Latest YouTube Video
Saturday, October 22, 2016
Viagra Anonymous
from Google Alert - anonymous http://ift.tt/2eFIkH4
via IFTTT
Ravens: QB Joe Flacco (shoulder) will be active for Sunday's game vs. Jets; was expected to be game-time decision (ESPN)
via IFTTT
Anonymous Art Auction
from Google Alert - anonymous http://ift.tt/2er7Z8H
via IFTTT
An Army of Million Hacked IoT Devices Almost Broke the Internet Today
from The Hacker News http://ift.tt/2dXavQo
via IFTTT
Friday, October 21, 2016
Warriors' Thompson angered by anonymous 'coward'
from Google Alert - anonymous http://ift.tt/2epHjVT
via IFTTT
Ravens: Joe Flacco (shoulder) questionable and will be game-time decision Sunday at Jets; Steve Smith Sr. (ankle) out (ESPN)
via IFTTT
Ravens: Joe Flacco returns to practice Friday after missing past two days; showed no effects from injured right shoulder (ESPN)
via IFTTT
Royals, Rangers and Orioles rank among the top MLB teams in ESPN The Magazine's 2016 Ultimate Standings (ESPN)
via IFTTT
Massive DDoS Attack Against Dyn DNS Causes Major Outages to Popular Sites
from The Hacker News http://ift.tt/2dtj49v
via IFTTT
ISS Daily Summary Report – 10/20/2016
from ISS On-Orbit Status Report http://ift.tt/2eqCwRf
via IFTTT
"Fraud" payments for anonymous orders
from Google Alert - anonymous http://ift.tt/2eA7xBv
via IFTTT
Georgetown Prep Receives $20 Million Gift From Anonymous Donor
from Google Alert - anonymous http://ift.tt/2dFSpVw
via IFTTT
You are less anonymous on the web than you think — much less.
from Google Alert - anonymous http://ift.tt/2eA7IN1
via IFTTT
Dirty COW — Critical Linux Kernel Flaw Being Exploited in the Wild
from The Hacker News http://ift.tt/2ecPwMs
via IFTTT
Ex-NSA Contractor Stole 50 TB of Data; Includes Top-Secret Hacking Tools
from The Hacker News http://ift.tt/2erDLA9
via IFTTT
network-anonymous-tor
from Google Alert - anonymous http://ift.tt/2epGdq2
via IFTTT
The Tulip in the Swan

Thursday, October 20, 2016
anonymous-sums
from Google Alert - anonymous http://ift.tt/2eMpPUY
via IFTTT
Maximizing positive opinion influence using an evidential approach. (arXiv:1610.06340v1 [cs.SI])
In this paper, we propose a new data based model for influence maximization in online social networks. We use the theory of belief functions to overcome the data imperfection problem. Besides, the proposed model searches to detect influencer users that adopt a positive opinion about the product, the idea, etc, to be propagated. Moreover, we present some experiments to show the performance of our model.
from cs.AI updates on arXiv.org http://ift.tt/2epbGc0
via IFTTT
Dynamic Probabilistic Network Based Human Action Recognition. (arXiv:1610.06395v1 [cs.CV])
This paper examines use of dynamic probabilistic networks (DPN) for human action recognition. The actions of lifting objects and walking in the room, sitting in the room and neutral standing pose were used for testing the classification. The research used the dynamic interrelation between various different regions of interest (ROI) on the human body (face, body, arms, legs) and the time series based events related to the these ROIs. This dynamic links are then used to recognize the human behavioral aspects in the scene. First a model is developed to identify the human activities in an indoor scene and this model is dependent on the key features and interlinks between the various dynamic events using DPNs. The sub ROI are classified with DPN to associate the combined interlink with a specific human activity. The recognition accuracy performance between indoor (controlled lighting conditions) is compared with the outdoor lighting conditions. The accuracy in outdoor scenes was lower than the controlled environment.
from cs.AI updates on arXiv.org http://ift.tt/2edaYDq
via IFTTT
A Growing Long-term Episodic & Semantic Memory. (arXiv:1610.06402v1 [cs.AI])
The long-term memory of most connectionist systems lies entirely in the weights of the system. Since the number of weights is typically fixed, this bounds the total amount of knowledge that can be learned and stored. Though this is not normally a problem for a neural network designed for a specific task, such a bound is undesirable for a system that continually learns over an open range of domains. To address this, we describe a lifelong learning system that leverages a fast, though non-differentiable, content-addressable memory which can be exploited to encode both a long history of sequential episodic knowledge and semantic knowledge over many episodes for an unbounded number of domains. This opens the door for investigation into transfer learning, and leveraging prior knowledge that has been learned over a lifetime of experiences to new domains.
