Latest YouTube Video
Saturday, February 18, 2017
AuthCache + Drupal Commerce integration + anonymous caching question
from Google Alert - anonymous http://ift.tt/2luK63g
via IFTTT
A Typo in Zerocoin's Source Code helped Hackers Steal ZCoins worth $585,000
from The Hacker News http://ift.tt/2l6TIAv
via IFTTT
Anonymous Leaks Gain New Prominence In Trump-Era Journalism
from Google Alert - anonymous http://ift.tt/2l6jzIR
via IFTTT
Google Discloses Windows Vulnerability That Microsoft Fails To Patch, Again!
from The Hacker News http://ift.tt/2kzzII5
via IFTTT
I have a new follower on Twitter
The Inspired Home
Creating moments to connect.
Chicago, IL
https://t.co/V1KA5V3GrK
Following: 24339 - Followers: 30081
February 18, 2017 at 11:12AM via Twitter http://twitter.com/ihainspiredhome
I have a new follower on Twitter
GlassWire
GlassWire's free firewall helps protect your device, privacy, and data usage by visualizing your network activity. https://t.co/aGDu9rafC2
Austin, TX USA
https://t.co/aGDu9rafC2
Following: 1735 - Followers: 2007
February 18, 2017 at 08:37AM via Twitter http://twitter.com/GlassWireLabs
Anonymous/House of LIGHTS
from Google Alert - anonymous http://ift.tt/2kzitGL
via IFTTT
I have a new follower on Twitter
Invest in Yourself
We are team of professionals that promotes #startups and general #crowdfunding #projects, by providing #SEO optimized advertisment and #traffic to our clients.
New York City
http://t.co/as4BeseoqU
Following: 10131 - Followers: 30233
February 18, 2017 at 05:32AM via Twitter http://twitter.com/investors_by
Friday, February 17, 2017
I have a new follower on Twitter
Happy to help 💡♨💦☎
FREE impartial advice and FREE quotes on all your business utilities. Please email. laura.cousins@switchedonbrokers.com
Wilmslow
Following: 364 - Followers: 479
February 17, 2017 at 07:42PM via Twitter http://twitter.com/ljcousins
Study: Anonymous web browsing doesn't mean you stay anonymous
from Google Alert - anonymous http://ift.tt/2ky8qBG
via IFTTT
Illinois utility plan allows access to anonymous energy usage data
from Google Alert - anonymous http://ift.tt/2l3eyAV
via IFTTT
Hackers Are Using Android Malware To Spy On Israeli Military Personnel
from The Hacker News http://ift.tt/2lrvdih
via IFTTT
ISS Daily Summary Report – 2/16/2017
from ISS On-Orbit Status Report http://ift.tt/2l11hbZ
via IFTTT
59 minutes ago
from Google Alert - anonymous http://ift.tt/2kFi54I
via IFTTT
This Ransomware Malware Could Poison Your Water Supply If Not Paid
from The Hacker News http://ift.tt/2kZBzER
via IFTTT
Thursday, February 16, 2017
[2.1,2.2] Anonymous auto-enlistment fails to contact metadata service
from Google Alert - anonymous http://ift.tt/2kvUPLm
via IFTTT
I have a new follower on Twitter
MarketScale
We help B2B brands market their products with the same level of precision and inspiration required to engineer them.
Dallas, TX
https://t.co/owXkuG3qAJ
Following: 1797 - Followers: 2238
February 16, 2017 at 09:43PM via Twitter http://twitter.com/MarketScale
Efficient Computation of Moments in Sum-Product Networks. (arXiv:1702.04767v1 [cs.LG])
Bayesian online learning algorithms for Sum-Product Networks (SPNs) need to compute moments of model parameters under the one-step update posterior distribution. The best existing method for computing such moments scales quadratically in the size of the SPN, although it scales linearly for trees. We propose a linear-time algorithm that works even when the SPN is a directed acyclic graph (DAG). We achieve this goal by reducing the moment computation problem into a joint inference problem in SPNs and by taking advantage of a special structure of the one-step update posterior distribution: it is a multilinear polynomial with exponentially many monomials, and we can evaluate moments by differentiating. The latter is known as the \emph{differential trick}. We apply the proposed algorithm to develop a linear time assumed density filter (ADF) for SPN parameter learning. As an additional contribution, we conduct extensive experiments comparing seven different online learning algorithms for SPNs on 20 benchmark datasets. The new linear-time ADF method consistently achieves low runtime due to the efficient linear-time algorithm for moment computation; however, we discover that two other methods (CCCP and SMA) typically perform better statistically, while a third (BMM) is comparable to ADF. Interestingly, CCCP can be viewed as implicitly using the same differentiation trick that we make explicit here. The fact that two of the top four fastest methods use this trick suggests that the same trick might find other uses for SPN learning in the future.
from cs.AI updates on arXiv.org http://ift.tt/2kY74io
via IFTTT
Theoretical and Practical Advances on Smoothing for Extensive-Form Games. (arXiv:1702.04849v1 [cs.GT])
Sparse iterative methods, in particular first-order methods, are known to be among the most effective in solving large-scale two-player zero-sum extensive-form games. The convergence rates of these methods depend heavily on the properties of the distance-generating function that they are based on. We investigate the acceleration of first-order methods for solving extensive-form games through better design of the dilated entropy function---a class of distance-generating functions related to the domains associated with the extensive-form games. By introducing a new weighting scheme for the dilated entropy function, we develop the first distance-generating function for the strategy spaces of sequential games that has no dependence on the branching factor of the player. This result improves the convergence rate of several first-order methods by a factor of $\Omega(b^dd)$, where $b$ is the branching factor of the player, and $d$ is the depth of the game tree.
