpose. However, many existing methods work only for data with structures that are not self-intersected, which is quite restrictive for real applications. A few methods can overcome the above problem, but they either require complicated human-made rules for a specific task with lack of convergence guarantee and adaption flexibility to different tasks, or cannot obtain explicit structures of data. To address these issues, we develop a new regularized principal graph learning framework that captures the local information of the underlying graph structure based on reversed graph embedding. As showcases, models that can learn a spanning tree or a weighted undirected $\ell_1$ graph are proposed, and a new learning algorithm is developed that learns a set of principal points and a graph structure from data, simultaneously. The new algorithm is simple with guaranteed convergence. We then extend the proposed framework to deal with large-scale data. Experimental results on various synthetic and six real world datasets show that the proposed method compares favorably with baselines and can uncover the underlying structure correctly.
from cs.AI updates on arXiv.org http://ift.tt/1jP1URQ
via IFTTT
ShapeNet: An Information-Rich 3D Model Repository. (arXiv:1512.03012v1 [cs.GR])
We present ShapeNet: a richly-annotated, large-scale repository of shapes represented by 3D CAD models of objects. ShapeNet contains 3D models from a multitude of semantic categories and organizes them under the WordNet taxonomy. It is a collection of datasets providing many semantic annotations for each 3D model such as consistent rigid alignments, parts and bilateral symmetry planes, physical sizes, keywords, as well as other planned annotations. Annotations are made available through a public web-based interface to enable data visualization of object attributes, promote data-driven geometric analysis, and provide a large-scale quantitative benchmark for research in computer graphics and vision. At the time of this technical report, ShapeNet has indexed more than 3,000,000 models, 220,000 models out of which are classified into 3,135 categories (WordNet synsets). In this report we describe the ShapeNet effort as a whole, provide details for all currently available datasets, and summarize future plans.
from cs.AI updates on arXiv.org http://ift.tt/1QglapI
via IFTTT
Learning measures of semi-additive behaviour. (arXiv:1512.03020v1 [cs.AI])
In business analytics, measure values, such as sales numbers or volumes of cargo transported, are often summed along values of one or more corresponding categories, such as time or shipping container. However, not every measure should be added by default (e.g., one might more typically want a mean over the heights of a set of people); similarly, some measures should only be summed within certain constraints (e.g., population measures need not be summed over years). In systems such as Watson Analytics, the exact additive behaviour of a measure is often determined by a human expert. In this work, we propose a small set of features for this issue. We use these features in a case-based reasoning approach, where the system suggests an aggregation behaviour, with 86% accuracy in our collected dataset.
from cs.AI updates on arXiv.org http://ift.tt/1jP1URK
via IFTTT
Exploiting Causality for Selective Belief Filtering in Dynamic Bayesian Networks. (arXiv:1401.7941v2 [cs.AI] UPDATED)
Dynamic Bayesian networks (DBNs) are a general model for stochastic processes with partially observed states. Belief filtering in DBNs is the task of inferring the belief state (i.e. the probability distribution over process states) based on incomplete and noisy observations. This can be a hard problem in complex processes with large state space. In this article, we explore the idea of accelerating the filtering task by automatically exploiting causality in the process. We consider a specific type of causal relation, called passivity, which pertains to how state variables cause changes in other variables. We present a novel filtering method, called Passivity-based Monitoring (PM), which maintains a factored belief representation and exploits passivity to perform selective updates over the belief factors. PM produces exact belief states under certain assumptions and approximate belief states otherwise, where the approximation error is bounded by the degree of uncertainty in the process. We show empirically, in synthetic processes with varying sizes and degrees of passivity, that PM is faster than several alternative methods while achieving competitive accuracy. Furthermore, we demonstrate how passivity occurs naturally in a complex system such as a multi-robot warehouse, and how PM can exploit this to accelerate the filtering task.