from cs.AI updates on arXiv.org http://ift.tt/2eo3Ocf
via IFTTT
Exploiting inter-image similarity and ensemble of extreme learners for fixation prediction using deep features. (arXiv:1610.06449v1 [cs.CV])
This paper presents a novel fixation prediction and saliency modeling framework based on inter-image similarities and ensemble of Extreme Learning Machines (ELM). The proposed framework is inspired by two observations, 1) the contextual information of a scene along with low-level visual cues modulates attention, 2) the influence of scene memorability on eye movement patterns caused by the resemblance of a scene to a former visual experience. Motivated by such observations, we develop a framework that estimates the saliency of a given image using an ensemble of extreme learners, each trained on an image similar to the input image. That is, after retrieving a set of similar images for a given image, a saliency predictor is learnt from each of the images in the retrieved image set using an ELM, resulting in an ensemble. The saliency of the given image is then measured in terms of the mean of predicted saliency value by the ensemble's members.
from cs.AI updates on arXiv.org http://ift.tt/2epa4iB
via IFTTT
Reasoning with Memory Augmented Neural Networks for Language Comprehension. (arXiv:1610.06454v1 [cs.CL])
Hypothesis testing is an important cognitive process that supports human reasoning. In this paper, we introduce a computational hypothesis testing approach based on memory augmented neural networks. Our approach involves a hypothesis testing loop that reconsiders and progressively refines a previously formed hypothesis in order to generate new hypotheses to test. We apply the proposed approach to language comprehension task by using Neural Semantic Encoders (NSE). Our NSE models achieve the state-of-the-art results showing an absolute improvement of 1.2% to 2.6% accuracy over previous results obtained by single and ensemble systems on standard machine comprehension benchmarks such as the Children's Book Test (CBT) and Who-Did-What (WDW) news article datasets.
from cs.AI updates on arXiv.org http://ift.tt/2ebuOg3
via IFTTT
Generalized Interval-valued OWA Operators with Interval Weights Derived from Interval-valued Overlap Functions. (arXiv:1610.06473v1 [cs.AI])
In this work we extend to the interval-valued setting the notion of an overlap functions and we discuss a method which makes use of interval-valued overlap functions for constructing OWA operators with interval-valued weights. . Some properties of interval-valued overlap functions and the derived interval-valued OWA operators are analysed. We specially focus on the homogeneity and migrativity properties.
from cs.AI updates on arXiv.org http://ift.tt/2eLZO8b
via IFTTT
An Extended Neo-Fuzzy Neuron and its Adaptive Learning Algorithm. (arXiv:1610.06483v1 [cs.AI])
A modification of the neo-fuzzy neuron is proposed (an extended neo-fuzzy neuron (ENFN)) that is characterized by improved approximating properties. An adaptive learning algorithm is proposed that has both tracking and smoothing properties. An ENFN distinctive feature is its computational simplicity compared to other artificial neural networks and neuro-fuzzy systems.
from cs.AI updates on arXiv.org http://ift.tt/2eo51QZ
via IFTTT
An Evolving Cascade System Based on A Set Of Neo Fuzzy Nodes. (arXiv:1610.06484v1 [cs.AI])
Neo-fuzzy elements are used as nodes for an evolving cascade system. The proposed system can tune both its parameters and architecture in an online mode. It can be used for solving a wide range of Data Mining tasks (namely time series forecasting). The evolving cascade system with neo-fuzzy nodes can process rather large data sets with high speed and effectiveness.
from cs.AI updates on arXiv.org http://ift.tt/2eM24MO
via IFTTT
A Multidimensional Cascade Neuro-Fuzzy System with Neuron Pool Optimization in Each Cascade. (arXiv:1610.06485v1 [cs.AI])
A new architecture and learning algorithms for the multidimensional hybrid cascade neural network with neuron pool optimization in each cascade are proposed in this paper. The proposed system differs from the well-known cascade systems in its capability to process multidimensional time series in an online mode, which makes it possible to process non-stationary stochastic and chaotic signals with the required accuracy. Compared to conventional analogs, the proposed system provides computational simplicity and possesses both tracking and filtering capabilities.
from cs.AI updates on arXiv.org http://ift.tt/2eo7gE3
via IFTTT
Adaptive Forecasting of Non-Stationary Nonlinear Time Series Based on the Evolving Weighted Neuro-Neo-Fuzzy-ANARX-Model. (arXiv:1610.06486v1 [cs.AI])
An evolving weighted neuro-neo-fuzzy-ANARX model and its learning procedures are introduced in the article. This system is basically used for time series forecasting. This system may be considered as a pool of elements that process data in a parallel manner. The proposed evolving system may provide online processing data streams.