Thus far, counterfactual regret minimization methods have been faster in practice, and more popular, than first-order methods despite their theoretically inferior convergence rates. Using our new weighting scheme and practical tuning we show that, for the first time, the excessive gap technique can be made faster than the fastest counterfactual regret minimization algorithm, CFR+, in practice.
from cs.AI updates on arXiv.org http://ift.tt/2kPq7Jl
via IFTTT
Reflexive Regular Equivalence for Bipartite Data. (arXiv:1702.04956v1 [cs.LG])
Bipartite data is common in data engineering and brings unique challenges, particularly when it comes to clustering tasks that impose on strong structural assumptions. This work presents an unsupervised method for assessing similarity in bipartite data. Similar to some co-clustering methods, the method is based on regular equivalence in graphs. The algorithm uses spectral properties of a bipartite adjacency matrix to estimate similarity in both dimensions. The method is reflexive in that similarity in one dimension is used to inform similarity in the other. Reflexive regular equivalence can also use the structure of transitivities -- in a network sense -- the contribution of which is controlled by the algorithm's only free-parameter, $\alpha$. The method is completely unsupervised and can be used to validate assumptions of co-similarity, which are required but often untested, in co-clustering analyses. Three variants of the method with different normalizations are tested on synthetic data. The method is found to be robust to noise and well-suited to asymmetric co-similar structure, making it particularly informative for cluster analysis and recommendation in bipartite data of unknown structure. In experiments, the convergence and speed of the algorithm are found to be stable for different levels of noise. Real-world data from a network of malaria genes are analyzed, where the similarity produced by the reflexive method is shown to out-perform other measures' ability to correctly classify genes.
from cs.AI updates on arXiv.org http://ift.tt/2kY8rOf
via IFTTT
Two Timescale Stochastic Approximation with Controlled Markov noise and Off-policy temporal difference learning. (arXiv:1503.09105v12 [math.DS] UPDATED)
We present for the first time an asymptotic convergence analysis of two time-scale stochastic approximation driven by `controlled' Markov noise. In particular, both the faster and slower recursions have non-additive controlled Markov noise components in addition to martingale difference noise. We analyze the asymptotic behavior of our framework by relating it to limiting differential inclusions in both time-scales that are defined in terms of the ergodic occupation measures associated with the controlled Markov processes. Finally, we present a solution to the off-policy convergence problem for temporal difference learning with linear function approximation, using our results.
from cs.AI updates on arXiv.org http://ift.tt/1EA6KLi
via IFTTT
Learning to Poke by Poking: Experiential Learning of Intuitive Physics. (arXiv:1606.07419v2 [cs.CV] UPDATED)
We investigate an experiential learning paradigm for acquiring an internal model of intuitive physics. Our model is evaluated on a real-world robotic manipulation task that requires displacing objects to target locations by poking. The robot gathered over 400 hours of experience by executing more than 100K pokes on different objects. We propose a novel approach based on deep neural networks for modeling the dynamics of robot's interactions directly from images, by jointly estimating forward and inverse models of dynamics. The inverse model objective provides supervision to construct informative visual features, which the forward model can then predict and in turn regularize the feature space for the inverse model. The interplay between these two objectives creates useful, accurate models that can then be used for multi-step decision making. This formulation has the additional benefit that it is possible to learn forward models in an abstract feature space and thus alleviate the need of predicting pixels. Our experiments show that this joint modeling approach outperforms alternative methods.
from cs.AI updates on arXiv.org http://ift.tt/291kNxf
via IFTTT
Grammatical Templates: Improving Text Difficulty Evaluation for Language Learners. (arXiv:1609.05180v2 [cs.CL] UPDATED)
Language students are most engaged while reading texts at an appropriate difficulty level. However, existing methods of evaluating text difficulty focus mainly on vocabulary and do not prioritize grammatical features, hence they do not work well for language learners with limited knowledge of grammar. In this paper, we introduce grammatical templates, the expert-identified units of grammar that students learn from class, as an important feature of text difficulty evaluation. Experimental classification results show that grammatical template features significantly improve text difficulty prediction accuracy over baseline readability features by 7.4%. Moreover, we build a simple and human-understandable text difficulty evaluation approach with 87.7% accuracy, using only 5 grammatical template features.
