Latest YouTube Video
Saturday, June 3, 2017
Food Addicts in Recovery Anonymous (Concord)
from Google Alert - anonymous http://ift.tt/2qLWYli
via IFTTT
Français (France)
from Google Alert - anonymous http://ift.tt/2s56pQs
via IFTTT
The Steele Of Approval To An Anonymous Guy Who Helped Some Hockey Fans Get Stanley Cup ...
from Google Alert - anonymous http://ift.tt/2qLzxZk
via IFTTT
I have a new follower on Twitter
Eugene Tbone
are you living your dream?
Toledo, Ohio
Following: 4153 - Followers: 255
June 03, 2017 at 12:08PM via Twitter http://twitter.com/profeplligelma
Ravens are perfect landing spot for Jeremy Maclin, but team ranks among bottom five in salary-cap space - Jamison Hensley (ESPN)
via IFTTT
9 comments
from Google Alert - anonymous http://ift.tt/2qRtCB9
via IFTTT
Insecure Hadoop Clusters Exposed Over 5,000 Terabytes of Data
from The Hacker News http://ift.tt/2s3QFNA
via IFTTT
I have a new follower on Twitter
Logan Weeks
you can chat with me http://https://t.co/XkWxliq7Mg
Following: 461 - Followers: 7
June 03, 2017 at 04:43AM via Twitter http://twitter.com/LoganWeeks12
Perijove Passage
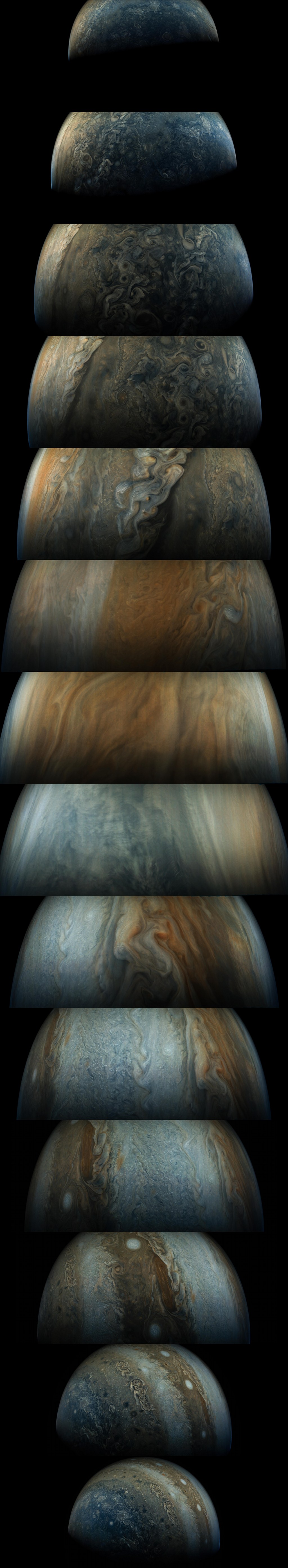
Friday, June 2, 2017
Orioles Video: Manny Machado jumps on Rick Porcello's 3-1 pitch and rockets solo homer into upper deck in 3-2 win over Red Sox (ESPN)
via IFTTT
Anonymous Donors Pay Off Loan For 7hills Day Center
from Google Alert - anonymous http://ift.tt/2qJS9bT
via IFTTT
Flix Anonymous - Episode 28
from Google Alert - anonymous http://ift.tt/2qJPfE8
via IFTTT
NFL: Ravens TE Dennis Pitta dislocated hip during Friday's OTA - Adam Schefter; 3rd time in 4 years he suffers same injury (ESPN)
via IFTTT
Anonymous Group Pays Balloon Payment to Keep 7Hills' Day Center Open
from Google Alert - anonymous http://ift.tt/2qKJYQF
via IFTTT
After Bomb Threats, FCC Proposes Letting Police Unveil Anonymous Callers