from cs.AI updates on arXiv.org http://ift.tt/2eM09rw
via IFTTT
An Evolving Neuro-Fuzzy System with Online Learning/Self-learning. (arXiv:1610.06488v1 [cs.AI])
An architecture of a new neuro-fuzzy system is proposed. The basic idea of this approach is to tune both synaptic weights and membership functions with the help of the supervised learning and self-learning paradigms. The approach to solving the problem has to do with evolving online neuro-fuzzy systems that can process data under uncertainty conditions. The results prove the effectiveness of the developed architecture and the learning procedure.
from cs.AI updates on arXiv.org http://ift.tt/2eo6iaN
via IFTTT
An Ensemble of Adaptive Neuro-Fuzzy Kohonen Networks for Online Data Stream Fuzzy Clustering. (arXiv:1610.06490v1 [cs.AI])
A new approach to data stream clustering with the help of an ensemble of adaptive neuro-fuzzy systems is proposed. The proposed ensemble is formed with adaptive neuro-fuzzy self-organizing Kohonen maps in a parallel processing mode. A final result is chosen by the best neuro-fuzzy self-organizing Kohonen map.
from cs.AI updates on arXiv.org http://ift.tt/2eM0Wsj
via IFTTT
Jointly Learning to Align and Convert Graphemes to Phonemes with Neural Attention Models. (arXiv:1610.06540v1 [cs.CL])
We propose an attention-enabled encoder-decoder model for the problem of grapheme-to-phoneme conversion. Most previous work has tackled the problem via joint sequence models that require explicit alignments for training. In contrast, the attention-enabled encoder-decoder model allows for jointly learning to align and convert characters to phonemes. We explore different types of attention models, including global and local attention, and our best models achieve state-of-the-art results on three standard data sets (CMUDict, Pronlex, and NetTalk).
from cs.AI updates on arXiv.org http://ift.tt/2drOmh7
via IFTTT
IDE0008 Do not offer explicit type instead of var for anonymous objects · Issue #14635
from Google Alert - anonymous http://ift.tt/2e5FqvE
via IFTTT
"Society's Best Kept Secret": Jackie O's Anonymous Wedding Dress Designer
from Google Alert - anonymous http://ift.tt/2exQdwI
via IFTTT
I have a new follower on Twitter
FirmRight
Following: 1969 - Followers: 581
October 20, 2016 at 04:01PM via Twitter http://twitter.com/FirmRight
Over 43 Million Weebly Accounts Hacked; Foursquare Also Hit By Data Breach
from The Hacker News http://ift.tt/2eL6zr5
via IFTTT
Over 43 Million Weebly Accounts Hacked; Foursquare Also Hit By Data Breach
from The Hacker News http://ift.tt/2eL6zr5
via IFTTT
Ravens: LB Elvis Dumervil (foot) believes he will play again in 2016, but has no timetable for return; "I wish I did" (ESPN)
via IFTTT
Gamblers Anonymous
from Google Alert - anonymous http://ift.tt/2eob1aS
via IFTTT
MBRFilter — Open Source Tool to Protect Against 'Master Boot Record' Malware
from The Hacker News http://ift.tt/2ekI5DC
via IFTTT
Ravens: QB Joe Flacco (shoulder) misses his second straight day of practice Thursday; injured Sunday vs. Giants (ESPN)
via IFTTT
Massive ATM Hack Hits 3.2 Million Indian Debit Cards — Change Your PIN Now!
from The Hacker News http://ift.tt/2ebrgg7
via IFTTT
Dios (Gaiser's Atheists Anonymous Remix)
from Google Alert - anonymous http://ift.tt/2dD58bC
via IFTTT
ISS Daily Summary Report – 10/19/2016
from ISS On-Orbit Status Report http://ift.tt/2eUZd3r
via IFTTT
M45: The Pleiades Star Cluster

Wednesday, October 19, 2016
Particle Swarm Optimization for Generating Fuzzy Reinforcement Learning Policies. (arXiv:1610.05984v1 [cs.NE])
Fuzzy controllers are known to serve as efficient and interpretable system controllers for continuous state and action spaces. To date these controllers have been constructed by hand, or automatically trained either on expert generated problem specific cost functions or by incorporating detailed knowledge about the optimal control strategy. Both requirements for automatic training processes are not given in the majority of real world reinforcement learning (RL) problems. We introduce a new particle swarm reinforcement learning (PSRL) approach which is capable of constructing fuzzy RL policies solely by training parameters on world models produced from randomly generated samples of the real system. This approach relates self-organizing fuzzy controllers to model-based RL for the first time. PSRL can be used straightforward on any RL problem, which is demonstrated on three standard RL benchmarks, mountain car, cart pole balancing and cart pole swing up. Our experiments yielded high performing and well interpretable fuzzy policies.