from cs.AI updates on arXiv.org http://ift.tt/2d0yz52
via IFTTT
Coupling Distributed and Symbolic Execution for Natural Language Queries. (arXiv:1612.02741v2 [cs.LG] UPDATED)
Building neural networks to query a knowledge base (a table) with natural language is an emerging research topic in NLP. The neural enquirer typically necessitates multiple steps of execution because of the compositionality of queries. In previous studies, researchers have developed either distributed enquirers or symbolic ones for table querying. The distributed enquirer is end-to-end learnable, but is weak in terms of execution efficiency and explicit interpretability. The symbolic enqurier, on the contrary, is efficient during execution; but it is very difficult to train especially at initial stages. In this paper, we propose to couple distributed and symbolic execution for natural language queries. The observation is that a fully distributed executor also exhibits meaningful, albeit imperfect, interpretation. We can thus pretrain the symbolic executor with the distributed one's intermediate execution results in a step-by-step fashion. Experiments show that our approach significantly outperforms either the distributed or symbolic executor; moreover, we have recovered more than 80% execution sequences with only groundtruth denotations during training. In summary, the coupled neural enquirer takes advantages of both distributed and symbolic executors, and has high performance, high learning efficiency, high execution efficiency, and high interpretability.
from cs.AI updates on arXiv.org http://ift.tt/2ggxMx4
via IFTTT
Orioles: RP Brad Brach asks for $3.05M in arbitration; team offers $2.5M (ESPN)
via IFTTT
Anonymous Posting as "A TripAdvisor member"?
from Google Alert - anonymous http://ift.tt/2lnuNd1
via IFTTT
Lottery winners could soon be anonymous
from Google Alert - anonymous http://ift.tt/2lXXwlf
via IFTTT
Anonymous Donor Leaves Free Treats At Bottom Of Vending Machine As
from Google Alert - anonymous http://ift.tt/2lmIEQB
via IFTTT
This anonymous Tiger
from Google Alert - anonymous http://ift.tt/2lmGdha
via IFTTT
Anonymous U football player: Fleck more proactive than Kill/Claeys in accountability
from Google Alert - anonymous http://ift.tt/2kNYnVq
via IFTTT
Chameleon in a Candy Store
from Google Alert - anonymous http://ift.tt/2locbsQ
via IFTTT
A Simple JavaScript Exploit Bypasses ASLR Protection On 22 CPU Architectures
from The Hacker News http://ift.tt/2lX7NOs
via IFTTT
[FD] Elefant CMS 1.3.12-RC: Code Execution
Source: Gmail -> IFTTT-> Blogger
[FD] Elefant CMS 1.3.12-RC: Code Execution
Source: Gmail -> IFTTT-> Blogger
[FD] Plone: XSS
Source: Gmail -> IFTTT-> Blogger
[FD] Elefant CMS 1.3.12-RC: CSRF
Source: Gmail -> IFTTT-> Blogger
[FD] Elefant CMS 1.3.12-RC: Multiple Persistent and Reflected XSS
Source: Gmail -> IFTTT-> Blogger
Five Moves: Pick up C.J. Mosley's option, re-sign Brandon Williams among Bill Barnwell's offseason priorities for Ravens (ESPN)
via IFTTT
Regarding Prospects Visit Anonymous Visitor Page U...
from Google Alert - anonymous http://ift.tt/2lOZsjY
via IFTTT
ISS Daily Summary Report – 2/15/2017
from ISS On-Orbit Status Report http://ift.tt/2lWgCIa
via IFTTT
News editors back anonymous sources bill
from Google Alert - anonymous http://ift.tt/2lVv8zV
via IFTTT
Yahoo Hacked Once Again! Quietly Warns Affected Users About New Attack
from The Hacker News http://ift.tt/2lV5kE2
via IFTTT
New MacOS Malware linked to Russian Hackers Can Steal Passwords & iPhone Backups
from The Hacker News http://ift.tt/2kVF7Ys
via IFTTT
The Calabash Nebula from Hubble

August 21, 2017 Total Solar Eclipse Path for Spherical Displays
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2ks3Sgr
via IFTTT
Wednesday, February 15, 2017
Community United for Safety and Protection: An anonymous experience relating to HB112
from Google Alert - anonymous http://ift.tt/2kMfirx
via IFTTT
(meme)- Quote from anonymous intelligence community member.
from Google Alert - anonymous http://ift.tt/2lMYk00
via IFTTT
Entropy Non-increasing Games for the Improvement of Dataflow Programming. (arXiv:1702.04389v1 [cs.AI])
In this article, we introduce a new conception of a family of esport games called Samu Entropy to try to improve dataflow program graphs like the ones that are based on Google's TensorFlow. Currently, the Samu Entropy project specifies only requirements for new esport games to be developed with particular attention to the investigation of the relationship between esport and artificial intelligence. It is quite obvious that there is a very close and natural relationship between esport games and artificial intelligence. Furthermore, the project Samu Entropy focuses not only on using artificial intelligence, but on creating AI in a new way. We present a reference game called Face Battle that implements the Samu Entropy requirements.
from cs.AI updates on arXiv.org http://ift.tt/2llw049
via IFTTT
Efficient Multi-task Feature and Relationship Learning. (arXiv:1702.04423v1 [cs.LG])
In this paper we propose a multi-convex framework for multi-task learning that improves predictions by learning relationships both between tasks and between features. Our framework is a generalization of related methods in multi-task learning, that either learn task relationships, or feature relationships, but not both. We start with a hierarchical Bayesian model, and use the empirical Bayes method to transform the underlying inference problem into a multi-convex optimization problem. We propose a coordinate-wise minimization algorithm that has a closed form solution for each block subproblem. Naively these solutions would be expensive to compute, but by using the theory of doubly stochastic matrices, we are able to reduce the underlying matrix optimization subproblem into a minimum weight perfect matching problem on a complete bipartite graph, and solve it analytically and efficiently. To solve the weight learning subproblem, we propose three different strategies, including a gradient descent method with linear convergence guarantee when the instances are not shared by multiple tasks, and a numerical solution based on Sylvester equation when instances are shared. We demonstrate the efficiency of our method on both synthetic datasets and real-world datasets. Experiments show that the proposed optimization method is orders of magnitude faster than an off-the-shelf projected gradient method, and our model is able to exploit the correlation structures among multiple tasks and features.