from Google Alert - anonymous http://ift.tt/2snnTVO
via IFTTT
Ravens: Dennis Pitta re-injures hip at Friday's OTA; led team with career-high 86 receptions last season (ESPN)
via IFTTT
WannaCry Coding Mistakes Can Help Files Recovery Even After Infection
from The Hacker News http://ift.tt/2rNvDTS
via IFTTT
Anonymous Faceless Woman Vector
from Google Alert - anonymous http://ift.tt/2s1q2sO
via IFTTT
ISS Daily Summary Report – 6/01/2017
from ISS On-Orbit Status Report http://ift.tt/2rjeRdK
via IFTTT
CIA Implants This Windows Hacking Tool to Silently Hack Computers Over Network
from The Hacker News http://ift.tt/2qIx063
via IFTTT
[FD] Qualys Security Advisory - CVE-2017-1000367 in Sudo's get_process_ttyname() for Linux
Source: Gmail -> IFTTT-> Blogger
[FD] DefenseCode ThunderScan SAST Advisory: WordPress No External Links Plugin Security Vulnerability
Source: Gmail -> IFTTT-> Blogger
[FD] DefenseCode ThunderScan SAST Advisory: WordPress Simple Slideshow Manager Plugin Multiple Security Vulnerabilities
Source: Gmail -> IFTTT-> Blogger
[FD] DefenseCode WebScanner DAST Advisory: WordPress Tribulant Newsletters Plugin Multiple Security Vulnerabilities
Source: Gmail -> IFTTT-> Blogger
Black Holes of Known Mass
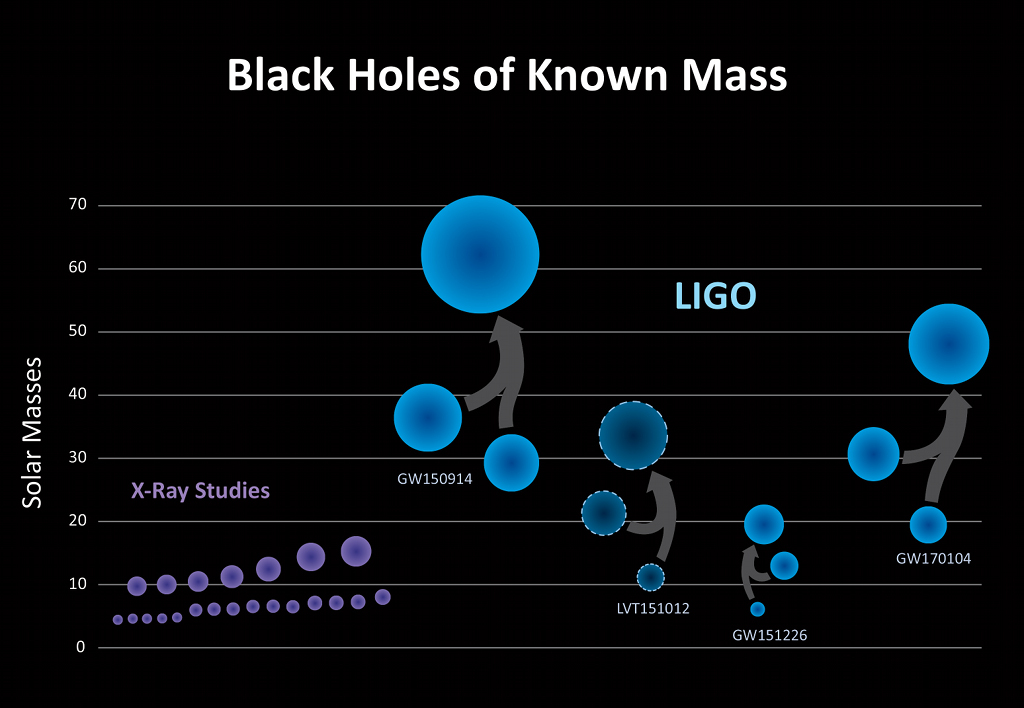
Thursday, June 1, 2017
Orioles Video: Chris Davis smacks solo home run deep to center during 7-5 win over Red Sox (ESPN)
via IFTTT
This Just In: CB Tavon Young suffered torn ACL during Thursday's practice and will miss 2017 season - Jamison Hensley (ESPN)
via IFTTT
OneLogin Password Manager Hacked; Users’ Data Can be Decrypted
from The Hacker News http://ift.tt/2rvoxCx
via IFTTT
I have a new follower on Twitter
Jesse Randall
Deviant strategist. Fundraising, financial modeling, B2B sales, content strategy. Live and die for start-ups. Constantly training for the next Ironman.