from cs.AI updates on arXiv.org http://ift.tt/2e2BtYH
via IFTTT
Constrained Cohort Intelligence using Static and Dynamic Penalty Function Approach for Mechanical Components Design. (arXiv:1610.06009v1 [cs.AI])
Most of the metaheuristics can efficiently solve unconstrained problems; however, their performance may degenerate if the constraints are involved. This paper proposes two constraint handling approaches for an emerging metaheuristic of Cohort Intelligence (CI). More specifically CI with static penalty function approach (SCI) and CI with dynamic penalty function approach (DCI) are proposed. The approaches have been tested by solving several constrained test problems. The performance of the SCI and DCI have been compared with algorithms like GA, PSO, ABC, d-Ds. In addition, as well as three real world problems from mechanical engineering domain with improved solutions. The results were satisfactory and validated the applicability of CI methodology for solving real world problems.
from cs.AI updates on arXiv.org http://ift.tt/2elCxdz
via IFTTT
Fairness as a Program Property. (arXiv:1610.06067v1 [cs.PL])
We explore the following question: Is a decision-making program fair, for some useful definition of fairness? First, we describe how several algorithmic fairness questions can be phrased as program verification problems. Second, we discuss an automated verification technique for proving or disproving fairness of decision-making programs with respect to a probabilistic model of the population.
from cs.AI updates on arXiv.org http://ift.tt/2drn2uo
via IFTTT
Recognizing Semantic Features in Faces using Deep Learning. (arXiv:1512.00743v2 [cs.LG] UPDATED)
The human face constantly conveys information, both consciously and subconsciously. However, as basic as it is for humans to visually interpret this information, it is quite a big challenge for machines. Conventional semantic facial feature recognition and analysis techniques are already in use and are based on physiological heuristics, but they suffer from lack of robustness and high computation time. This thesis aims to explore ways for machines to learn to interpret semantic information available in faces in an automated manner without requiring manual design of feature detectors, using the approach of Deep Learning. This thesis provides a study of the effects of various factors and hyper-parameters of deep neural networks in the process of determining an optimal network configuration for the task of semantic facial feature recognition. This thesis explores the effectiveness of the system to recognize the various semantic features (like emotions, age, gender, ethnicity etc.) present in faces. Furthermore, the relation between the effect of high-level concepts on low level features is explored through an analysis of the similarities in low-level descriptors of different semantic features. This thesis also demonstrates a novel idea of using a deep network to generate 3-D Active Appearance Models of faces from real-world 2-D images.
For a more detailed report on this work, please see [arXiv:1512.00743v1].
from cs.AI updates on arXiv.org http://ift.tt/1XIqQYm
via IFTTT
Human Pose Estimation in Space and Time using 3D CNN. (arXiv:1609.00036v3 [cs.CV] UPDATED)
This paper explores the capabilities of convolutional neural networks to deal with a task that is easily manageable for humans: perceiving 3D pose of a human body from varying angles. However, in our approach, we are restricted to using a monocular vision system. For this purpose, we apply a convolutional neural network approach on RGB videos and extend it to three dimensional convolutions. This is done via encoding the time dimension in videos as the 3\ts{rd} dimension in convolutional space, and directly regressing to human body joint positions in 3D coordinate space. This research shows the ability of such a network to achieve state-of-the-art performance on the selected Human3.6M dataset, thus demonstrating the possibility of successfully representing temporal data with an additional dimension in the convolutional operation.
from cs.AI updates on arXiv.org http://ift.tt/2bUFCuM
via IFTTT
Learning to learn with backpropagation of Hebbian plasticity. (arXiv:1609.02228v2 [cs.NE] UPDATED)
Hebbian plasticity is a powerful principle that allows biological brains to learn from their lifetime experience. By contrast, artificial neural networks trained with backpropagation generally have fixed connection weights that do not change once training is complete. While recent methods can endow neural networks with long-term memories, Hebbian plasticity is currently not amenable to gradient descent. Here we derive analytical expressions for activity gradients in neural networks with Hebbian plastic connections. Using these expressions, we can use backpropagation to train not just the baseline weights of the connections, but also their plasticity. As a result, the networks "learn how to learn" in order to solve the problem at hand: the trained networks automatically perform fast learning of unpredictable environmental features during their lifetime, expanding the range of solvable problems. We test the algorithm on various on-line learning tasks, including pattern completion, one-shot learning, and reversal learning. The algorithm successfully learns how to learn the relevant associations from one-shot instruction, and fine-tunes the temporal dynamics of plasticity to allow for continual learning in response to changing environmental parameters. We conclude that backpropagation of Hebbian plasticity offers a powerful model for lifelong learning.