from cs.AI updates on arXiv.org http://ift.tt/2kA1oaO
via IFTTT
Frustratingly Short Attention Spans in Neural Language Modeling. (arXiv:1702.04521v1 [cs.CL])
Neural language models predict the next token using a latent representation of the immediate token history. Recently, various methods for augmenting neural language models with an attention mechanism over a differentiable memory have been proposed. For predicting the next token, these models query information from a memory of the recent history which can facilitate learning mid- and long-range dependencies. However, conventional attention mechanisms used in memory-augmented neural language models produce a single output vector per time step. This vector is used both for predicting the next token as well as for the key and value of a differentiable memory of a token history. In this paper, we propose a neural language model with a key-value attention mechanism that outputs separate representations for the key and value of a differentiable memory, as well as for encoding the next-word distribution. This model outperforms existing memory-augmented neural language models on two corpora. Yet, we found that our method mainly utilizes a memory of the five most recent output representations. This led to the unexpected main finding that a much simpler model based only on the concatenation of recent output representations from previous time steps is on par with more sophisticated memory-augmented neural language models.
from cs.AI updates on arXiv.org http://ift.tt/2lluUVO
via IFTTT
On the Discrepancy Between Kleinberg's Clustering Axioms and $k$-Means Clustering Algorithm Behavior. (arXiv:1702.04577v1 [cs.LG])
This paper investigates the validity of Kleinberg's axioms for clustering functions with respect to the quite popular clustering algorithm called $k$-means. While Kleinberg's axioms have been discussed heavily in the past, we concentrate here on the case predominantly relevant for $k$-means algorithm, that is behavior embedded in Euclidean space. We point at some contradictions and counter intuitiveness aspects of this axiomatic set within $\mathbb{R}^m$ that were evidently not discussed so far. Our results suggest that apparently without defining clearly what kind of clusters we expect we will not be able to construct a valid axiomatic system. In particular we look at the shape and the gaps between the clusters. Finally we demonstrate that there exist several ways to reconcile the formulation of the axioms with their intended meaning and that under this reformulation the axioms stop to be contradictory and the real-world $k$-means algorithm conforms to this axiomatic system.
from cs.AI updates on arXiv.org http://ift.tt/2kzYkeY
via IFTTT
Developing an ontology for the access to the contents of an archival fonds: the case of the Catasto Gregoriano. (arXiv:1702.04584v1 [cs.AI])
The research was proposed to exploit and extend the relational and contextual nature of the information assets of the Catasto Gregoriano, kept at the Archivio di Stato in Rome. Developed within the MODEUS project (Making Open Data Effectively Usable), this study originates from the following key ideas of MODEUS: to require Open Data to be expressed in terms of an ontology, and to include such an ontology as a documentation of the data themselves. Thus, Open Data are naturally linked by means of the ontology, which meets the requirements of the Linked Open Data vision.
from cs.AI updates on arXiv.org http://ift.tt/2llsEOw
via IFTTT
Local Search for Minimum Weight Dominating Set with Two-Level Configuration Checking and Frequency Based Scoring Function. (arXiv:1702.04594v1 [cs.AI])
The Minimum Weight Dominating Set (MWDS) problem is an important generalization of the Minimum Dominating Set (MDS) problem with extensive applications. This paper proposes a new local search algorithm for the MWDS problem, which is based on two new ideas. The first idea is a heuristic called two-level configuration checking (CC2), which is a new variant of a recent powerful configuration checking strategy (CC) for effectively avoiding the recent search paths. The second idea is a novel scoring function based on the frequency of being uncovered of vertices. Our algorithm is called CC2FS, according to the names of the two ideas. The experimental results show that, CC2FS performs much better than some state-of-the-art algorithms in terms of solution quality on a broad range of MWDS benchmarks.
from cs.AI updates on arXiv.org http://ift.tt/2kA48F3
via IFTTT
Visualizing Deep Neural Network Decisions: Prediction Difference Analysis. (arXiv:1702.04595v1 [cs.CV])
This article presents the prediction difference analysis method for visualizing the response of a deep neural network to a specific input. When classifying images, the method highlights areas in a given input image that provide evidence for or against a certain class. It overcomes several shortcoming of previous methods and provides great additional insight into the decision making process of classifiers. Making neural network decisions interpretable through visualization is important both to improve models and to accelerate the adoption of black-box classifiers in application areas such as medicine. We illustrate the method in experiments on natural images (ImageNet data), as well as medical images (MRI brain scans).