Phoenix, Arizona
https://t.co/K7tkaKMbGd
Following: 12003 - Followers: 12903
June 01, 2017 at 03:22PM via Twitter http://twitter.com/deviantstrat
Orioles: Manny Machado is scuffling like he has never scuffled before; Eddie Matz examines what's troubling the 3-time All-Star (ESPN)
via IFTTT
Ravens: CB Tavon Young helped off field after injuring leg midway through Thursday's practice; extent of injury still unknown (ESPN)
via IFTTT
Putin: Hackers Are Like Artists, Who Wake Up In A Good Mood & Start Painting
from The Hacker News http://ift.tt/2rptwT3
via IFTTT
Ravens: Football Power Index predicts 9-7 record for 2017 season, 48.6 percent chance to make playoffs (ESPN)
via IFTTT
Beware! Nearly 250 Million Computers Infected with Fireball Malware
from The Hacker News http://ift.tt/2qG0DFc
via IFTTT
ISS Daily Summary Report – 5/31/2017
from ISS On-Orbit Status Report http://ift.tt/2srOobE
via IFTTT
Online Training for CISA, CISM, and CISSP Cyber Security Certifications
from The Hacker News http://ift.tt/2qES9hy
via IFTTT
High-Severity Linux Sudo Flaw Allows Users to Gain Root Privileges
from The Hacker News http://ift.tt/2qIHopK
via IFTTT
Annual Arctic Sea Ice Minimum 1979-2016 with Area Graph
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2rrI3jb
via IFTTT
Temperature, Reflectance Point to Frost near the Moon's Poles
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2sppRnQ
via IFTTT
Image of the Arctic Sea ice - September 10, 2016
from NASA's Scientific Visualization Studio: Most Recent Items http://ift.tt/2rrBtZX
via IFTTT
Wednesday, May 31, 2017
Commercial PV Designer III
from Google Alert - anonymous http://ift.tt/2rGZai4
via IFTTT
Orioles Video: Adam Jones returns from injury with three-run homer to center in 10-4 victory over Yankees (ESPN)
via IFTTT
Why Anonymous Sources Matter
from Google Alert - anonymous http://ift.tt/2qHoEH8
via IFTTT
Anonymous Cav Says JaVale McGee Not Smart Enough To Play In NBA Finals
from Google Alert - anonymous http://ift.tt/2rd3lAR
via IFTTT
Workbench JavaScript Formula Fields Results - Now What?
from Google Alert - anonymous http://ift.tt/2rlLmpZ
via IFTTT
Orioles: Robert Andino suspended 50 games under baseball's minor league drug program following positive test for Amphetamine (ESPN)
via IFTTT
I have a new follower on Twitter
Will Botz
and I swear I hate you when you leave.
Scottsdale, Arizona
Following: 4190 - Followers: 123
May 31, 2017 at 06:25PM via Twitter http://twitter.com/seredrapepot
Orioles: Adam Jones (ankle, hip) in starting lineup Wednesday vs. Yankees after missing last four games (ESPN)
via IFTTT
Orioles: Welington Castillo may end up on DL after being hit in groin by foul ball Tuesday, says Buck Showalter (ESPN)
via IFTTT
Orioles: Manny Machado leads AL 3B in first All-Star ballot update; Welington Castillo 2nd at C (ESPN)
via IFTTT
Food Addicts in Recovery Anonymous (FA) - Tonight in Hanover
from Google Alert - anonymous http://ift.tt/2rl2NXM
via IFTTT
US Defense Contractor left Sensitive Files on Amazon Server Without Password
from The Hacker News http://ift.tt/2qGLaQb
via IFTTT
Ravens: John Harbaugh lauds early work of new S Tony Jefferson; "My impressions would be A-plus in every area" (ESPN)
via IFTTT
Anonymous user 414b5f
from Google Alert - anonymous http://ift.tt/2qBikSj
via IFTTT
ISS Daily Summary Report – 5/30/2017
from ISS On-Orbit Status Report http://ift.tt/2qAXSki
via IFTTT
Summary: Go Down, Moses by Anonymous [PDF for iPad]
from Google Alert - anonymous http://ift.tt/2rjnHqb
via IFTTT
LinkedIn Hacker, Wanted by US & Russian, Can be Extradited to Either State
from The Hacker News http://ift.tt/2rjihLX
via IFTTT
Tuesday, May 30, 2017
UVA Police investigate anonymous bomb threats across the Grounds.