from cs.AI updates on arXiv.org http://ift.tt/2cxDnyC
via IFTTT
Re: [FD] Critical Vulnerability in Ubiquiti UniFi
Source: Gmail -> IFTTT-> Blogger
[FD] Ubiquiti
Source: Gmail -> IFTTT-> Blogger
[FD] CVE-2016-7999: SPIP 3.1.2 Server Side Request Forgery
Source: Gmail -> IFTTT-> Blogger
[FD] CVE-2016-7982: SPIP 3.1.1/3.1.2 File Enumeration / Path Traversal
", $titre, '
', $bandeau, '
', "
Source: Gmail -> IFTTT-> Blogger
[FD] CVE-2016-7981: SPIP 3.1.2 Reflected Cross-Site Scripting
", $titre, '
', $bandeau, '
', ### Timeline (dd/mm/yyyy) * 15/09/2016 : Initial discovery * 26/09/2016 : Contact with SPIP Team * 27/09/2016 : Answer from SPIP Team, sent advisory details * 27/09/2016 : Incorrect fix from SPIP Team. * 27/09/2016 : New proof of concept for bypassing fixes for XSS sent. * 27/09/2016 : Fixes issued for XSS (23185). * 30/09/2016 : SPIP 3.1.3 Released ### Fixes * http://ift.tt/2dt1cMd * http://ift.tt/2d44Eun * http://ift.tt/2dt0zm9 ### Affected versions * Version <= 3.1.2 ### Credits * Nicolas CHATELAIN, Sysdream (n.chatelain -at- sysdream -dot- com)Source: Gmail -> IFTTT-> Blogger
[FD] CVE-2016-7980: SPIP 3.1.2 Exec Code Cross-Site Request Forgery
Source: Gmail -> IFTTT-> Blogger
Busted! Anonymous Drops a Massive Bomb on Hillary, Just Before NV Debate!
from Google Alert - anonymous http://ift.tt/2dASidy
via IFTTT
[FD] OpenSSL 1.1.0 remote client memory corruption
Source: Gmail -> IFTTT-> Blogger
[FD] [ERPSCAN-16-029] SAP NetWeaver AS JAVA - deserialization of untrusted user value
Source: Gmail -> IFTTT-> Blogger
[FD] [ERPSCAN-16-028] SAP Adaptive Server Enterprise - DoS vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] CVE-2016-8600 dotCMS - CAPTCHA bypass by reusing valid code
Source: Gmail -> IFTTT-> Blogger
Breaking — Russian Hacker Responsible for LinkedIn Data Breach Arrested by FBI
from The Hacker News http://ift.tt/2et9jUR
via IFTTT
Russian Hacker who was wanted by FBI arrested in Prague
from The Hacker News http://ift.tt/2ehAaGP
via IFTTT
Ravens: QB Joe Flacco dealing with right shoulder injury, still has "legitimate shot" at playing Sunday - John Harbaugh (ESPN)
via IFTTT
Ravens: QB Joe Flacco not practicing Wednesday after taking several hard hits against Giants on Sunday (ESPN)
via IFTTT
ISS Daily Summary Report – 10/18/2016
from ISS On-Orbit Status Report http://ift.tt/2egNnzV
via IFTTT
Police Scan 117 Million Driving Licence Photos for Face Recognition Database
from The Hacker News http://ift.tt/2e0LhSV
via IFTTT
Winers Anonymous
from Google Alert - anonymous http://ift.tt/2ekmclF
via IFTTT
16 OCT 16 CMA Announcements
from Google Alert - anonymous http://ift.tt/2ejQpou
via IFTTT
The Antlia Cluster of Galaxies
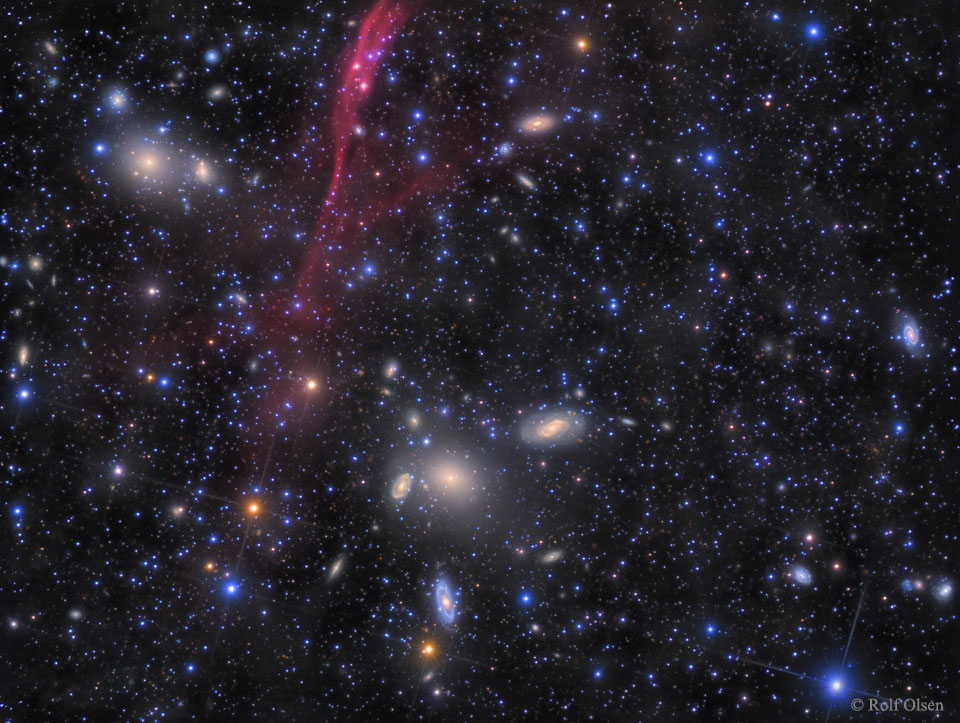
Tuesday, October 18, 2016
VRPBench: A Vehicle Routing Benchmark Tool. (arXiv:1610.05402v1 [cs.AI])