from cs.AI updates on arXiv.org http://ift.tt/2lMWiNq
via IFTTT
A Spacetime Approach to Generalized Cognitive Reasoning in Multi-scale Learning. (arXiv:1702.04638v1 [cs.AI])
In modern machine learning, pattern recognition replaces realtime semantic reasoning. The mapping from input to output is learned with fixed semantics by training outcomes deliberately. This is an expensive and static approach which depends heavily on the availability of a very particular kind of prior raining data to make inferences in a single step. Conventional semantic network approaches, on the other hand, base multi-step reasoning on modal logics and handcrafted ontologies, which are {\em ad hoc}, expensive to construct, and fragile to inconsistency. Both approaches may be enhanced by a hybrid approach, which completely separates reasoning from pattern recognition. In this report, a quasi-linguistic approach to knowledge representation is discussed, motivated by spacetime structure. Tokenized patterns from diverse sources are integrated to build a lightly constrained and approximately scale-free network. This is then be parsed with very simple recursive algorithms to generate `brainstorming' sets of reasoned knowledge.
from cs.AI updates on arXiv.org http://ift.tt/2llBlbw
via IFTTT
Telugu OCR Framework using Deep Learning. (arXiv:1509.05962v2 [stat.ML] UPDATED)
In this paper, we address the task of Optical Character Recognition(OCR) for the Telugu script. We present an end-to-end framework that segments the text image, classifies the characters and extracts lines using a language model. The segmentation is based on mathematical morphology. The classification module, which is the most challenging task of the three, is a deep convolutional neural network. The language is modelled as a third degree markov chain at the glyph level. Telugu script is a complex alphasyllabary and the language is agglutinative, making the problem hard. In this paper we apply the latest advances in neural networks to achieve state-of-the-art error rates. We also review convolutional neural networks in great detail and expound the statistical justification behind the many tricks needed to make Deep Learning work.
from cs.AI updates on arXiv.org http://ift.tt/1KIvpiF
via IFTTT
Optimal Number of Choices in Rating Contexts. (arXiv:1605.06588v5 [cs.AI] UPDATED)
In many settings people must give numerical scores to entities from a small discrete set. For instance, rating physical attractiveness from 1-5 on dating sites, or papers from 1-10 for conference reviewing. We study the problem of understanding when using a different number of options is optimal. For concreteness we assume the true underlying scores are integers from 1-100. We consider the case when scores are uniform random and Gaussian. We study when using 2, 3, 4, 5, and 10 options is optimal in these models. One may expect that using more options would always improve performance in this model, but we show that this is not necessarily the case, and that using fewer choices -- even just two -- can surprisingly be optimal in certain situations. While in theory for this setting it would be optimal to use all 100 options, in practice this is prohibitive, and it is preferable to utilize a smaller number of options due to humans' limited computational resources. Our results suggest that using a smaller number of options than is typical could be optimal in certain situations. This would have many potential applications, as settings requiring entities to be ranked by humans are ubiquitous.
from cs.AI updates on arXiv.org http://ift.tt/1Ua9moh
via IFTTT
Neural Architecture Search with Reinforcement Learning. (arXiv:1611.01578v2 [cs.LG] UPDATED)
Neural networks are powerful and flexible models that work well for many difficult learning tasks in image, speech and natural language understanding. Despite their success, neural networks are still hard to design. In this paper, we use a recurrent network to generate the model descriptions of neural networks and train this RNN with reinforcement learning to maximize the expected accuracy of the generated architectures on a validation set. On the CIFAR-10 dataset, our method, starting from scratch, can design a novel network architecture that rivals the best human-invented architecture in terms of test set accuracy. Our CIFAR-10 model achieves a test error rate of 3.65, which is 0.09 percent better and 1.05x faster than the previous state-of-the-art model that used a similar architectural scheme. On the Penn Treebank dataset, our model can compose a novel recurrent cell that outperforms the widely-used LSTM cell, and other state-of-the-art baselines. Our cell achieves a test set perplexity of 62.4 on the Penn Treebank, which is 3.6 perplexity better than the previous state-of-the-art model. The cell can also be transferred to the character language modeling task on PTB and achieves a state-of-the-art perplexity of 1.214.
from cs.AI updates on arXiv.org http://ift.tt/2eGYtO2
via IFTTT
Learning to Act by Predicting the Future. (arXiv:1611.01779v2 [cs.LG] UPDATED)
We present an approach to sensorimotor control in immersive environments. Our approach utilizes a high-dimensional sensory stream and a lower-dimensional measurement stream. The cotemporal structure of these streams provides a rich supervisory signal, which enables training a sensorimotor control model by interacting with the environment. The model is trained using supervised learning techniques, but without extraneous supervision. It learns to act based on raw sensory input from a complex three-dimensional environment. The presented formulation enables learning without a fixed goal at training time, and pursuing dynamically changing goals at test time. We conduct extensive experiments in three-dimensional simulations based on the classical first-person game Doom. The results demonstrate that the presented approach outperforms sophisticated prior formulations, particularly on challenging tasks. The results also show that trained models successfully generalize across environments and goals. A model trained using the presented approach won the Full Deathmatch track of the Visual Doom AI Competition, which was held in previously unseen environments.
from cs.AI updates on arXiv.org http://ift.tt/2fzg5c7
via IFTTT
Anonymous Alerts® and PNW BOCES Partner to Eliminate Bullying, Drugs, and Safety Issues in All ...