from cs.AI updates on arXiv.org http://ift.tt/1aLCiAv
via IFTTT
Hinge-Loss Markov Random Fields and Probabilistic Soft Logic. (arXiv:1505.04406v2 [cs.LG] UPDATED)
A fundamental challenge in developing high-impact machine learning technologies is balancing the ability to model rich, structured domains with the ability to scale to big data. Many important problem areas are both richly structured and large scale, from social and biological networks, to knowledge graphs and the Web, to images, video, and natural language. In this paper, we introduce two new formalisms for modeling structured data, distinguished from previous approaches by their ability to both capture rich structure and scale to big data. The first, hinge-loss Markov random fields (HL-MRFs), is a new kind of probabilistic graphical model that generalizes different approaches to convex inference. We unite three approaches from the randomized algorithms, probabilistic graphical models, and fuzzy logic communities, showing that all three lead to the same inference objective. We then derive HL-MRFs by generalizing this unified objective. The second new formalism, probabilistic soft logic (PSL), is a probabilistic programming language that makes HL-MRFs easy to define using a syntax based on first-order logic. We next introduce an algorithm for inferring most-probable variable assignments (MAP inference) that is much more scalable than general-purpose convex optimization software, because it uses message passing to take advantage of sparse dependency structures. We then show how to learn the parameters of HL-MRFs. The learned HL-MRFs are as accurate as analogous discrete models, but much more scalable. Together, these algorithms enable HL-MRFs and PSL to model rich, structured data at scales not previously possible.
from cs.AI updates on arXiv.org http://ift.tt/1AhkWaY
via IFTTT
Belief and Truth in Hypothesised Behaviours. (arXiv:1507.07688v2 [cs.AI] UPDATED)
There is a long history in game theory on the topic of Bayesian or "rational" learning, in which each player maintains beliefs over a set of alternative behaviours, or types, for the other players. This idea has gained increasing interest in the artificial intelligence (AI) community, where it is used as a method to control a single agent in a system composed of multiple agents with unknown behaviours. The idea is to hypothesise a set of types, each specifying a possible behaviour for the other agents, and to plan our own actions with respect to those types which we believe are most likely, given the observed actions of the agents. The game theory literature studies this idea primarily in the context of equilibrium attainment. In contrast, many AI applications have a focus on task completion and payoff maximisation. With this perspective in mind, we identify and address a spectrum of questions pertaining to belief and truth in hypothesised types. We formulate three basic ways to incorporate evidence into posterior beliefs and show when the resulting beliefs are correct, and when they may fail to be correct. Moreover, we demonstrate that prior beliefs can have a significant impact on our ability to maximise payoffs in the long-term, and that they can be computed automatically with consistent performance effects. Furthermore, we analyse the conditions under which we are able complete our task optimally, despite inaccuracies in the hypothesised types. Finally, we show how the correctness of hypothesised types can be ascertained during the interaction via an automated statistical analysis.
from cs.AI updates on arXiv.org http://ift.tt/1JQl9k3
via IFTTT
Return of Frustratingly Easy Domain Adaptation. (arXiv:1511.05547v2 [cs.CV] UPDATED)
Unlike human learning, machine learning often fails to handle changes between training (source) and test (target) input distributions. Such domain shifts, common in practical scenarios, severely damage the performance of conventional machine learning methods. Supervised domain adaptation methods have been proposed for the case when the target data have labels, including some that perform very well despite being "frustratingly easy" to implement. However, in practice, the target domain is often unlabeled, requiring unsupervised adaptation. We propose a simple, effective, and efficient method for unsupervised domain adaptation called CORrelation ALignment (CORAL). CORAL minimizes domain shift by aligning the second-order statistics of source and target distributions, without requiring any target labels. Even though it is extraordinarily simple--it can be implemented in four lines of Matlab code--CORAL performs remarkably well in extensive evaluations on standard benchmark datasets.