The number of optimization techniques in the combinatorial domain is large and diversified. Nevertheless, there is still a lack of real benchmarks to validate optimization algorithms. In this work we introduce VRPBench, a tool to create instances and visualize solutions to the Vehicle Routing Problem (VRP) in a planar graph embedded in the Euclidean 2D space. We use VRPBench to model a real-world mail delivery case of the city of Artur Nogueira. Such scenarios were characterized as a multi-objective optimization of the VRP. We extracted a weighted graph from a digital map of the city to create a challenging benchmark for the VRP. Each instance models one generic day of mail delivery with hundreds to thousands of delivery points, thus allowing both the comparison and validation of optimization algorithms for routing problems.
from cs.AI updates on arXiv.org http://ift.tt/2dlXvYr
via IFTTT
Makespan Optimal Solving of Cooperative Path-Finding via Reductions to Propositional Satisfiability. (arXiv:1610.05452v1 [cs.AI])
The problem of makespan optimal solving of cooperative path finding (CPF) is addressed in this paper. The task in CPF is to relocate a group of agents in a non-colliding way so that each agent eventually reaches its goal location from the given initial location. The abstraction adopted in this work assumes that agents are discrete items moving in an undirected graph by traversing edges. Makespan optimal solving of CPF means to generate solutions that are as short as possi-ble in terms of the total number of time steps required for the execution of the solution.
We show that reducing CPF to propositional satisfiability (SAT) represents a viable option for obtaining makespan optimal solutions. Several encodings of CPF into propositional formulae are suggested and experimentally evaluated. The evaluation indicates that SAT based CPF solving outperforms other makespan optimal methods significantly in highly constrained situations (environments that are densely occupied by agents).
from cs.AI updates on arXiv.org http://ift.tt/2dZO4Mk
via IFTTT
Diagnosis of aerospace structure defects by a HPC implemented soft computing algorithm. (arXiv:1610.05521v1 [cs.AI])
This study concerns with the diagnosis of aerospace structure defects by applying a HPC parallel implementation of a novel learning algorithm, named U-BRAIN. The Soft Computing approach allows advanced multi-parameter data processing in composite materials testing. The HPC parallel implementation overcomes the limits due to the great amount of data and the complexity of data processing. Our experimental results illustrate the effectiveness of the U-BRAIN parallel implementation as defect classifier in aerospace structures. The resulting system is implemented on a Linux-based cluster with multi-core architecture.