from Google Alert - anonymous http://ift.tt/2kzH3Ct
via IFTTT
Sister Anonymous
from Google Alert - anonymous http://ift.tt/2l973qi
via IFTTT
Sandusky Register Star News
from Google Alert - anonymous http://ift.tt/2kqeHzu
via IFTTT
ISS Daily Summary Report – 2/14/2017
from ISS On-Orbit Status Report http://ift.tt/2kSs0ra
via IFTTT
I have a new follower on Twitter
Clearlease Funding
Visit https://t.co/P3qDBpCQIg today get your campaign promoted on Facebook 520,000+ & Twitter to 1,840,000+ Donors, Investors, & Angels
GLOBAL
https://t.co/P3qDBpCQIg
Following: 88082 - Followers: 85324
February 15, 2017 at 07:03AM via Twitter http://twitter.com/Clearlease
Websites Can Now Track You Online Across Multiple Web Browsers
from The Hacker News http://ift.tt/2kp60Wh
via IFTTT
Signal Messaging App Rolls Out Encrypted Video Calling
from The Hacker News http://ift.tt/2koM3Pf
via IFTTT
[FD] Backdoored Web Application v.1.0.2
Source: Gmail -> IFTTT-> Blogger
[FD] ShadeYouVPN.com Client v2.0.1.11 for Windows Privilege Escalation
Source: Gmail -> IFTTT-> Blogger
The Rosette Nebula
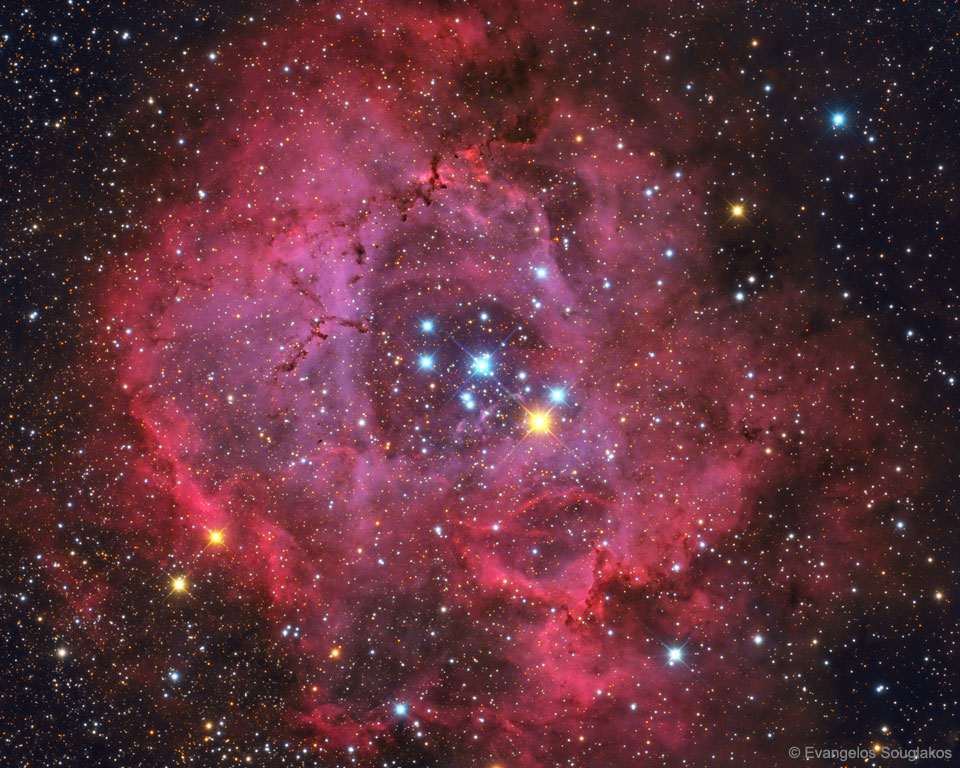
Tuesday, February 14, 2017
I have a new follower on Twitter
James Maguire
Tech journalist, managing editor, https://t.co/oemYsgw8XQ - Cloud, Big Data, AI, VR, startups. Omnivorous culture hound. Tweets my own 'til the robots rebel.
SF Bay Area
http://t.co/LvTiSUR3zu
Following: 5767 - Followers: 8616
February 14, 2017 at 10:43PM via Twitter http://twitter.com/JamesMaguire
Data-Intensive Supercomputing in the Cloud: Global Analytics for Satellite Imagery. (arXiv:1702.03935v1 [cs.DC])
We present our experiences using cloud computing to support data-intensive analytics on satellite imagery for commercial applications. Drawing from our background in high-performance computing, we draw parallels between the early days of clustered computing systems and the current state of cloud computing and its potential to disrupt the HPC market. Using our own virtual file system layer on top of cloud remote object storage, we demonstrate aggregate read bandwidth of 230 gigabytes per second using 512 Google Compute Engine (GCE) nodes accessing a USA multi-region standard storage bucket. This figure is comparable to the best HPC storage systems in existence. We also present several of our application results, including the identification of field boundaries in Ukraine, and the generation of a global cloud-free base layer from Landsat imagery.