from Google Alert - anonymous http://ift.tt/2skjaDv
via IFTTT
Summary and review: The Seafarer by Anonymous [PDF for iPad]
from Google Alert - anonymous http://ift.tt/2sjUkU9
via IFTTT
Romantics Anonymous
from Google Alert - anonymous http://ift.tt/2rlXkSN
via IFTTT
Orioles: Adam Jones (ankle, hip) back in lineup Tuesday vs. Yankees; sat out last three games (ESPN)
via IFTTT
I have a new follower on Twitter
Victoria Harmon
if you want to my naked photos her https://t.co/OrUr7jtY76
Following: 0 - Followers: 1
May 30, 2017 at 02:00PM via Twitter http://twitter.com/Victori09691048
Publish as an anonymous author or using
from Google Alert - anonymous http://ift.tt/2s9Z2nZ
via IFTTT
Quarter Million Dollar Anonymous by Trappin Anonymous
from Google Alert - anonymous http://ift.tt/2rAz0NX
via IFTTT
Chrome Flaw Allows Sites to Secretly Record Audio/Video Without Indication
from The Hacker News http://ift.tt/2shpA6k
via IFTTT
ISS Daily Summary Report – 5/29/2017
from ISS On-Orbit Status Report http://ift.tt/2rfnmF9
via IFTTT
ISS Daily Summary Report – 5/26/2017
from ISS On-Orbit Status Report http://ift.tt/2rQMepu
via IFTTT
Blog.yogisanonymous.com
from Google Alert - anonymous http://ift.tt/2rfh8oy
via IFTTT
Shadow Brokers Launches 0-Day Exploit Subscriptions for $21,000 Per Month
from The Hacker News http://ift.tt/2qugwhH
via IFTTT
[FD] Hacktivity 2017 Call For Papers
Source: Gmail -> IFTTT-> Blogger
A Kalahari Sky

Monday, May 29, 2017
Food Addicts in Recovery Anonymous (FA)
from Google Alert - anonymous http://ift.tt/2ryEqsF
via IFTTT
Bring visual novel Anonymous;Code to the West in English
from Google Alert - anonymous http://ift.tt/2seX6tY
via IFTTT
Orioles Video: Jonathan Schoop rips 2-run double the opposite way in 3rd inning against Yankees (ESPN)
via IFTTT
Linguistic Analysis Suggests WannaCry Hackers Could be From Southern China
from The Hacker News http://ift.tt/2s7qgMd
via IFTTT
Judy Android Malware Infects Over 36.5 Million Google Play Store Users
from The Hacker News http://ift.tt/2qrYWuZ
via IFTTT
Montages with OpenCV
Today’s blog post is inspired by an email I received from PyImageSearch reader, Brian.
Brian asks:
Hi Adrian,
I’m really enjoying the PyImageSearch blog. I found your site a few days ago and I’ve been hooked on your tutorials ever since.
I followed your tutorial on building an image search engine, but instead of displaying the result images one-by-one (like you did), I want to display the top-20 results in a montage.
Is there a way to do with OpenCV?
Thanks,
Brian
Great question Brian, thanks for asking.
One of my favorite aspects of running the PyImageSearch blog is being able to chat with you, the reader, and discover the projects you’re working on.
It’s especially exciting when I can take questions or comments and turn them into blog posts — that way the entire PyImageSearch community is able to benefit from the answer.
Today we will learn how to build montages of images using OpenCV and the imutils package. A big thank you to Kyle Hounslow who contributed the
build_montagesfunction to imutils.
To learn more about building an image montage with OpenCV, just keep reading.
Looking for the source code to this post?
Jump right to the downloads section.
Montages with OpenCV
There are four primary pieces to today’s blog post.
In the first part, we’ll learn how to build a list of image paths from an image dataset residing on disk.
From there, we’ll use the
build_montagesfunction to take this list of images and create the actual montage.
Next, we’ll display the montage to our screen.
Finally, I’ll provide an example of using montages to display images with OpenCV.
To download the source code + example images to this blog post, be sure to use the “Downloads” section below.
Creating a montage with OpenCV
To get started, open up a new file, name it
montage_example.py, and insert the following code:
# import the necessary packages from imutils import build_montages from imutils import paths import argparse import random import cv2
Lines 2-6 import our required Python packages. Notice how
build_montagesis imported from the imutils package.
If you do not have
imutilsinstalled on your system (v0.4.3 as of this writing), then make sure you install/upgrade it via
pip:
$ pip install --upgrade imutils
Note: If you are using Python virtual environments (as all of my OpenCV install tutorials do), make sure you use the
workoncommand to access your virtual environment first and then install/upgrade
imutils.
From there, we can parse our command line arguments:
# import the necessary packages
from imutils import build_montages
from imutils import paths
import argparse
import random
import cv2
# construct the argument parse and parse the arguments
ap = argparse.ArgumentParser()
ap.add_argument("-i", "--images", required=True,
help="path to input directory of images")
ap.add_argument("-s", "--sample", type=int, default=21,
help="# of images to sample")
args = vars(ap.parse_args())
Our script requires one command line argument, followed by a second optional one, each detailed below:
-
--images
: The path to your directory containing the images you want to build a montage out of. -
--samples
: An optional command line argument that specifies the number of images to sample (we default this value to21
total images).