from cs.AI updates on arXiv.org http://ift.tt/1WY5345
via IFTTT
Anonymous wants us all to troll ISIS on Friday with hashtag #daeshbags
from Google Alert - anonymous http://ift.tt/1mbkNA1
via IFTTT
Emotions Anonymous Support Group
from Google Alert - anonymous http://ift.tt/1mbkLrX
via IFTTT
[FD] [CVE-2014-3260] Crypto implementation flaws in Pacom GMS System
Source: Gmail -> IFTTT-> Blogger
[FD] APPLE-SA-2015-12-08-3 OS X El Capitan 10.11.2 and Security Update 2015-008
Source: Gmail -> IFTTT-> Blogger
[FD] APPLE-SA-2015-12-08-4 watchOS 2.1
Source: Gmail -> IFTTT-> Blogger
[FD] [CVE-2015-7706] SECURE DATA SPACE API Multiple Non-Persistent Cross-Site Scripting Vulnerabilities
Source: Gmail -> IFTTT-> Blogger
Anonymous hackers declare Friday "Troll ISIS Day"
from Google Alert - anonymous http://ift.tt/1IFpNqN
via IFTTT
Download link token for anonymous users
from Google Alert - anonymous http://ift.tt/1M3DI4z
via IFTTT
[FD] appRain 4.0.3: CSRF
[FD] appRain 4.0.3: Path Traversal
Source: Gmail -> IFTTT-> Blogger
[FD] appRain 4.0.3: XSS
- X
- 5. Solution This issue was not fixed by the vendor. 6. Report Timeline 10/02 Informed Vendor. Mailbox info@apprain.com is full, used /2015 security@apprain.com instead (no reply) 10/21 Reminded Vendor of Disclosure Date /2015 10/21 Vendor anounces fix for 11/02/2015 /2015 11/04 No fix released, extended public disclosure date to 11/11/2015 /2015 11/05 Vendor asks for list of organizations that may help implementing fixes /2015 11/11 Replied that we do not have lists, and that we do not have the resources /2015 to implement fixes ourselves. Extended release date to 11/18/2015 and offered further extension if needed (no reply) 11/17 CVE Requested (no reply) /2015 11/24 Reminded Vendor of release date, extended date to 12/02/2015 and offered /2015 extension if needed (no reply) 12/02 Disclosed to public /2015 Blog Reference: http://ift.tt/1IFbUbX
Source: Gmail -> IFTTT-> Blogger
[FD] redaxscript 2.5.0: Code Execution
Source: Gmail -> IFTTT-> Blogger
[FD] Geeklog 2.1.0: Code Execution
Source: Gmail -> IFTTT-> Blogger
[FD] Geeklog 2.1.0: Code Execution Exploit
[FD] Geeklog 2.1.0: XSS
Source: Gmail -> IFTTT-> Blogger
[FD] phpwcms 1.7.9: Code Execution
Source: Gmail -> IFTTT-> Blogger
[FD] phpwcms 1.7.9: CSRF
Source: Gmail -> IFTTT-> Blogger
[FD] CodoForum 3.4: XSS
Source: Gmail -> IFTTT-> Blogger
[FD] 4images 1.7.11: Code Execution
[FD] 4images 1.7.11: Code Execution Exploit
Source: Gmail -> IFTTT-> Blogger
[FD] 4images 1.7.11: Path Traversal
Source: Gmail -> IFTTT-> Blogger
[FD] 4images 1.7.11: SQL Injection
Source: Gmail -> IFTTT-> Blogger
[FD] SQLMap Code Execute
Source: Gmail -> IFTTT-> Blogger
[FD] ntop-ng <= 2.0.151021 - Privilege Escalation
Source: Gmail -> IFTTT-> Blogger
[FD] Announcing NorthSec 2016 CFP + Reg - Montreal, May 19-22
Source: Gmail -> IFTTT-> Blogger
[FD] [CVE-2015-8369] Cacti SQL injection in graph.php
| \cacti-0.8.8f\lib\rrd.php function rrdtool_function_graph line 631 $rra["timespan"] = 86400; }else{ /* get a list of RRAs related to this graph */ $rras = get_associated_rras($local_graph_id); if (sizeof($rras) > 0) { foreach ($rras as $unchosen_rra) { /* the timespan specified in the RRA "timespan" field may not be accurate */ $real_timespan = ($ds_step * $unchosen_rra["steps"] * $unchosen_rra["rows"]); /* make sure the current start/end times fit within each RRA's timespan */ if ( (($graph_data_array["graph_end"] - $graph_data_array["graph_start"]) <= $real_timespan) && ((time() - $graph_data_array["graph_start"]) <= $real_timespan) ) { /* is this RRA better than the already chosen one? */ if ((isset($rra)) && ($unchosen_rra["steps"] < $rra["steps"])) { $rra = $unchosen_rra; }else if (!isset($rra)) { $rra = $unchosen_rra; } } } } if (!isset($rra)) { $rra["rows"] = 600; $rra["steps"] = 1; } } }else{ // sql injection here $rra = db_fetch_row("select timespan,rows,steps from rra where id=$rra_id"); } [Exploit] poc: http://ift.tt/1Nc02x6 Source: Gmail -> IFTTT-> Blogger |