from cs.AI updates on arXiv.org http://ift.tt/2dlZxYq
via IFTTT
Weighted Positive Binary Decision Diagrams for Exact Probabilistic Inference. (arXiv:1610.05551v1 [cs.AI])
Recent work on weighted model counting has been very successfully applied to the problem of probabilistic inference in Bayesian networks. The probability distribution is encoded into a Boolean normal form and compiled to a target language, in order to represent local structure expressed among conditional probabilities more efficiently. We show that further improvements are possible, by exploiting the knowledge that is lost during the encoding phase and incorporating it into a compiler inspired by Satisfiability Modulo Theories. Constraints among variables are used as a background theory, which allows us to optimize the Shannon decomposition. We propose a new language, called Weighted Positive Binary Decision Diagrams, that reduces the cost of probabilistic inference by using this decomposition variant to induce an arithmetic circuit of reduced size.
from cs.AI updates on arXiv.org http://ift.tt/2dZMREG
via IFTTT
Identifiability and Transportability in Dynamic Causal Networks. (arXiv:1610.05556v1 [cs.AI])
In this paper we propose a causal analog to the purely observational Dynamic Bayesian Networks, which we call Dynamic Causal Networks. We provide a sound and complete algorithm for identification of Dynamic Causal Net- works, namely, for computing the effect of an intervention or experiment, based on passive observations only, whenever possible. We note the existence of two types of confounder variables that affect in substantially different ways the iden- tification procedures, a distinction with no analog in either Dynamic Bayesian Networks or standard causal graphs. We further propose a procedure for the transportability of causal effects in Dynamic Causal Network settings, where the re- sult of causal experiments in a source domain may be used for the identification of causal effects in a target domain.
from cs.AI updates on arXiv.org http://ift.tt/2dlZcoM
via IFTTT
Census Signal Temporal Logic Inference for Multi-Agent Group Behavior Analysis. (arXiv:1610.05612v1 [cs.AI])
In this paper, we define a novel census signal temporal logic (CensusSTL) that focuses on the number of agents in different subsets of a group that complete a certain task specified by the signal temporal logic (STL). CensusSTL consists of an "inner logic" STL formula and an "outer logic" STL formula. We present a new inference algorithm to infer CensusSTL formulae from the trajectory data of a group of agents. We first identify the "inner logic" STL formula and then infer the subgroups based on whether the agents' behaviors satisfy the "inner logic" formula at each time point. We use two different approaches to infer the subgroups based on similarity and complementarity, respectively. The "outer logic" CensusSTL formula is inferred from the census trajectories of different subgroups. We apply the algorithm in analyzing data from a soccer match by inferring the CensusSTL formula for different subgroups of a soccer team.
from cs.AI updates on arXiv.org http://ift.tt/2dZNVZe
via IFTTT
Low-rank and Sparse Soft Targets to Learn Better DNN Acoustic Models. (arXiv:1610.05688v1 [cs.CL])
Conventional deep neural networks (DNN) for speech acoustic modeling rely on Gaussian mixture models (GMM) and hidden Markov model (HMM) to obtain binary class labels as the targets for DNN training. Subword classes in speech recognition systems correspond to context-dependent tied states or senones. The present work addresses some limitations of GMM-HMM senone alignments for DNN training. We hypothesize that the senone probabilities obtained from a DNN trained with binary labels can provide more accurate targets to learn better acoustic models. However, DNN outputs bear inaccuracies which are exhibited as high dimensional unstructured noise, whereas the informative components are structured and low-dimensional. We exploit principle component analysis (PCA) and sparse coding to characterize the senone subspaces. Enhanced probabilities obtained from low-rank and sparse reconstructions are used as soft-targets for DNN acoustic modeling, that also enables training with untranscribed data. Experiments conducted on AMI corpus shows 4.6% relative reduction in word error rate.
from cs.AI updates on arXiv.org http://ift.tt/2dMMAmF
via IFTTT
Design Mining Microbial Fuel Cell Cascades. (arXiv:1610.05716v1 [cs.NE])
Microbial fuel cells (MFCs) perform wastewater treatment and electricity production through the conversion of organic matter using microorganisms. For practical applications, it has been suggested that greater efficiency can be achieved by arranging multiple MFC units into physical stacks in a cascade with feedstock flowing sequentially between units. In this paper, we investigate the use of computational intelligence to physically explore and optimise (potentially) heterogeneous MFC designs in a cascade, i.e. without simulation. Conductive structures are 3-D printed and inserted into the anodic chamber of each MFC unit, augmenting a carbon fibre veil anode and affecting the hydrodynamics, including the feedstock volume and hydraulic retention time, as well as providing unique habitats for microbial colonisation. We show that it is possible to use design mining to identify new conductive inserts that increase both the cascade power output and power density.