from cs.AI updates on arXiv.org http://ift.tt/2leWKne
via IFTTT
Constraint Answer Set Solver EZCSP and Why Integration Schemas Matter. (arXiv:1702.04047v1 [cs.AI])
Researchers in answer set programming and constraint programming have spent significant efforts in the development of hybrid languages and solving algorithms combining the strengths of these traditionally separate fields. These efforts resulted in a new research area: constraint answer set programming. Constraint answer set programming languages and systems proved to be successful at providing declarative, yet efficient solutions to problems involving hybrid reasoning tasks. One of the main contributions of this paper is the first comprehensive account of the constraint answer set language and solver EZCSP, a mainstream representative of this research area that has been used in various successful applications. We also develop an extension of the transition systems proposed by Nieuwenhuis et al. in 2006 to capture Boolean satisfiability solvers. We use this extension to describe the EZCSP algorithm and prove formal claims about it. The design and algorithmic details behind EZCSP clearly demonstrate that the development of the hybrid systems of this kind is challenging. Many questions arise when one faces various design choices in an attempt to maximize system's benefits. One of the key decisions that a developer of a hybrid solver makes is settling on a particular integration schema within its implementation. Thus, another important contribution of this paper is a thorough case study based on EZCSP, focused on the various integration schemas that it provides.
Under consideration in Theory and Practice of Logic Programming (TPLP).
from cs.AI updates on arXiv.org http://ift.tt/2lhIglR
via IFTTT
Crossmatching variable objects with the Gaia data. (arXiv:1702.04165v1 [astro-ph.IM])
Tens of millions of new variable objects are expected to be identified in over a billion time series from the Gaia mission. Crossmatching known variable sources with those from Gaia is crucial to incorporate current knowledge, understand how these objects appear in the Gaia data, train supervised classifiers to recognise known classes, and validate the results of the Variability Processing and Analysis Coordination Unit (CU7) within the Gaia Data Analysis and Processing Consortium (DPAC). The method employed by CU7 to crossmatch variables for the first Gaia data release includes a binary classifier to take into account positional uncertainties, proper motion, targeted variability signals, and artefacts present in the early calibration of the Gaia data. Crossmatching with a classifier makes it possible to automate all those decisions which are typically made during visual inspection. The classifier can be trained with objects characterized by a variety of attributes to ensure similarity in multiple dimensions (astrometry, photometry, time-series features), with no need for a-priori transformations to compare different photometric bands, or of predictive models of the motion of objects to compare positions. Other advantages as well as some disadvantages of the method are discussed. Implementation steps from the training to the assessment of the crossmatch classifier and selection of results are described.
from cs.AI updates on arXiv.org http://ift.tt/2kvkleF
via IFTTT
On Detecting Adversarial Perturbations. (arXiv:1702.04267v1 [stat.ML])
Machine learning and deep learning in particular has advanced tremendously on perceptual tasks in recent years. However, it remains vulnerable against adversarial perturbations of the input that have been crafted specifically to fool the system while being quasi-imperceptible to a human. In this work, we propose to augment deep neural networks with a small "detector" subnetwork which is trained on the binary classification task of distinguishing genuine data from data containing adversarial perturbations. Our method is orthogonal to prior work on addressing adversarial perturbations, which has mostly focused on making the classification network itself more robust. We show empirically that adversarial perturbations can be detected surprisingly well even though they are quasi-imperceptible to humans. Moreover, while the detectors have been trained to detect only a specific adversary, they generalize to similar and weaker adversaries. In addition, we propose an adversarial attack that fools both the classifier and the detector and a novel training procedure for the detector that counteracts this attack.
from cs.AI updates on arXiv.org http://ift.tt/2lhwVCx
via IFTTT
DAGER: Deep Age, Gender and Emotion Recognition Using Convolutional Neural Network. (arXiv:1702.04280v1 [cs.CV])
This paper describes the details of Sighthound's fully automated age, gender and emotion recognition system. The backbone of our system consists of several deep convolutional neural networks that are not only computationally inexpensive, but also provide state-of-the-art results on several competitive benchmarks. To power our novel deep networks, we collected large labeled datasets through a semi-supervised pipeline to reduce the annotation effort/time. We tested our system on several public benchmarks and report outstanding results. Our age, gender and emotion recognition models are available to developers through the Sighthound Cloud API at http://ift.tt/1MlcpaD
from cs.AI updates on arXiv.org http://ift.tt/2kvjRWh
via IFTTT
T-SKIRT: Online Estimation of Student Proficiency in an Adaptive Learning System. (arXiv:1702.04282v1 [cs.AI])
We develop T-SKIRT: a temporal, structured-knowledge, IRT-based method for predicting student responses online. By explicitly accounting for student learning and employing a structured, multidimensional representation of student proficiencies, the model outperforms standard IRT-based methods on an online response prediction task when applied to real responses collected from students interacting with diverse pools of educational content.