[FD] Symfony CMS 2.6.3 – Multiple Cross-Site Scripting Vulnerability
Source: Gmail -> IFTTT-> Blogger
Orioles: Baltimore offering 1B Chris Davis a 7-year deal, around $150M - Buster Olney; would be biggest in team history (ESPN)
via IFTTT
ISS Daily Summary Report – 12/8/15
from ISS On-Orbit Status Report http://ift.tt/1PZ2SJH
via IFTTT
It Works! Google's Quantum Computer is '100 Million Times Faster' than a PC
from The Hacker News http://ift.tt/1YYspE6
via IFTTT
Watch the World's First Mind-Controlled Car in Action
from The Hacker News http://ift.tt/1R9zH6s
via IFTTT
Police Raid alleged Bitcoin Creator Craig Wright's Home in Sydney
from The Hacker News http://ift.tt/1HUmcFa
via IFTTT
Bitcoin Creator 'Satoshi Nakamoto' Unmasked! An Australian Man 'Craig Wright' identified...
from The Hacker News http://ift.tt/1HUieMD
via IFTTT
Anonymous threat diverts Air France flight to Montreal
from Google Alert - anonymous http://ift.tt/1NUxADl
via IFTTT
Icelandic Legends and Aurora

Tuesday, December 8, 2015
Sensitivity analysis, multilinearity and beyond. (arXiv:1512.02266v1 [cs.AI])
Sensitivity methods for the analysis of the outputs of discrete Bayesian networks have been extensively studied and implemented in different software packages. These methods usually focus on the study of sensitivity functions and on the impact of a parameter change to the Chan-Darwiche distance. Although not fully recognized, the majority of these results heavily rely on the multilinear structure of atomic probabilities in terms of the conditional probability parameters associated with this type of network. By defining a statistical model through the polynomial expression of its associated defining conditional probabilities, we develop a unifying approach to sensitivity methods applicable to a large suite of models including extensions of Bayesian networks, for instance context-specific and dynamic ones, and chain event graphs. By then focusing on models whose defining polynomial is multilinear, our algebraic approach enables us to prove that the Chan-Darwiche distance is minimized for a certain class of multi-parameter contemporaneous variations when parameters are proportionally covaried.
from cs.AI updates on arXiv.org http://ift.tt/1M21BcZ
via IFTTT
Learning Discrete Bayesian Networks from Continuous Data. (arXiv:1512.02406v1 [cs.AI])
Real data often contains a mixture of discrete and continuous variables, but many Bayesian network structure learning and inference algorithms assume all random variables are discrete. Continuous variables are often discretized, but the choice of discretization policy has significant impact on the accuracy, speed, and interpretability of the resulting models. This paper introduces a principled Bayesian discretization method for continuous variables in Bayesian networks with quadratic complexity instead of the cubic complexity of other standard techniques. Empirical demonstrations show that the proposed method is superior to the state of the art. In addition, this paper shows how to incorporate existing methods into the structure learning process to discretize all continuous variables and simultaneously learn Bayesian network structures.