from cs.AI updates on arXiv.org http://ift.tt/2dm3pZm
via IFTTT
Deep Amortized Inference for Probabilistic Programs. (arXiv:1610.05735v1 [cs.AI])
Probabilistic programming languages (PPLs) are a powerful modeling tool, able to represent any computable probability distribution. Unfortunately, probabilistic program inference is often intractable, and existing PPLs mostly rely on expensive, approximate sampling-based methods. To alleviate this problem, one could try to learn from past inferences, so that future inferences run faster. This strategy is known as amortized inference; it has recently been applied to Bayesian networks and deep generative models. This paper proposes a system for amortized inference in PPLs. In our system, amortization comes in the form of a parameterized guide program. Guide programs have similar structure to the original program, but can have richer data flow, including neural network components. These networks can be optimized so that the guide approximately samples from the posterior distribution defined by the original program. We present a flexible interface for defining guide programs and a stochastic gradient-based scheme for optimizing guide parameters, as well as some preliminary results on automatically deriving guide programs. We explore in detail the common machine learning pattern in which a 'local' model is specified by 'global' random values and used to generate independent observed data points; this gives rise to amortized local inference supporting global model learning.
from cs.AI updates on arXiv.org http://ift.tt/2dMJVt7
via IFTTT
Fast Sampling for Bayesian Max-Margin Models. (arXiv:1504.07107v5 [stat.ML] UPDATED)
Bayesian max-margin models have shown superiority in various practical applications, such as text categorization, collaborative prediction, social network link prediction and crowdsourcing, and they conjoin the flexibility of Bayesian modeling and predictive strengths of max-margin learning. However, Monte Carlo sampling for these models still remains challenging, especially for applications that involve large-scale datasets. In this paper, we present the stochastic subgradient Hamiltonian Monte Carlo (HMC) methods, which are easy to implement and computationally efficient. We show the approximate detailed balance property of subgradient HMC which reveals a natural and validated generalization of the ordinary HMC. Furthermore, we investigate the variants that use stochastic subsampling and thermostats for better scalability and mixing. Using stochastic subgradient Markov Chain Monte Carlo (MCMC), we efficiently solve the posterior inference task of various Bayesian max-margin models and extensive experimental results demonstrate the effectiveness of our approach.
from cs.AI updates on arXiv.org http://ift.tt/1JMjVYd
via IFTTT
Unsupervised Learning for Physical Interaction through Video Prediction. (arXiv:1605.07157v4 [cs.LG] UPDATED)
A core challenge for an agent learning to interact with the world is to predict how its actions affect objects in its environment. Many existing methods for learning the dynamics of physical interactions require labeled object information. However, to scale real-world interaction learning to a variety of scenes and objects, acquiring labeled data becomes increasingly impractical. To learn about physical object motion without labels, we develop an action-conditioned video prediction model that explicitly models pixel motion, by predicting a distribution over pixel motion from previous frames. Because our model explicitly predicts motion, it is partially invariant to object appearance, enabling it to generalize to previously unseen objects. To explore video prediction for real-world interactive agents, we also introduce a dataset of 59,000 robot interactions involving pushing motions, including a test set with novel objects. In this dataset, accurate prediction of videos conditioned on the robot's future actions amounts to learning a "visual imagination" of different futures based on different courses of action. Our experiments show that our proposed method produces more accurate video predictions both quantitatively and qualitatively, when compared to prior methods.
from cs.AI updates on arXiv.org http://ift.tt/1Ua9BQ7
via IFTTT
Donald Trump's Email Servers are Horribly Insecure — Researcher Reveals
from The Hacker News http://ift.tt/2ef0lwB
via IFTTT
Facebook is Going to make all your Private Photos Public Tomorrow — It's a Hoax!
from The Hacker News http://ift.tt/2dl8nFL
via IFTTT
Ravens (3-3) move down 4 spots to No. 18 in Week 7 NFL Power Rankings; visit Jets (1-5) on Sunday (ESPN)
via IFTTT
ISS Daily Summary Report – 10/17/2016
from ISS On-Orbit Status Report http://ift.tt/2e4AD1j
via IFTTT
ISS Daily Summary Report – 10/14/2016
from ISS On-Orbit Status Report http://ift.tt/2dYz0OV
via IFTTT
VeraCrypt Audit Reveals Critical Security Flaws — Update Now
from The Hacker News http://ift.tt/2edOyyB
via IFTTT
WikiLeaks Confirms Ecuador Cut Julian Assange's Internet Access After Clinton Leak
from The Hacker News http://ift.tt/2dx3g3R
via IFTTT