from cs.AI updates on arXiv.org http://ift.tt/2kveupR
via IFTTT
Bayesian Opponent Exploitation in Imperfect-Information Games. (arXiv:1603.03491v4 [cs.GT] UPDATED)
Two fundamental problems in computational game theory are computing a Nash equilibrium and learning to exploit opponents given observations of their play (opponent exploitation). The latter is perhaps even more important than the former: Nash equilibrium does not have a compelling theoretical justification in game classes other than two-player zero-sum, and for all games one can potentially do better by exploiting perceived weaknesses of the opponent than by following a static equilibrium strategy throughout the match. The natural setting for opponent exploitation is the Bayesian setting where we have a prior model that is integrated with observations to create a posterior opponent model that we respond to. The most natural, and a well-studied prior distribution is the Dirichlet distribution. An exact polynomial-time algorithm is known for best-responding to the posterior distribution for an opponent assuming a Dirichlet prior with multinomial sampling in normal-form games; however, for imperfect-information games the best known algorithm is based on approximating an infinite integral without theoretical guarantees. We present the first exact algorithm for a natural class of imperfect-information games. We demonstrate that our algorithm runs quickly in practice and outperforms the best prior approaches. We also present an algorithm for the uniform prior setting.
from cs.AI updates on arXiv.org http://ift.tt/22ee9sx
via IFTTT
Hadamard Product for Low-rank Bilinear Pooling. (arXiv:1610.04325v3 [cs.CV] UPDATED)
Bilinear models provide rich representations compared with linear models. They have been applied in various visual tasks, such as object recognition, segmentation, and visual question-answering, to get state-of-the-art performances taking advantage of the expanded representations. However, bilinear representations tend to be high-dimensional, limiting the applicability to computationally complex tasks. We propose low-rank bilinear pooling using Hadamard product for an efficient attention mechanism of multimodal learning. We show that our model outperforms compact bilinear pooling in visual question-answering tasks with the state-of-the-art results on the VQA dataset, having a better parsimonious property.
from cs.AI updates on arXiv.org http://ift.tt/2ed1inE
via IFTTT
Dynamic Coattention Networks For Question Answering. (arXiv:1611.01604v3 [cs.CL] UPDATED)
Several deep learning models have been proposed for question answering. However, due to their single-pass nature, they have no way to recover from local maxima corresponding to incorrect answers. To address this problem, we introduce the Dynamic Coattention Network (DCN) for question answering. The DCN first fuses co-dependent representations of the question and the document in order to focus on relevant parts of both. Then a dynamic pointing decoder iterates over potential answer spans. This iterative procedure enables the model to recover from initial local maxima corresponding to incorrect answers. On the Stanford question answering dataset, a single DCN model improves the previous state of the art from 71.0% F1 to 75.9%, while a DCN ensemble obtains 80.4% F1.
from cs.AI updates on arXiv.org http://ift.tt/2exT6xr
via IFTTT
Cutting-off Redundant Repeating Generations for Neural Abstractive Summarization. (arXiv:1701.00138v2 [cs.CL] UPDATED)
This paper tackles the reduction of redundant repeating generation that is often observed in RNN-based encoder-decoder models. Our basic idea is to jointly estimate the upper-bound frequency of each target vocabulary in the encoder and control the output words based on the estimation in the decoder. Our method shows significant improvement over a strong RNN-based encoder-decoder baseline and achieved its best results on an abstractive summarization benchmark.
from cs.AI updates on arXiv.org http://ift.tt/2iJg8Vk
via IFTTT
Click Through Rate Prediction for Contextual Advertisment Using Linear Regression. (arXiv:1701.08744v1 [cs.IR] CROSS LISTED)
This research presents an innovative and unique way of solving the advertisement prediction problem which is considered as a learning problem over the past several years. Online advertising is a multi-billion-dollar industry and is growing every year with a rapid pace. The goal of this research is to enhance click through rate of the contextual advertisements using Linear Regression. In order to address this problem, a new technique propose in this paper to predict the CTR which will increase the overall revenue of the system by serving the advertisements more suitable to the viewers with the help of feature extraction and displaying the advertisements based on context of the publishers. The important steps include the data collection, feature extraction, CTR prediction and advertisement serving. The statistical results obtained from the dynamically used technique show an efficient outcome by fitting the data close to perfection for the LR technique using optimized feature selection.
from cs.AI updates on arXiv.org http://ift.tt/2jNkuNH
via IFTTT
Must visit
from Google Alert - anonymous http://ift.tt/2lIrsFW
via IFTTT
Feeld — Anonymous Invite
from Google Alert - anonymous http://ift.tt/2lHZZEp
via IFTTT
Orioles' Chris Tillman likely to start season on DL after PRP injection in shoulder; team-best 16 wins in 2016 (ESPN)
via IFTTT
Anonymous user 517a69
from Google Alert - anonymous http://ift.tt/2lMGEP7
via IFTTT
Ravens: Unrestricted free-agent NT Brandon Williams says future with team is "up in the air" - Sirius XM NFL Radio (ESPN)
via IFTTT
I have a new follower on Twitter
Eric S Burdon
Youtube host of Eric Burdon TV, Blogger, Life Coach. My goal is to help YOU! You can also support me on patreon: https://t.co/IM0PkBGiyv
https://t.co/WhcDXvBRBv
Following: 5954 - Followers: 11969
February 14, 2017 at 12:08PM via Twitter http://twitter.com/es_burdon
Anonymous notes show support for Pueblo police
from Google Alert - anonymous http://ift.tt/2l4HkPN
via IFTTT
ISS Daily Summary Report – 2/13/2017
from ISS On-Orbit Status Report http://ift.tt/2ksZNUe
via IFTTT
ISS Daily Summary Report – 2/10/2017
from ISS On-Orbit Status Report http://ift.tt/2lcCGBP
via IFTTT