Next, we can use the
--imagespath to randomly select some input images:
# import the necessary packages
from imutils import build_montages
from imutils import paths
import argparse
import random
import cv2
# construct the argument parse and parse the arguments
ap = argparse.ArgumentParser()
ap.add_argument("-i", "--images", required=True,
help="path to input directory of images")
ap.add_argument("-s", "--sample", type=int, default=21,
help="# of images to sample")
args = vars(ap.parse_args())
# grab the paths to the images, then randomly select a sample of
# them
imagePaths = list(paths.list_images(args["images"]))
random.shuffle(imagePaths)
imagePaths = imagePaths[:args["sample"]]
To obtain a listing of all image paths inside the
--imagesdirectory, we make a call to the
list_imagesfunction (Line 18).
For the purpose of this exercise we randomly shuffle the image paths on Line 19, followed by taking a sample of these images to display to our screen (Line 20). The set of
imagePathsreturned by this sampling will be used to build our montage.
For your own applications you likely will not have to bother with randomly shuffling and selecting a set of image paths — you will already have your image paths.
In the context of Brian’s original question, he is looking to display the results of his image search engine.
The results therefore contain his image paths.
Again, keep in mind that we are simply demonstrating how to build a montage with OpenCV — how you actually use this example is entirely up to you.
Given our
imagePaths, we are ready to build the montage:
# import the necessary packages
from imutils import build_montages
from imutils import paths
import argparse
import random
import cv2
# construct the argument parse and parse the arguments
ap = argparse.ArgumentParser()
ap.add_argument("-i", "--images", required=True,
help="path to input directory of images")
ap.add_argument("-s", "--sample", type=int, default=21,
help="# of images to sample")
args = vars(ap.parse_args())
# grab the paths to the images, then randomly select a sample of
# them
imagePaths = list(paths.list_images(args["images"]))
random.shuffle(imagePaths)
imagePaths = imagePaths[:args["sample"]]
# initialize the list of images
images = []
# loop over the list of image paths
for imagePath in imagePaths:
# load the image and update the list of images
image = cv2.imread(imagePath)
images.append(image)
# construct the montages for the images
montages = build_montages(images, (128, 196), (7, 3))
On Line 23 we initialize our list of
images.
We then loop through the
imagePathson Lines 26-29, loading each
imagefrom disk, and then appending the
imageto our
imageslist.
To actually construct the montage, we make a call to the
build_montagesfunction on Line 32 — this is where all of the heavy lifting is done. If you’re curious about the internals of the
build_montagesmethod and what is going on under the hood, be sure to check out the source code implementation on GitHub.
The
build_montagesfunction requires three arguments:
-
image_list
: This parameter is a list of images loaded via OpenCV. In our case, we supply theimages
list built on Lines 26-29. -
image_shape
: A tuple containing the width and height of each image in the montage. Here we indicate that all images in the montage will be resized to 129 x 196. Resizing every image in the montage to a fixed size is a requirement so we can properly allocate memory in the resulting NumPy array. Note: Empty space in the montage will be filled with black pixels. -
montage_shape
: A second tuple, this one specifying the number of columns and rows in the montage. Here we indicate that our montage will have 7 columns (7 images wide) and 3 rows (3 images tall).
The
build_montagesmethod returns a list of montage images in NumPy array format.
If there are more images in the
imageslist than the
montage_shapecan hold, a new montage is created for the extra
images. This process is repeated until all
imageshave been added to a montage. This process is identical to displaying search results over multiple pages.
Our final code block handles displaying the
montagesto our screen:
# import the necessary packages
from imutils import build_montages
from imutils import paths
import argparse
import random
import cv2
# construct the argument parse and parse the arguments
ap = argparse.ArgumentParser()
ap.add_argument("-i", "--images", required=True,
help="path to input directory of images")
ap.add_argument("-s", "--sample", type=int, default=21,
help="# of images to sample")
args = vars(ap.parse_args())
# grab the paths to the images, then randomly select a sample of
# them
imagePaths = list(paths.list_images(args["images"]))
random.shuffle(imagePaths)
imagePaths = imagePaths[:args["sample"]]
# initialize the list of images
images = []
# loop over the list of image paths
for imagePath in imagePaths:
# load the image and update the list of images
image = cv2.imread(imagePath)
images.append(image)
# construct the montages for the images
montages = build_montages(images, (128, 196), (7, 3))
# loop over the montages and display each of them
for montage in montages:
cv2.imshow("Montage", montage)
cv2.waitKey(0)
On Line 35 we loop over each of the
montages(again, similar to displaying N number of (faux) “search results” on a page).