from cs.AI updates on arXiv.org http://ift.tt/1M21CgY
via IFTTT
Stochastic And-Or Grammars: A Unified Framework and Logic Perspective. (arXiv:1506.00858v2 [cs.AI] UPDATED)
Stochastic And-Or grammars (AOG) extend traditional stochastic grammars of language to model other types of data such as images and events. In this paper we propose a representation framework of stochastic AOGs that is agnostic to the type of the data being modeled and thus unifies various domain-specific AOGs. Many existing grammar formalisms and probabilistic models in natural language processing, computer vision, and machine learning can be seen as special cases of this framework. We also propose a domain-independent inference algorithm of stochastic context-free AOGs and show its tractability under a reasonable assumption. Furthermore, we provide an interpretation of stochastic context-free AOGs as a subset of first-order probabilistic logic, which connects stochastic AOGs to the field of statistical relational learning. Based on the interpretation, we clarify the relation between stochastic AOGs and a few existing statistical relational models.
from cs.AI updates on arXiv.org http://ift.tt/1MiLJ8p
via IFTTT
On-the-Job Learning with Bayesian Decision Theory. (arXiv:1506.03140v2 [cs.AI] UPDATED)
Our goal is to deploy a high-accuracy system starting with zero training examples. We consider an "on-the-job" setting, where as inputs arrive, we use real-time crowdsourcing to resolve uncertainty where needed and output our prediction when confident. As the model improves over time, the reliance on crowdsourcing queries decreases. We cast our setting as a stochastic game based on Bayesian decision theory, which allows us to balance latency, cost, and accuracy objectives in a principled way. Computing the optimal policy is intractable, so we develop an approximation based on Monte Carlo Tree Search. We tested our approach on three datasets---named-entity recognition, sentiment classification, and image classification. On the NER task we obtained more than an order of magnitude reduction in cost compared to full human annotation, while boosting performance relative to the expert provided labels. We also achieve a 8% F1 improvement over having a single human label the whole set, and a 28% F1 improvement over online learning.
from cs.AI updates on arXiv.org http://ift.tt/1TcnYUd
via IFTTT
Fast Convergence of Regularized Learning in Games. (arXiv:1507.00407v4 [cs.GT] UPDATED)
We show that natural classes of regularized learning algorithms with a form of recency bias achieve faster convergence rates to approximate efficiency and to coarse correlated equilibria in multiplayer normal form games. When each player in a game uses an algorithm from our class, their individual regret decays at $O(T^{-3/4})$, while the sum of utilities converges to an approximate optimum at $O(T^{-1})$--an improvement upon the worst case $O(T^{-1/2})$ rates. We show a black-box reduction for any algorithm in the class to achieve $\tilde{O}(T^{-1/2})$ rates against an adversary, while maintaining the faster rates against algorithms in the class. Our results extend those of [Rakhlin and Shridharan 2013] and [Daskalakis et al. 2014], who only analyzed two-player zero-sum games for specific algorithms.
from cs.AI updates on arXiv.org http://ift.tt/1JB6JcL
via IFTTT
[FD] MacOS/iPhone/Apple Watch/Apple TV libc File System Buffer Overflow
Source: Gmail -> IFTTT-> Blogger
Anonymous declares this Friday 'ISIS trolling day'
from Google Alert - anonymous http://ift.tt/1lMrBDI
via IFTTT
Ravens: Baltimore (4-8) drops five spots to No. 30 in Week 14 NFL power rankings; open here for full rankings (ESPN)
via IFTTT
ISS Daily Summary Report – 12/7/15
from ISS On-Orbit Status Report http://ift.tt/1ICjwMz
via IFTTT