Lines 36 and 37 then display the current
montageto our screen. The
cv2.waitKeycall pauses execution of our script until we select the currently active window and press any key on our keyboard. This will cause the
forloop to advance.
Once we reach the end of the
montageslist, the script exits.
Displaying the Montage
Approximately two years ago I was involved in a computer vision project that required me to build a simple image fashion search engine. To accomplish this, I built a simple web crawler to spider Nordstrom.com and download all the product images and associated meta data.
We are are going to use a tiny sample of this data today when demoing the
build_montagesfunction.
Once you’ve used the “Downloads” section below to download the source code + example images, you can execute the following command to see the results:
$ python montage_example.py --images nordstrom_sample
After executing the script you should see output similar to the following:
Figure 1: Building a montage with OpenCV and Python.
Note: The exact images that you see in the montage will vary from mine since we are randomly sampling from the input directory.
As we can see in Figure 1 above, we have three rows, each row containing seven images. Each image in the montage has been resized to a fixed size of 128 x 196 pixels.
In the context of Brian’s question at the top of this blog post, this montage could be search results from his image search engine algorithm.
As a second example, let’s increase the
--samplesuch that we create multiple montages since all images will not fit in a three row, seven column format:
$ python montage_example.py --images nordstrom_sample --sample 33
Since 3 x 7 = 21, we know that sampling 33 images cannot possibly fit into a 21 image montage.
Luckily for us, the
build_montagesfunction realizes that there are too many images to fit into a single montage and thus creates two montages.
The first montage can be seen below with all 21 spaces in the montage occupied:
Figure 2: The first montage generated with OpenCV is completely filled.
The second montage holds the remaining 12 images that could not fit in the first montage:
Figure 3: The second montage displays images that could not fit in the first montage.
Notice how empty spaces in the montage are filled with black pixels.
Summary
In today’s blog post I demonstrated how to build a montage with OpenCV and Python to visualize a collection of images. This is a handy tool you can use in your own image processing projects, such as in Brian’s image search engine project detailed at the top of this blog post.
I would also like to take a second and give a big shoutout to Kyle Hounslow who contributed the
build_montagesfunction to the imutils package — thanks again Kyle!
In next week’s blog post I’ll demonstrate how to use this montage functionality in an actual application where we sort images in a dataset according to how “colorful” they are.
To be notified when this next blog post goes live, be sure to enter your email address in the form below.
Downloads:
The post Montages with OpenCV appeared first on PyImageSearch.
from PyImageSearch http://ift.tt/2r4gCv6
via IFTTT
"I'm just not picking up the ball" - Orioles slugger Chris Davis, who is in midst of 2-for-26 slump in which he's struck out 14 times (ESPN)
via IFTTT
Russian Hackers Made 'Tainted Leaks' a Thing — Phishing to Propaganda
from The Hacker News http://ift.tt/2r3hSiq
via IFTTT
Sculptuur Berusting, anonymous, c. 1855 - c. 1880
from Google Alert - anonymous http://ift.tt/2rMZM5v
via IFTTT
Beneath Jupiter

Sunday, May 28, 2017
Legislature OKs anonymous reporting for sex assault victims
from Google Alert - anonymous http://ift.tt/2rvKWk4
via IFTTT
No River Too Wide Goddesses Anonymous English Edition Ebook
from Google Alert - anonymous http://ift.tt/2qt1BAl
via IFTTT
(28/05/2017) E7?~ | best way to get anonymous bitcoins
from Google Alert - anonymous http://ift.tt/2rvphIu
via IFTTT
"I think my money went to Brandon Williams" - Dennis Pitta has a theory on what Ravens did with his $2.5 million pay cut (ESPN)
via IFTTT
Permission for anonymous not see auction with page
from Google Alert - anonymous http://ift.tt/2rc2mRB
via IFTTT
ChrisPC Anonymous Proxy Pro v7 download
from Google Alert - anonymous http://ift.tt/2sak5Gz
via IFTTT
[InsideNothing] kenneth liked your post "[FD] [ERPSCAN-16-036] SAP ASE ODATA SERVER - DENIAL OF SERVICE"
|
Source: Gmail -> IFTTT-> Blogger